Take a proactive approach to cybersecurity with CMMC compliance.
Beyond the capability to access real-time data to optimize decision making, the advent of Internet of Things (IoT) technology has enabled organizations to revolutionize their operations through seamless connectivity, unprecedented insights into asset utilization, and the automation of repetitive tasks. Businesses now have access to powerful tools to drive their efficiency, productivity, and innovation to new heights. In this article, we’ll delve into the world of IoT asset tracking, exploring its definition, benefits, implementation strategies and key features.
What is IoT Asset Tracking?
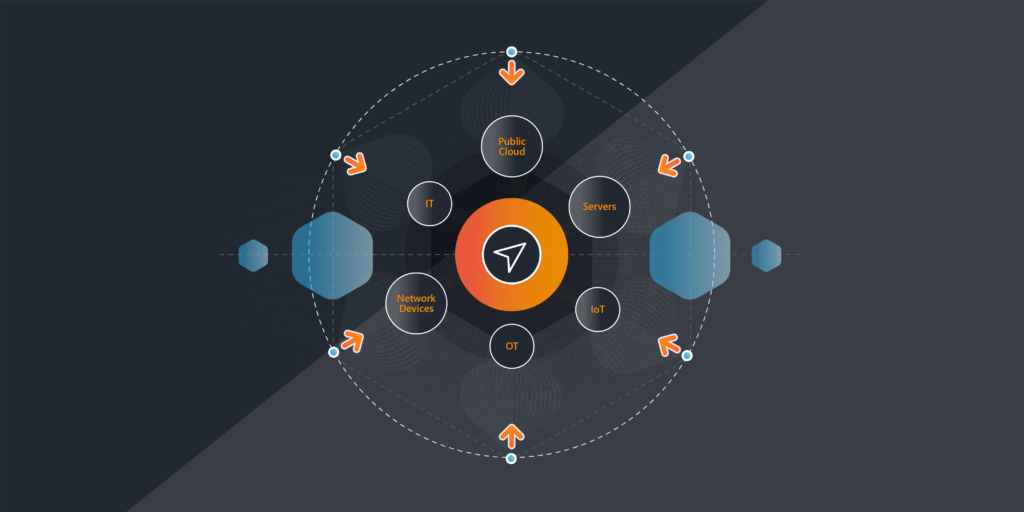
IoT asset tracking involves the use of interconnected devices equipped with sensors and communication capabilities to monitor and manage physical assets. These assets can range from equipment and machinery to inventory and vehicles. For instance, sensors attached to manufacturing equipment can collect data on operational parameters such as temperature, vibration, and energy consumption. This data can then be used to optimize maintenance schedules, prevent breakdowns, and ensure maximum uptime. By leveraging IoT technology, businesses gain real-time visibility into the location, status, and condition of their assets, enabling more efficient operations and improved decision-making.
How IoT Asset Tracking Works
IoT asset tracking systems typically consist of three main components: sensors, connectivity modules, and a centralized software platform. Sensors attached to assets collect data such as location, temperature, humidity, and motion. This data is transmitted wirelessly via connectivity modules, such as Wi-Fi, Bluetooth, or cellular networks, to the software platform, where it is processed, analyzed, and visualized in real-time.
Who Does IoT Asset Tracking Benefit?
Once IoT asset tracking data is fed into the software, various stakeholders across different departments and levels of the organization can leverage it to make informed decisions and optimize operations. Here’s how different users may utilize IoT asset tracking data:
Operations Managers: Operations managers utilize IoT asset tracking data to monitor the performance and utilization of assets. They can track asset movement, identify bottlenecks, and optimize workflows to improve operational efficiency.
Maintenance Teams: Maintenance teams rely on IoT asset tracking data to schedule preventive maintenance tasks and address equipment failures proactively.
Supply Chain Managers: Supply chain managers leverage IoT asset tracking data to monitor the movement and location of inventory and shipments throughout the supply chain.
Finance and Procurement Teams: Finance and procurement teams use IoT asset tracking data to track asset depreciation, monitor asset lifecycle costs, and optimize procurement decisions.
Executive Leadership: Executive leadership relies on IoT asset tracking data to gain insights into overall operational performance, identify strategic opportunities, and make data-driven decisions.
Implementing an IoT Asset Tracking System
Successfully implementing an IoT asset tracking system requires careful planning and consideration. Key steps include choosing the right IoT asset tracking solution based on business requirements and objectives, integrating the solution with existing systems and infrastructure to ensure seamless operation, and following best practices for deployment, configuration, and maintenance to maximize effectiveness and minimize risks.
How To Choose the Best IoT Asset Discovery Platform for Your Business
We’ve created a checklist of features that cybersecurity experts should consider when choosing the right IoT asset discovery platform for their organization.
Security Features:
- Does the platform offer robust security features to protect against cyber threats, such as encryption, authentication mechanisms, and secure communication protocols?
- Are there built-in security controls to prevent unauthorized access, tampering, or manipulation of IoT devices and data?
Compliance Requirements:
- Does the platform comply with industry-specific regulations and standards, such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), or PCI DSS (Payment Card Industry Data Security Standard)?
- Can the platform support compliance audits and provide evidence of regulatory compliance?
Data Privacy:
- Does the platform ensure the privacy and confidentiality of sensitive data collected from IoT devices, such as personally identifiable information (PII) or proprietary business information?
- Are there privacy-enhancing features, such as data anonymization or pseudonymization, to minimize the risk of data exposure?
Integration Capabilities:
- Is the platform compatible with existing cybersecurity tools and systems, such as SIEM (Security Information and Event Management) solutions, firewalls, and intrusion detection/prevention systems?
- Can the platform integrate with other IT infrastructure components, such as network devices, servers, and cloud services, to provide comprehensive visibility and control?
Scalability and Flexibility:
- Is the platform scalable to accommodate the growing number of IoT devices and data volumes over time?
- Does the platform support heterogeneous IoT environments, including diverse device types, protocols, and communication technologies?
Real-time Monitoring and Alerting:
- Does the platform provide real-time monitoring and alerting capabilities to detect abnormal behavior, security incidents, or policy violations?
- Can the platform generate actionable insights and notifications to enable timely response and remediation of security threats?
Threat Intelligence Integration:
- Does the platform integrate with external threat intelligence sources to enhance threat detection and response capabilities?
- Can the platform leverage threat intelligence feeds to identify known attack patterns, vulnerabilities, and indicators of compromise (IOCs)?
Cost-effectiveness:
- Is the platform cost-effective in terms of initial deployment costs, ongoing maintenance expenses, and total cost of ownership (TCO)?
- Are there flexible pricing models, such as subscription-based or pay-per-use pricing, to align with the organization’s budget and requirements?
User Experience and Usability:
- Is the platform user-friendly and intuitive, with a well-designed interface and workflow?
- Can cybersecurity experts easily navigate the platform, configure security policies, and generate reports without extensive training or specialized expertise?
By following this checklist, cybersecurity experts can evaluate different IoT discovery platforms and select the one that best meets their business requirements, security needs, and compliance obligations.
Still not sure if you can make the best IoT asset discovery platform selection for your business? We can help. Our team of experts is here to guide you through the implementation process and help you unlock the full potential of IoT technology for asset tracking. Contact us to request a demo and discover how our solutions can transform your business.
Don’t wait any longer – take the first step towards a more efficient and secure future with IoT asset tracking.