Achieve CIS Compliance with Lansweeper
- Gain Complete Visibility of your IT Asset Inventory with Lansweeper
- The First Step in Protecting Anything is Knowing What You Have
When companies are unsure how to demonstrate their cybersecurity efforts, many turn to ISO27001 and ISO27002. While these frameworks are great for showing compliance, they aren’t as effective for prioritizing, measuring, and implementing practical IT security initiatives. For this, a consensus-based framework like the CIS 18 Critical Security Controls® is ideal.
The CIS Controls® provide detailed, practical, and prioritized advice on implementing cybersecurity measures. They offer clear instructions on what actions to take, how to measure progress, prioritize efforts, and audit your cybersecurity posture.
In this article, we’ll explore the advantages of using CIS Controls, the common hurdles organizations might face, and best practices for successful implementation. Additionally, we’ll discuss how Lansweeper can aid in this process by providing essential tools for asset management and vulnerability assessment.
What are the CIS Controls?
Center for Internet Security (CIS) Controls are a set of recommended actions and best practices designed to boost your organization’s cybersecurity. These controls are part of a framework created to protect systems and data from cyber threats.
Developed by a global community of cybersecurity experts, CIS Controls are regularly updated to tackle the latest threats and tech advancements.
CIS Controls are split into three categories:
- Basic Controls: These are the must-do actions for any organization to ensure a basic level of cybersecurity. They cover things like keeping track of hardware and software assets, managing vulnerabilities continuously, and controlling the use of admin privileges.
- Foundational Controls: These add more layers of security on top of the basics. They include protections for email and web browsers, defenses against malware, and secure configurations for hardware and software.
- Organizational Controls: These focus on the bigger picture of CIS cybersecurity controls within the organization. They cover incident response and management, penetration testing, and security awareness training programs.
CIS Controls v8, developed by the Center for Internet Security, is the latest version of prioritized cybersecurity best practices aimed at improving organizational security. This streamlined version consolidates 20 controls into 18, making them easier to implement and more relevant to current technology environments, including cloud and mobile. Designed to integrate with other cybersecurity frameworks like NIST, CIS Controls v8 provides actionable guidelines to manage and reduce cybersecurity risks effectively.
What Is the Main Purpose of CIS?
The main purpose of the Center for Internet Security (CIS) is to make the online world safer for everyone. CIS does this by developing best practices, guidelines, and tools to help organizations improve their cybersecurity. They create frameworks like the CIS Controls, which are step-by-step recommendations for securing IT systems and data.
By following these guidelines, organizations can better protect themselves against cyber threats and reduce their overall risk.
What Are the Benefits of Adhering to CIS Controls
Adhering to CIS Controls comes with a bunch of benefits that can really boost your organization’s cybersecurity. Here are some key perks:
- Improved Security: The CIS Controls framework helps to protect your systems and data, and guard against a wide range of cyber threats.
- Risk Reduction: These controls help you identify and address vulnerabilities, reducing the risk of breaches and cyber attacks.
- Prioritization: The CIS Controls list is prioritized, so you know which actions to tackle first for the biggest impact, making your cybersecurity efforts more effective and efficient.
- Compliance Support: Many industry regulations and standards align with CIS Controls, so adhering to them can help you meet compliance requirements more easily.
- Cost Efficiency: By preventing incidents before they happen, you can save on the costs associated with data breaches, downtime, and recovery efforts.
- Increased Trust: Demonstrating a commitment to strong cybersecurity practices can boost trust with customers, partners, and stakeholders.
- Adaptability: CIS Controls are regularly updated to keep up with new threats and technologies, ensuring your security measures stay relevant and effective.
