In our previous blog, How good is your end-to-end Network Asset Inventory, we noted that industrial OT/ICS networks and industrial assets are often poorly understood by the corporate IT and cybersecurity managers who are responsible for securing them. Often, the OT side of the enterprise is like a black box to IT personnel because they are unable to see a sizable portion of the industrial assets and they are often discouraged from getting into the OT network to find out. “Traditional approaches” to network scanning can be disastrous in OT/ICS environments, as some assets can be very sensitive these “active” methods. OT is a whole different world from IT. In this blog, we’re going to open the OT black box and explain what’s inside.
Handle with care – OT Assets can be rather sensitive
Network scanning in operational or production environments can sometimes have unintended consequences, such as system malfunction or physical damage to equipment. OT/ICS systems are designed to operate in real-time, and any disruption to the system can cause a cascade of failures, leading to production downtime or even physical damage to equipment. In addition, a network scan can cause excessive traffic on the network, thus disrupting the normal functioning of the system. By far, the safest way to discover OT assets, is to communicate with them in their native protocol, and within the tempo boundaries that the asset knows and expects.
The OT/ICS world view
Generally, the IT cybersecurity view focuses on protecting the company’s intellectual property, information systems, customer data, and the like – confidentiality, Integrity, and availability are the guiding principles. The OT view is quite different. It is not a matter of right or wrong; rather, it is an objective approach to identifying inherent cyber risk in relation to the business’s risk appetite.
OT systems are used to control and monitor physical processes, such as Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems. These systems can include sensors, Programmable Logic Controllers (PLCs), and other devices that interact with physical equipment. For engineers and OT cybersecurity practitioners, the focus is on the reliability, productivity, and safety of these systems and their immediate environments. The approach is very much an engineering methodology.
Mini crash-course on OT – for IT folks
OT/ICS networks constitute a highly specialized environment, with dedicated assets (PLC, RTU, sensor, HMI, etc.) and dedicated languages (protocol) and that are critical to industrial processes and production. The integrity and continuity of these operational technologies must be protected against any and all threats that could disrupt industrial processes and cause downtime.
The “Purdue Model” diagram below shows the different levels in a typical OT network environment. Levels 0-3 of the Purdue Model comprise the “OT/ICS” technology in the operational/production environment, while Levels 4-5 are considered “enterprise” or generic IT.
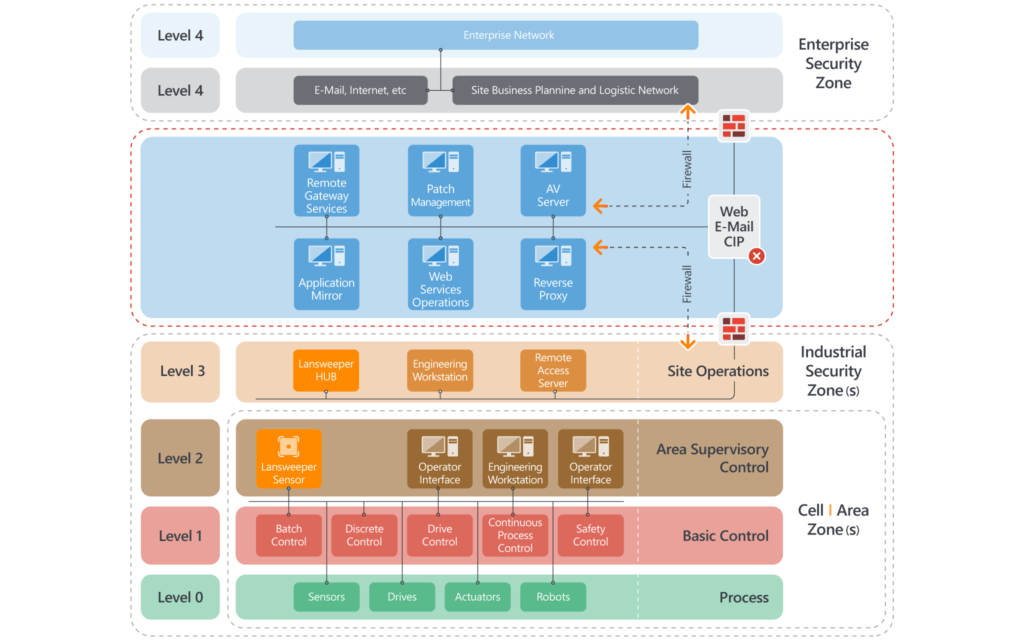
At “ground level” (Level 0) in a manufacturing facility, a wind farm, an electricity transmission grid, a water treatment plant, etc. numerous physical assets are deployed throughout the end-to-end industrial process. This level is where the physical equipment that defines the actual physical processes is found.
Each physical asset has dedicated instruments that detect and report its real-time status, conditions, and behavior to real-time controllers at Level 1. At this level, one can find basic control devices such as sensors, pumps, and actuators, which sense and manipulate physical processes to drive efficiencies. Typical OT environments may deploy hundreds or even thousands of sensors and controllers.
At Level 2, HMI and SCADA systems provide graphical user interfaces and dashboards for operations personnel to visualize, monitor, and control OT assets and the real-time OT processes they perform.
Level 3 is where production workflow is managed on the manufacturing floor, using customized systems for various functions such as batch management, data recording, and operation and plant performance management. These systems also compile lower-level data that is then pushed up to higher-level business systems.
