⚡ TL;DR | Go Straight to the Fortinet Vulnerability Audit Report
Fortinet has fixed an authentication bypass vulnerability in FortiOS and FortiProxy that attackers have been using to hijack Fortinet firewalls and breach enterprise networks. This vulnerability is related to a report that cybersecurity company Arctic Wolf released on the 10th of January which reported that Fortinet FortiGate firewalls with Internet-exposed management interfaces have been under attack since mid-November. We have added a new report to Lansweeper that allows you to find vulnerable devices in need of the update.
FortiOS and FortiProxy Vulnerability CVE-2024-55591
Fortinet’s advisory describes the vulnerability tracked as CVE-2024-55591 as “An Authentication Bypass Using an Alternate Path or Channel vulnerability”. It affects FortiOS and FortiProxy and received a critical CVSS score of 9.6. A remote attacker could you use the vulnerability to gain super-admin privileges via by sending crafted requests to the Node.js websocket module.
According the Fortinet, attackers are exploiting this zero-day to create admin or local users on compromised devices and adding them to existing SSL VPN user groups or to new ones they also add. Attackers can also add or change firewall policies or use the above mentioned local users they added to log in to the SSL VPN to get a tunnel to the internal network.
This vulnerability seems to be related to report released by cybersecurity company Arctic Wolf on the 10th of January that reports matching indicators of compromise and which says that Fortinet FortiGate firewalls with Internet-exposed management interfaces have been under attack since mid-November. Mostly likely CVE-2024-55591 has been the initial access vector in these attacks.
Update Vulnerable Fortinet Installations
Fortinet has released updates for the affected FortiOS and FortiProxy versions. Users are advised to update vulnerable instances to the latest version as soon as possible.
| Product and Version | Affected Version | Solution |
| FortiOS 7.6 | Not affected | Not Applicable |
| FortiOS 7.4 | Not affected | Not Applicable |
| FortiOS 7.2 | Not affected | Not Applicable |
| FortiOS 7.0 | 7.0.0 through 7.0.16 | Upgrade to 7.0.17 or above |
| FortiOS 6.4 | Not affected | Not Applicable |
| FortiProxy 7.6 | Not affected | Not Applicable |
| FortiProxy 7.4 | Not affected | Not Applicable |
| FortiProxy 7.2 | 7.2.0 through 7.2.12 | Upgrade to 7.2.13 or above |
| FortiProxy 7.0 | 7.0.0 through 7.0.19 | Upgrade to 7.0.20 or above |
| FortiProxy 2.0 | Not affected | Not Applicable |
Fortinet’s advisory also offered a possible workaround by disabling the HTTP/HTTPS administrative interface or by limiting what IP addresses can reach the administrative interface via local-in policies. You can find detailed instructions in the advisory
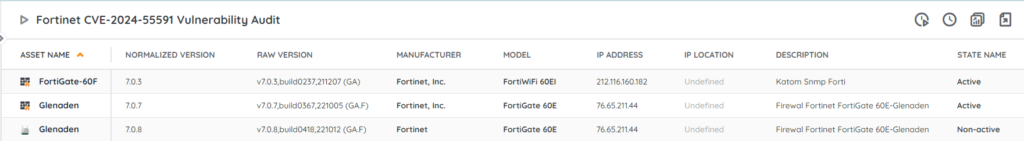
Discover Vulnerable Fortinet Installs
Our team has added a new reports to Lansweeper to help you locate vulnerable instances of FortiOS and FortiProxy. This will give you a list of instances of Fortinet products and their versions, so you can more easily check if they are all up to date. You can get the reports via the link below.