
Critical Security Vulnerabilities fixed in Firefox 72.0.1 and Firefox ESR 68.4.1
Mozilla released Firefox 72.0.1 and Firefox ESR 68.4.1 versions to patch a critical zero-day vulnerability in its browser that is being actively exploited in the wild.
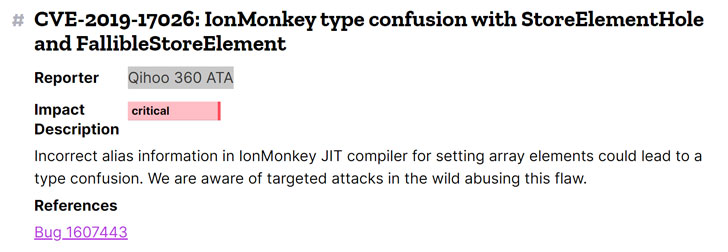
The critical 0-Day vulnerability, tracked as CVE-2019-17026, has been discovered in Mozilla Firefox and Firefox Extended Support Release (ESR), which could allow for arbitrary code execution.
The vulnerability impacts IonMonkey, which is a JavaScript JIT compiler for SpiderMonkey, the main component at Firefox’s core that handles JavaScript operations (Firefox’s JavaScript engine).
The vulnerability was categorized as a „type confusion“, which is a memory bug where a memory input is initially allocated as one type but gets switched to another type during manipulation, causing unexpected consequences to data processing, including the ability to execute code on a vulnerable system.
Systems Affected:
- Firefox versions prior to 72.0.1
- Firefox ESR versions prior to 68.4.1
Get A Report of all Vulnerable Firefox Installations
If you currently have Mozilla Firefox or Firefox ESR deployed on your workstations, it’s pretty critical that you update it at the earliest opportunity to ensure that you don’t fall prey to these vulnerabilities. Our Firefox 72 Vulnerability Audit Report can tell you in no time which devices still have an outdated Firefox version in place and need to be patched.
If you haven’t already, start your 14-day Lansweeper trial and get a list of all vulnerable Firefox versions in no time.