Key Components of CIS Controls
CIS Controls focus on three key aspects of cybersecurity to protect IT environments effectively:
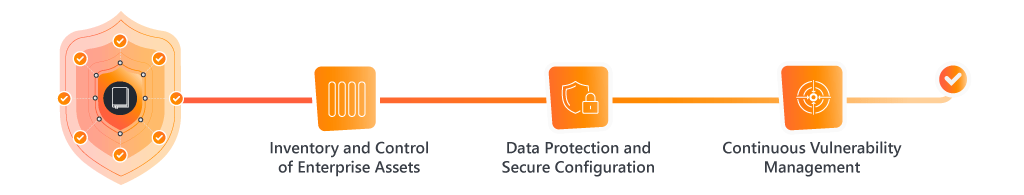
- Inventory and Control of Enterprise Assets: Keep an up-to-date inventory of all hardware and software assets to ensure they are properly managed, patched, and monitored, reducing security risks.
- Data Protection and Secure Configuration: Securely configure systems and encrypt sensitive data to prevent unauthorized access. Regularly review and adjust configurations to maintain a secure environment.
- Continuous Vulnerability Management: Regularly scan for and address vulnerabilities to stay ahead of evolving cyber threats, preventing potential breaches and keeping systems secure.
By focusing on these key components, you can build a strong foundation for your cybersecurity efforts.
Common Challenges in CIS Controls Implementation
Implementing CIS Controls can significantly boost your organization’s cybersecurity, but it’s not without its challenges.
One of the biggest challenges is having enough resources—whether it’s time, money, or personnel. Smaller organizations, in particular, might struggle to allocate the necessary resources to fully implement and maintain all the controls. Prioritizing the most critical controls and gradually expanding your efforts can help manage this issue. Maintaining accurate and up-to-date data about your IT assets is crucial but can be tricky, especially in dynamic environments where assets are constantly changing. Regular audits and automated tools can help, but they require ongoing effort and attention.
Integration with existing IT systems and tools can be complex and time-consuming, often requiring custom integrations or middleware solutions, which can be costly and require specialized knowledge. Ensuring smooth integration without disrupting current workflows is a delicate balancing act. For CIS Controls to be effective, they need buy-in from all stakeholders, not just the IT department. This involves clear communication, adequate training, and demonstrating the value of the controls. Additionally, staying current with evolving cyber threats requires continuous monitoring, regular updates, and staying informed about the latest security trends. By being aware of these challenges, you can better prepare and strategize for successful CIS Controls implementation.
Best Practices for Implementing CIS Controls
Here are some best practices to ensure a smooth and successful implementation:
- Start with a Risk Assessment. Conduct a thorough risk assessment to identify your most critical assets and the biggest threats facing your organization, so you can prioritize which CIS Controls to implement first.
- Engage Key Stakeholders Early. Getting their buy-in early ensures you have the necessary support and resources and helps facilitate smoother adoption across the organization.
- Develop a Clear Implementation Plan. Create a detailed plan that outlines each step of the process, including timelines, responsibilities, and milestones to make implementation more manageable.
- Leverage Automation Tools. Use automation tools to streamline the process and simplify tasks such as asset discovery, vulnerability scanning, and monitoring.
- Provide Comprehensive Training. Foster a culture of security awareness and ensures everyone knows how to implement and adhere to the controls properly.
- Monitor and Measure Effectiveness. Continuously monitor the effectiveness of your CIS Controls and measure their impact on your organization’s security posture. Use metrics and key performance indicators (KPIs) to track progress and identify areas for improvement.
- Document Everything. Keep detailed documentation of your CIS Controls implementation process, including policies, procedures, and configuration settings.
CIS Controls vs. Other Security Frameworks
When choosing a cybersecurity framework, organizations often weigh the CIS Controls list against frameworks like the NIST Cybersecurity Framework. CIS Controls offer a set of specific, actionable best practices that provide detailed guidance on improving security, while the NIST framework offers a broader, more flexible approach with its five core functions: Identify, Protect, Detect, Respond, and Recover, designed to be adaptable across various industries.
CIS standards can complement other standards such as NIST or ISO/IEC 27001, integrating with them to form a comprehensive security strategy. This integration allows organizations to address both strategic and operational aspects of cybersecurity, creating a robust and resilient security posture that caters to immediate and long-term risk management needs.
