Apple has just released a new version of their latest operating system called „Big Sur“. Along with this version 11.3 comes a slew of improvements and fixes in macOS. The most critical of the bunch is CVE-2021–30657. Discovered by Cedric Owens, this zero-day vulnerability allows attackers to get past Apple’s strict anti-malware measures. For example Shlayer malware is already abusing this flaw due to this macOS vulnerability.
Apple relies on three major security features to prevent malware from infecting a device. The first two are file quarantine combined with Gatekeeper, these warn users about potentially dangerous files and check code-signing information. The third one is Application Notarization, which scans and approves software to ensure it is safe for Apple products. However, the latest zero-day macOS vulnerability is able to bypass all three of these measures, making it very effective.
One of the more well-known Apple malware called „Shlayer“ has already been known to use this vulnerability, Therefore, it is critical that updates are performed as soon as possible to prevent possible infections.
A disruptive malware installer is exploiting this in the wild. There is a new variant of malware that was packaged as a bare-boned, on script based application which means that there is already malware exploiting it. Patrick Wardle explains via a video how the macOS vulnerability is exploited.
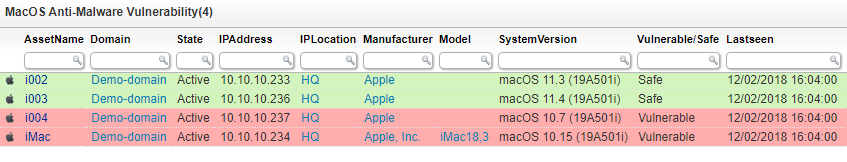
Run the macOS Vulnerability Audit Report
Our security experts have issued a dedicated macOS Audit Report that gives you an overview of all affected devices and their patch status.