⚡ TL;DR | Go Straight to the VMware vCenter Server Vulnerability Audit Report
Vmware has released an update for vCenter Server addressing 2 new vulnerabilities, one of which is critical. If successfully exploited this vulnerability could allow an unauthenticated attacker to execute remote code in low-complexity attacks that don’t require user interaction. We have added a new report to Lansweeper to help you identify any at-risk deployments of vCenter Server.
VMware vCenter Server Vulnerability CVE-2023-34048
The new VMware vCenter Server update includes fixes for 2 vulnerabilities, 1 of which is critical. The vulnerability tracked as CVE-2023-34048 received a critical CVSS score of 9.8. It is an out-of-bounds write vulnerability in the implementation of the DCERPC protocol. If successfully exploited an attacker with network access to vCenter Server could trigger an out-of-bounds write which can in turn lead to remote code execution. This could compromise confidential data and even lead to theft or fraud.
A second vulnerability (CVE-2023-34056) was also fixed. This partial information disclosure vulnerability received a CVSS score of 4.3 and could allow a malicious actor with non-administrative privileges access to unauthorized data. You can find all the details in VMware’s advisory.
Update Vulnerable vCenter Server Deployments
VMware has released updates for vCenter Server 7.0 and 8.0, and VMware Cloud Foundation 5.x and 4.x. The updates are available through the usual channels. The fixed versions are 8.0U2, 8.0U1, 7.0U3o, and KB88287. Due to the critical nature of this vulnerability, they also released patches for a number of end-of-life products. Specifically 6.7U3, 6.5U3, and VCF 3.x have been patched. For the full details, as well as links to the patches and updates, make sure to check the advisory page from VMware.
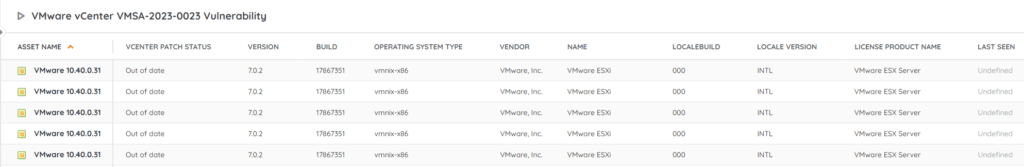
Discover At-Risk vCenter Server Deployments
We have added a new vulnerability report to Lansweeper to help you locate any at-risk vCenter Server deployments in your network. This will give you an actionable list of devices that may be vulnerable and still require you to take action. Do note that this report only lists instances of vCenter Server, and not Cloud Foundation. You can get the report via the link below.