CIS Controls Resources and Tools
The Center for Internet Security (CIS) website offers a comprehensive range of resources to enhance cybersecurity, including detailed CIS Controls and Benchmarks, the CIS-CAT Pro assessment tool, free implementation guides, CIS Hardened Images for secure cloud deployments, and automated tools for continuous monitoring. It also features the CIS WorkBench for community collaboration, self-assessment tools like CSAT, and an Ambassadors Program for expert guidance.
These resources collectively help organizations improve their cybersecurity posture and comply with CIS standards.
Lansweeper and CIS, Making Implementation and Compliance Easier
Lansweeper supports CIS implementation and compliance with automatic discovery and inventory of all hardware and software assets in your network.
- Using Active Directory scanning and the passive scanning of Asset Radar, Lansweeper continuously detects hardware assets on your network, reporting changes and newly discovered devices. It helps you create a comprehensive inventory of workstations, servers, network devices, IoT devices, mobile devices, cloud assets, and OT devices.
- Lansweeper also automatically discovers software on your hardware assets, including version number, publisher, and install date, helping to remove unwanted software and ensure only authorized software remains. Built-in reports help you categorize software as “Allowed,” “Denied,” or “Neutral.”
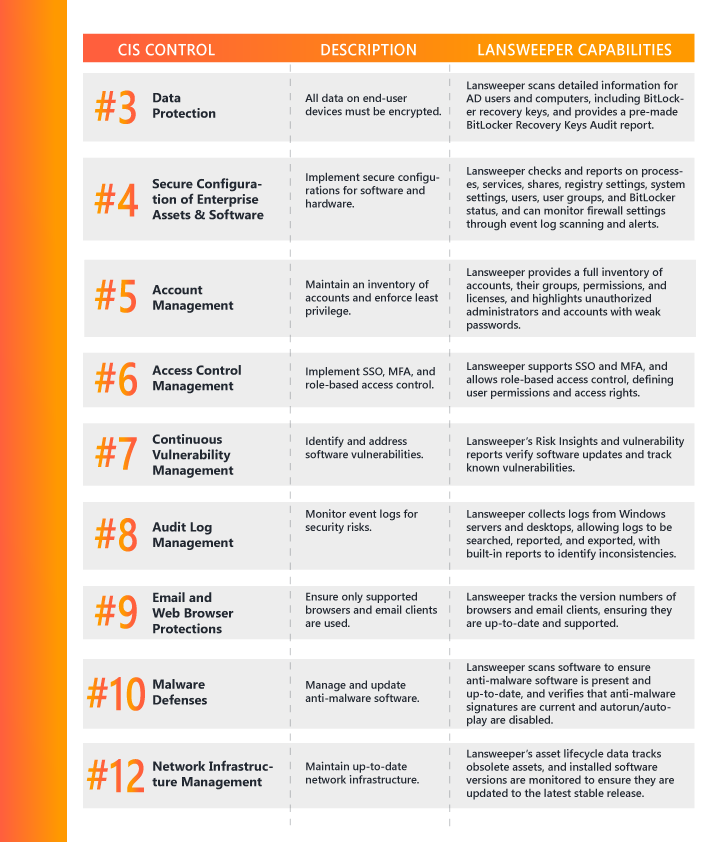
Lansweeper’s discovery and inventory capabilities align with CIS Control 1 (Inventory and Control of Hardware Assets) and CIS Control 2 (Inventory and Control of Software Assets), ensuring you have an accurate and up-to-date picture of your IT environment.
See the table below for more information about how Lansweeper aligns with other CIS Controls:
Take Action for a Stronger Cybersecurity Posture
Implementing CIS Controls is essential for bolstering your organization’s cybersecurity. While it comes with both benefits and challenges, following best practices can ensure a successful implementation. With Lansweeper, you can effectively implement and manage CIS Controls, boosting your cybersecurity posture and minimizing the risk of cyber threats.
To see how Lansweeper can enhance your cybersecurity efforts and ensure your compliance with CIS Controls, book a demo today and start identifying vulnerabilities in your IT environment.


