The frequency and severity of cyberattacks continue to escalate, with a 76% increase in high-profile victims over recent years. Ransomware gangs and access brokers are becoming more sophisticated, launching faster and more devastating attacks. In response, 48% of organizations are raising their IT budgets to deal with these growing security concerns.
One of the easiest entry points for attackers is through end-of-life (EOL) products. These products no longer receive security patches or updates, making them vulnerable targets. Worse still, they often don’t support modern security sensors, leaving them unmonitored. Essentially, they are an open door for malicious actors.
End-of-life Products: The Open Door into Your IT Infrastructure
By definition, EOL products are weak links in your network security. They no longer receive any support or updates from their manufacturers. This means they no longer receive any updates, patches, hotfixes, or even technical support. As time passes, these vulnerabilities accumulate, giving attackers ample opportunity to exploit them. The longer these products remain in use, the greater the risk they pose.
Additionally, the more outdated your end-of-life systems become, the more likely it is that they will no longer be compatible with modern security sensors and tools, leaving them unmonitored and thus even more vulnerable.
The most vulnerable products are operating systems and network appliances, which attackers frequently target for exploits. Network appliances are often exposed to external networks and can operate without the need for much user interaction. This makes them more vulnerable to attacks that then go unnoticed for longer. Popular operating systems, such as Windows, macOS, and leading Linux distributions, are prime targets, as compromising these platforms can affect a wide range of users. Once an attacker breaches the operating system, the potential for widespread damage significantly increases.
Take Windows, for example. Its frequent lifecycle changes and multiple versions, each with unique end-of-life dates, make it a challenge for organizations to track and manage. This becomes critical as Windows 10’s final end-of-life date approaches in October 2025, requiring close attention to ensure systems are secure and up to date.
Manage Your EOL Products With Lansweeper
Lansweeper offers a variety of tools to help you identify end-of-life systems and prioritize, track, and manage your mitigation efforts—effectively closing any back doors into your network infrastructure.
Identify
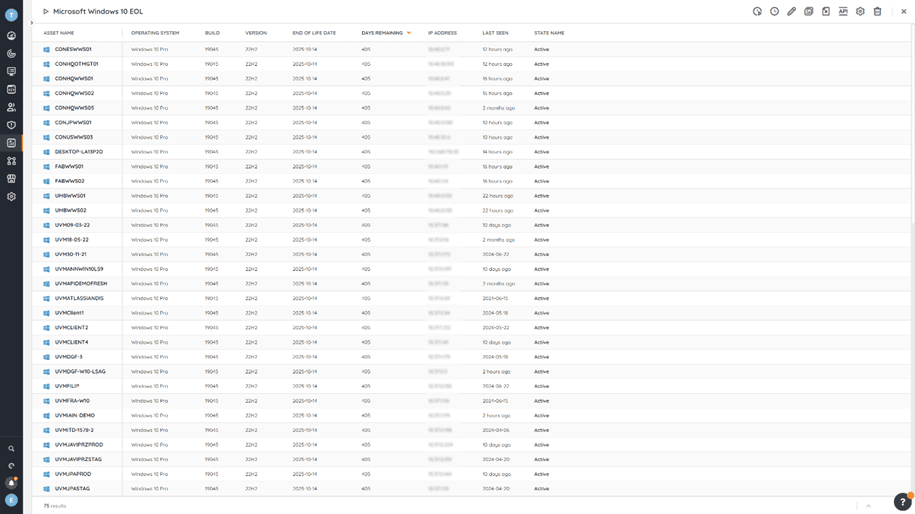
Lansweeper’s robust discovery engine automatically retrieves detailed asset data from all IT, OT, IoT, and Cloud devices within your technology estate. With its comprehensive inventory capabilities, Lansweeper offers unrivaled visibility, allowing you to easily pinpoint systems that have reached end-of-life (EOL). It captures critical information like operating system versions, hardware specifications, installed applications, and user data. Most importantly, this data is automatically enriched with both hardware and operating system lifecycle information and EOL status.
Using Lansweeper’s custom views, you can tailor the information that is displayed to fit your needs. By filtering key fields and critical factors related to EOL status, you can quickly create an intuitive view of your EOL information. For more detailed results, you can use Lansweeper’s report builder to generate customized reports focusing specifically on EOL devices. Additionally, our team regularly releases EOL reports for high-profile systems and software reaching their end-of-life date, which are available in our report library.
These views and reports can be easily shared with stakeholders to support decision-making processes in your organization. This allows you to manage your EOL risks effectively and proactively. This proactive approach ensures that no unsupported systems are overlooked, enabling you to mitigate risks by upgrading, replacing, or securing outdated infrastructure in a timely manner, effectively closing any potential security gaps.
