
⚡ TL;DR | Go Straight to the June 2024 Patch Tuesday Audit Report
Patch Tuesday is once again upon us. As always, our team has put together the monthly Patch Tuesday Report to help you manage your update progress. The audit report gives you a quick and clear overview of your Windows machines and their patching status. The June 2024 edition of Patch Tuesday brings us 51 new fixes, with 1 rated as critical. We’ve listed the most important changes below.
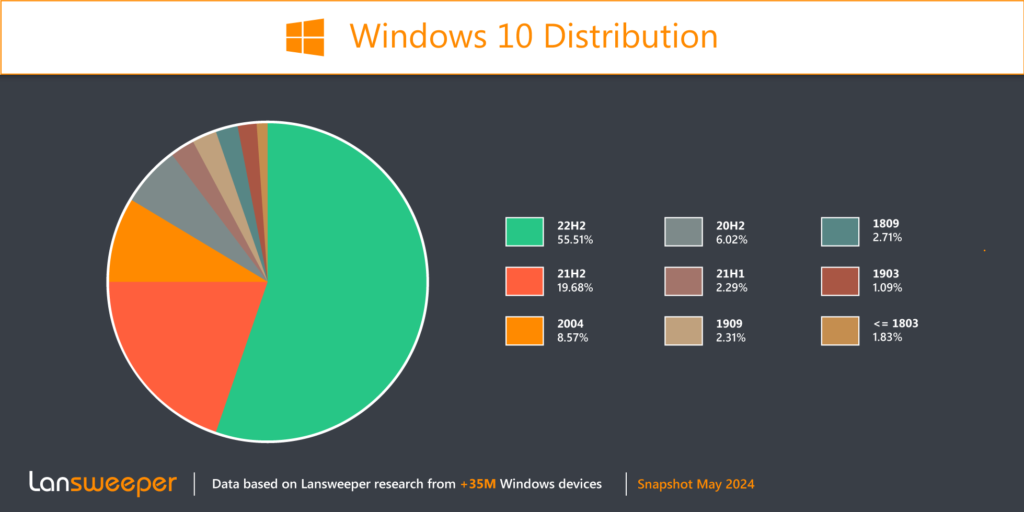
Windows 10 21H2 Last Update
Windows 10 version 21H2 has reached its end-of-life. Today the Enterprise, Education and IoT Enterprise editions go end-of-life which were the last 21H2 supported version. According to our data 44.49% of Windows 10 devices will need to update before next month to remain supported.
Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
The only critical rated vulnerability this month is CVE-2024-30080, a RCE vulnerability with a CVSS base score of 9.8. Additionally, Microsoft lists that this vulnerability is more likely to be exploited so its best you update as soon as possible.
In order to exploit the vulnerability Microsoft shared the following:
The Windows message queuing service, which is a Windows component, needs to be enabled for a system to be exploitable by this vulnerability. This feature can be added via the Control Panel.
Utilizing Lansweeper you can actually easily discover devices with the Windows message queuing service using our Windows Server MSMQ Server Feature Audit.
Multiple Elevation of Privilege Vulnerabilities
Aside from the one critical vulnerability, no other vulnerabilities really jump out. All the remaining vulnerabilities listed as being more likely to be exploited are EoP vulnerabilities in various Windows components.
All 10 vulnerabilities range between a CVSS base score of 7 and 7.8 and don’t really have much additional information aside from potential access attackers can gain from exploitation, but no information about how exploitation would occur.
- CVE-2024-30082
- CVE-2024-35250
- CVE-2024-30084
- CVE-2024-30085
- CVE-2024-30086
- CVE-2024-30087
- CVE-2024-30088
- CVE-2024-30089
- CVE-2024-30091
- CVE-2024-30099
Run the Patch Tuesday June 2024 Audit
To help manage your update progress, we’ve created the Patch Tuesday Audit that checks if the assets in your network are on the latest patch updates. The report has been color-coded to see which machines are up-to-date and which ones still need to be updated. As always, system administrators are urged to update their environment as soon as possible to ensure all endpoints are secured.
The Lansweeper Patch Tuesday report is automatically added to your Lansweeper Site. Lansweeper Sites is included in all our licenses without any additional cost and allows you to federate all your installations into one single view so all you need to do is look at one report, automatically added every patch Tuesday!
Patch Tuesday June 2024 CVE Codes & Titles
| CVE Number | CVE Title |
| CVE-2024-30069 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-30070 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30072 | Microsoft Event Trace Log File Parsing Remote Code Execution Vulnerability |
| CVE-2024-30074 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30075 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30076 | Windows Container Manager Service Elevation of Privilege Vulnerability |
| CVE-2024-30077 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-30078 | Windows Wi-Fi Driver Remote Code Execution Vulnerability |
| CVE-2024-35255 | Azure Identity Libraries and Microsoft Authentication Library Elevation of Privilege Vulnerability |
| CVE-2023-50868 | MITRE: CVE-2023-50868 NSEC3 closest encloser proof can exhaust CPU |
| CVE-2024-29187 | GitHub: CVE-2024-29187 WiX Burn-based bundles are vulnerable to binary hijack when run as SYSTEM |
| CVE-2024-29060 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2024-30062 | Windows Standards-Based Storage Management Service Remote Code Execution Vulnerability |
| CVE-2024-30063 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability |
| CVE-2024-30064 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30065 | Windows Themes Denial of Service Vulnerability |
| CVE-2024-30066 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-30067 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-30068 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30083 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2024-30090 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30093 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-30094 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30095 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30096 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2024-30097 | Microsoft Speech Application Programming Interface (SAPI) Remote Code Execution Vulnerability |
| CVE-2024-30100 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2024-30101 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30102 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30103 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-30104 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-35248 | Microsoft Dynamics 365 Business Central Elevation of Privilege Vulnerability |
| CVE-2024-35249 | Microsoft Dynamics 365 Business Central Remote Code Execution Vulnerability |
| CVE-2024-35252 | Azure Storage Movement Client Library Denial of Service Vulnerability |
| CVE-2024-35253 | Microsoft Azure File Sync Elevation of Privilege Vulnerability |
| CVE-2024-35254 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-35263 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability |
| CVE-2024-35265 | Windows Perception Service Elevation of Privilege Vulnerability |
| CVE-2024-37325 | Azure Science Virtual Machine (DSVM) Elevation of Privilege Vulnerability |
| CVE-2024-30052 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-30082 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-35250 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-30084 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-30085 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-30086 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30087 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30088 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30089 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30091 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30099 | Windows Kernel Elevation of Privilege Vulnerability |