The US Cyber Command posted a Tweet about an actively exploited Microsoft Outlook vulnerability alert that needs immediate patching. It’s an Outlook vulnerability that can plant malware on IT networks. The cyber security exploit used, CVE-2017-11774 , is a security bug that Microsoft patched in the October 2017 Patch Tuesday. This Outlook issue allows an attacker to bypass cyber security features and execute Arbitrary Commands on targeted computers that are running Windows. We advise you to scan your IT environment and discover all vulnerable devices to patch them.
FireEye issued a report stating that their researchers discovered evidence of hacking groups APT33 and APT34 actively using the Microsoft Outlook exploited vulnerability.
“As organizations expose any email server access to the public internet for its users, those systems become intrusion vectors. FireEye has observed an increase in targeted adversaries challenging and subverting security controls on Exchange and Office365.”
The Microsoft patch removes the legacy ‘home page’ feature, one that most companies are unaware of because of the low usage. This is an indication that many organizations don’t patch their key business software which can indicate the magnitude of the exploit. That’s where Lansweeper comes in, similar to previous months, we’ve created a report which checks if the assets in your network are on the latest Microsoft patch update. This audit is color-coded to give you an easy and quick overview of which assets are already on the latest Windows update, and which ones still need to be patched.
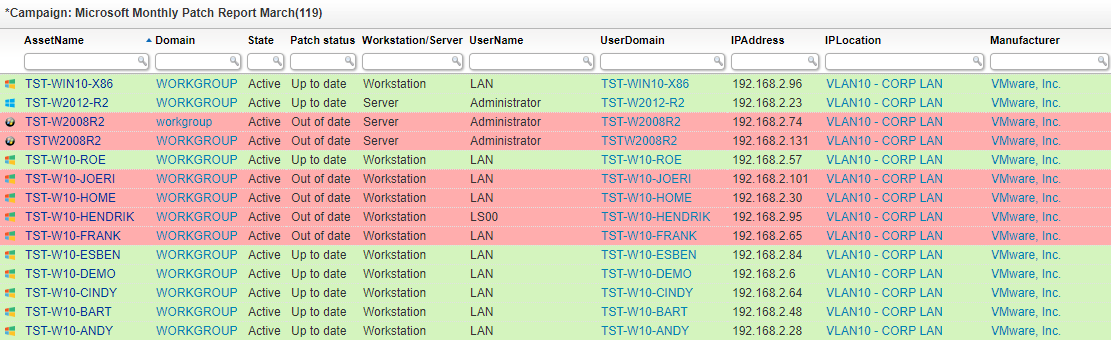
If you haven’t already, start your free trial of Lansweeper to run the Microsoft Patch Tuesday Report. Make sure to subscribe via the form below if you want to receive the latest Microsoft Patch report and audit your network.
Receive the Latest Patch Tuesday Report for FREE Every Month
"*" indicates required fields


