⚡ TL;DR | Go Straight to the VMware vCenter Server Vulnerability Audit Report
Broadcom has released an update for VMware vCenter Server addressing 2 new vulnerabilities, one of which is critical. If successfully exploited this heap-overflow vulnerability could allow an attacker to execute remote code via a network packet. We have added a new report to Lansweeper to help you identify any at-risk deployments of vCenter Server.
EDIT: On October 21st, Broadcom released new vCenter patches, as they determined that the patches released on the 17th of September did not fully address CVE-2024-38812. We have updated this article to reflect those new patches.
VMware vCenter Server Vulnerability CVE-2024-38812
The new VMware vCenter Server update includes fixes for 2 vulnerabilities, 1 of which is critical. The vulnerability tracked as CVE-2024-38812 received a critical CVSS score of 9.8. It is a heap-overflow vulnerability in the implementation of the DCERPC protocol. If successfully exploited a malicious actor with network access to vCenter Server could execute remote code by sending a specially crafted network packet. This could compromise confidential data, disrupt systems or even lead to theft or fraud.
The update also fixed a second vulnerability (CVE-2024-38813). This is a privilege escalation vulnerability with a CVSS score of 7.5 and could allow a malicious actor with network access to escalate privileges to root by sending a specially crafted network packet. You can find all the details in Broadcom’s advisory.
Update Vulnerable vCenter Server Deployments
Broadcom has released updates for vCenter Server 7.0 and 8.0, and VMware Cloud Foundation 5.x and 4.x. The updates are available through the usual channels and can also be found on Broadcom’s advisory page. Due to the critical nature of the issue, users are advised to update their deployment as soon as possible. There are no workarounds for these vulnerabilities.
EDIT: On the 22nd of October Broadcom released new patches for vCenter, as those released on the 17th of September did not adequately address CVE-2024-38812. The table below has been updated to reflect those new patches. Additionally, patches for the 8.0 U2 line are now also available.
| VMware Product | Affected version | Fixed version |
| vCenter Server | 8.0 | 8.0 U3b 8.0 U2e |
| vCenter Server | 7.0 | 7.0 U3s |
| VMware Cloud Foundation | 5.x | Async patch to 8.0 U3b |
| VMware Cloud Foundation | 5.1.x | Async patch to 8.0 U2e |
| VMware Cloud Foundation | 4.x | Async patch to 7.0 U3s |
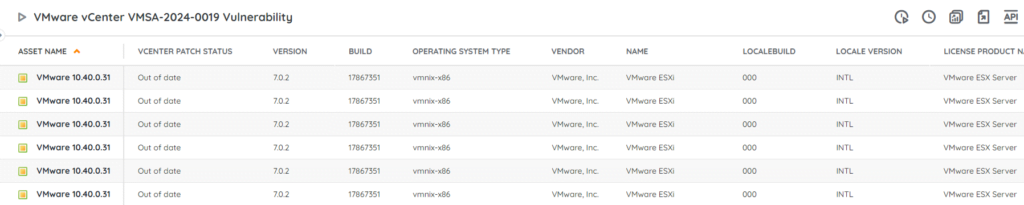
Discover At-Risk vCenter Server Deployments
Our team has created a new vulnerability report that you can use to locate any at-risk vCenter Server deployments in your network. This will give you an actionable list of devices that may be vulnerable and still require you to take action. Do note that this report only lists instances of vCenter Server, and not Cloud Foundation. You can get the report via the link below.