⚡ TL;DR | Go Straight to the Google Chrome 126 Vulnerability Audit Report
On June 11th, prompted version 126 to the stable channel for Windows, Mac and Linux. Along with it comes a massive list of 21 fixes for high and medium-severity vulnerabilities. We have added a new report to Lansweeper to help you locate vulnerable Chrome installations.
Google Chrome 126 Vulnerabilities
In total, this security update addresses 21 vulnerabilities in Chrome. The Center for Internet Security (CIS) lists in their advisory that the risk associated with not updating is high for all sizes of businesses and government entities.
Additionally, CIS adds:
Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
- High CVE-2024-5830: Type Confusion in V8
- High CVE-2024-5831: Use after free in Dawn
- High CVE-2024-5832: Use after free in Dawn
- High CVE-2024-5833: Type Confusion in V8
- High CVE-2024-5834: Inappropriate implementation in Dawn
- High CVE-2024-5835: Heap buffer overflow in Tab Groups
- High CVE-2024-5836: Inappropriate Implementation in DevTools
- High CVE-2024-5837: Type Confusion in V8
- High CVE-2024-5838: Type Confusion in V8
- Medium CVE-2024-5839: Inappropriate Implementation in Memory Allocator
- Medium CVE-2024-5840: Policy Bypass in CORS
- Medium CVE-2024-5841: Use after free in V8
- Medium CVE-2024-5842: Use after free in Browser UI
- Medium CVE-2024-5843: Inappropriate implementation in Downloads
- Medium CVE-2024-5844: Heap buffer overflow in Tab Strip
- Medium CVE-2024-5845: Use after free in Audio
- Medium CVE-2024-5846: Use after free in PDFium
- Medium CVE-2024-5847: Use after free in PDFium
You can find more information about these and other vulnerabilities on Chrome’s release page.
Update Vulnerable Chrome Installations
Chrome has released version 126.0.6478.54 (Linux) and 126.0.6478.56/57( Windows, Mac) that includes all the fixes mentioned above. As always, Google is holding off on releasing further bug details until a majority of users has had a chance to update their installations. That way malicious actors won’t be able to leverage the additional information for further attacks.
Remember to Update Microsoft Edge
Since Microsoft Edge is also a Chromium-based browser, we can expect an Edge security update soon to respond to the same vulnerabilities. You can always check what version your instances of Edge are on using our Edge Version Audit Report. This report will give you an overview of all instances of Microsoft Edge in your environment along with their version number.
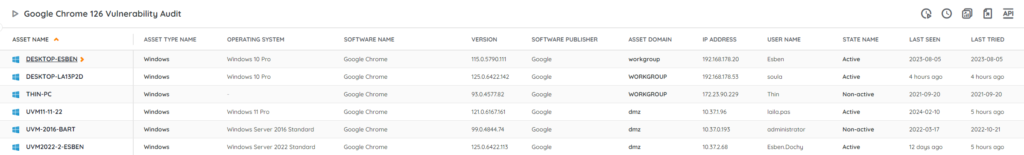
Discover Vulnerable Chrome Installs
We have added an updated audit report to your Lansweeper installations to help you locate any vulnerable instances of Google Chrome in your network. This report will give you an actionable list of installations that haven’t been updated to the fixed version yet. You can get the report via the link below.