OT assets are specialized and sensitive
The sheer number and variety of these elements alone makes OT asset inventory and management a daunting task. It becomes even more complicated when we consider the proprietary industrial protocols and communication sensitivities of OT assets.
In IT networks and systems, connectivity is taken for granted. IT is designed for digital data communications and is built around standard protocols. In contrast, OT systems, especially older ones, are not designed for inter-connectability. They focus on specialized physical devices, processes and outcomes and communicate via closed protocols. In fact, older OT/ICS control systems might not even be networked beyond serial connections, which makes it very hard for them to share information or to be discovered by a network scan.
Even if the OT assets are networked and the enterprise is using centralized OT/ICS control systems, you can’t just point a commercially available network asset scanner at an OT environment. Doing so could saturate the network, invertedly crash a critical asset, such as a PLC or have other unforeseen adverse impacts. You need to communicate within the boundaries of each proprietary protocol. The asset scanner must be able to discover an asset, itemize that asset, understand the network protocols it’s using, and then communicate back in the format and in the cadence that the asset is expecting.
When Lansweeper decided to extend its leading Asset Inventory and Asset Management solutions into the OT space, we understood very quickly that the ability to analyze industrial protocols and communicate accordingly had to be a key and core competence of Lansweeper OT.
Every industrial environment is different
In the IT domain, the network protocols and devices in one company are pretty much the same as every other company. Ethernet and the IP protocol are pervasive, and while there may be small difference, such as PC v. Mac, but the environments are fairly homogeneous. Not so in the OT world. While industrial operations all use sensors, PLCs, RTUs, HMIs, etc. the assets and processes they monitor and control are highly specialized and differ widely. Even when adopting an OT-centric approach to asset inventory and asset management, the particulars of each industry need to be understood and taken into account. For example, the assets and protocols used in the electricity generation and transmission sector are very different from those used in a manufacturing company.
Context within the operational environment is also incredibly important when assessing the function, OT vulnerabilities, and how each asset may contribute to the overall cyber risk.
Asset discovery, inventory and management tools must be able to accommodate the nuances of each OT asset, protocol and the operational environment. It is important to be able to go to the device (scan it) and bring that information back to an inventory database without affecting any protocol or any process in the OT network. When we consider the complexity, this presents and the sensitivity required, it’s no wonder that IT personnel have shied away (or been kept at arm’s length) from detailed OT asset discovery and inventory. Complexity and context are not the only issues. Cost also plays a big part in the reticence of industrial enterprises to aim for full coverage of OT assets in their inventory database.
While some of the larger OEM vendors may have asset inventory platforms, they can be cost-prohibitive for all but the very largest companies and typically only cover the specific vendor’s assets.
At what cost?
While some OT assets can be very simple, others can be quite complex. When we talk about discovering an OT asset during a network scan, we’re often talking about a composite asset with multiple modules connected via a backplane. Each module is an “asset” in its own right. To manage such an asset, IT managers need a comprehensive and very intuitive view of its hardware, backplane and modules.
Furthermore, the asset inventory database needs to map assets to OT vulnerabilities that are based on hardware, software or firmware versions in the OT space. Unlike IT where vulnerabilities can be quickly identified and patched, many OT vulnerabilities are in old devices that have been there for years and can’t be patched and can’t be pulled out of production. It is important to flag these vulnerabilities, especially if the asset is in a critical process path.
But at what cost?
Big name asset management solutions can achieve this level of granularity and coverage but only at a very high cost to the enterprise – and often for a limited set of vendor assets. Only big organizations with big budgets can absorb such costs for the benefit of OT asset management.
While many small and medium-sized industrial enterprises may share the same complexities as their larger counterparts and be exposed to the same cyber threats, they may lack the resources to invest in cybersecurity. The lack of resources is a significant issue for these companies, as it can make it difficult to maintain an effective security architecture, starting with fundamentals such as IT/OT asset discovery and inventory management.
When we extended our Lansweeper platform into the OT space, we committed to making Lansweeper OT a scalable, modular, and cost-effective asset inventory and management solution that small, medium and large enterprises can afford. Because from a compliance or cyber security or risk management perspective, there isn’t a framework out there that doesn’t start with asset visibility and management. Lansweeper brings a unified approach to IT and OT asset inventory and asset intelligence within easy reach of even the smallest industrial operator.
Taking the complexity out of OT asset inventory
Lansweeper OT is a platform designed to discover inventory in OT environments, including ICS/OT devices (PLC, RTU, DCS), IT/OT (HMI, Engineering workstations, PCs) and IIoT (IP cameras, smart buildings systems, etc.) within the production environment.
For many years, Lansweeper has provided a highly successful tool for small and medium-size enterprises to conduct IT hardware and software asset inventory. Recently, Lansweeper extended this expertise to the OT domain.
Lansweeper OT is uniquely positioned to help corporate IT and cybersecurity managers build a bridge to the “other side” – the OT side of the enterprise. There is no need to settle for limited asset visibility, or to compromise your cybersecurity program due to insufficient OT asset intelligence.
Lansweeper OT understands that OT/ICS environments are different; use proprietary protocols, and require an OT-sensitive approach to asset discovery and management. We leveraged our experience to provide unified IT/OT/IoT asset visibility and management in a way that is easy for IT professionals to use and understand.
Best of all, Lansweeper OT is highly affordable. Small, medium and large industrial enterprises get 100% asset inventory coverage and valuable asset intelligence without breaking the budget.
Learn more about Lansweeper solutions at https://www.lansweeper.com/