⚡ TL;DR | Go Straight to the Fortinet RCE Vulnerability Report
Last week Fortinet released firmware updates for FortiOS and FortiProxy in response to a critical vulnerability in SSL-VPN. Reports are now coming that the vulnerability may already have been exploited, so Fortinet is urging their customers to apply the patches urgently. The bug can lead to remote code execution, which can in turn compromise business-critical data and systems and disrupt operations. We have added a new report to Lansweeper to help you locate at-risk devices.
Fortinet Vulnerability CVE-2023-27997
The vulnerability tracked as CVE-2023-27997 is a heap-based buffer overflow vulnerability in FortiOS and FortiProxy SSL-VPN. It received a critical CVSS score of 9.2 and it seems it has already been exploited in the wild. Successful exploitation of this bug could allow a remote attacker to execute arbitrary code or commands via specifically crafted requests. This could in turn compromise business data and critical systems leading to escalation of privileges and disruptions in operations.
Protect Vulnerable Fortinet Devices
CVE-2023-27997 affects several different versions of FortiOS and FortiProxy. Since the vulnerability has already been exploited you should update the firmware on all devices that have SSL-VPN enabled as soon as possible in order to protect yourself from attacks. Fortinet is working closely with the affected users to monitor the situation. You can find a list of all fixed versions below. You can find the list of all affected versions in Fortinet’s PSIRT advisory.
Fortinet also released a PSIRT blog post to provide more context to this vulnerability. At this moment, they are not linking this particular vulnerability to the recently disclosed Volt Typhoon attacks. However, they are aware of the possibility that threat actors like those behind the Volt Typhoon campaign will continue to exploit unpatched vulnerabilities.
Fixed versions
- FortiOS-6K7K version 7.0.12 or above
- FortiOS-6K7K version 6.4.13 or above
- FortiOS-6K7K version 6.2.15 or above
- FortiOS-6K7K version 6.0.17 or above
- FortiProxy version 7.2.4 or above
- FortiProxy version 7.0.10 or above
- FortiOS version 7.4.0 or above
- FortiOS version 7.2.5 or above
- FortiOS version 7.0.12 or above
- FortiOS version 6.4.13 or above
- FortiOS version 6.2.14 or above
- FortiOS version 6.0.17 or above
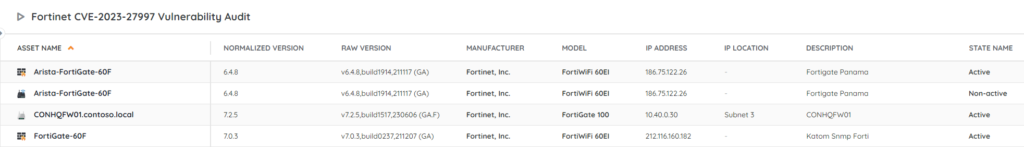
Discover Vulnerable Fortinet Devices
Based on Fortinet’s vulnerability advisory, our team has created a special report to help you find vulnerable Fortinet devices in your network that still need your intervention. The report will give you an actionable list of at-risk devices so that you can take action where needed.