Prioritize
Once you have a clear view of your EOL or nearly EOL systems, you can tailor the information to meet your specific needs and prioritize your most critical assets. You can add fields to highlight EOL status, days until EOL, domain, IP locations, or even custom fields relevant to your environment, and then filter and sort the list to focus on assets that are most vital to your network and operations.
This prioritized view is essential to save and continuously monitor, allowing you to take immediate action as critical systems approach obsolescence. If you want to take it a step further, use Lansweeper’s custom reporting to build targeted reports that zero in on EOL devices. Reports give you even more detailed options, allowing you to use every single data point of devices as a filter or condition.
Once you’ve set up your views and reports, you can share them with relevant stakeholders to guide informed decision-making across your organization. Having reliable EOL asset data ensures that you maintain a structured, prioritized approach, addressing the most pressing risks first.
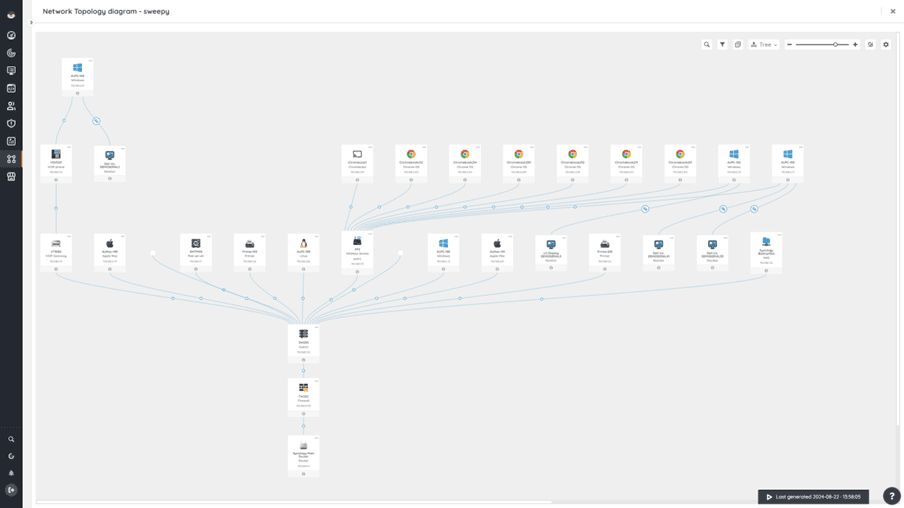
For even better prioritization, visualize your network configurations using Lansweeper’s Diagrams feature. Diagrams give you a visual representation of your IT infrastructure with all its connections and dependencies. This makes it easy to pick out those critical EOL assets that have the potential to have a major impact on your network should they be breached. This perspective lets you pinpoint high-risk areas and assess the potential for lateral movement by an attacker so that you can prioritize your remediation efforts more effectively.
Mitigate
Once you’ve identified which end-of-life (EOL) products need to be prioritized, it’s time to begin your mitigation efforts. These can be executed manually or, to streamline the process, you can leverage one of Lansweeper’s many integrations. For example, integrating Lansweeper with your preferred ITSM or CMDB tools allows you to automatically trigger specific workflows or automations whenever an EOL asset is identified. This seamless integration between systems accelerates the mitigation process, ensuring that vulnerabilities associated with EOL assets are addressed proactively. Not only does this save time, but it also ensures that risks are managed efficiently before they can be exploited by potential threats.
Track
Lansweeper keeps your IT asset inventory up-to-date at all times, meaning that any upgrades and replacements you made for mitigation will automatically be reflected across all EOL dashboards, views, and reports you have created. Integrated systems will also automatically sync with the latest data, providing a cohesive and up-to-date view at all times. This ensures you can effectively track your mitigation progress, and easily share accurate insights with internal stakeholders to keep everyone aligned.
Close the Door Today
End-of-life systems are essentially open doors for cybercriminals and they’re well aware of it. Once systems are too outdated to support modern security tools, vulnerabilities go unpatched, and monitoring becomes impossible. Upgrading, retiring, or replacing these outdated assets promptly is crucial for any effective cybersecurity strategy.
Lansweeper gives you the visibility you need to identify end-of-life systems and helps you prioritize and track mitigation efforts based on reliable IT asset data. By turning the comprehensive depth of its asset inventory into actionable insights through customizable views, reports, and diagrams, Lansweeper enables you to streamline and automate your mitigation efforts for proactive and efficient vulnerability management.