Article 21 of the NIS 2 Directive tells organizations to put effective policies for risk analysis and information system security into place. By systematically identifying weaknesses within an organization’s systems and infrastructure, vulnerability management can mitigate the likelihood and impact of security breaches. By choosing a risk-based approach to vulnerability management, you can prioritize issues that are most likely to impact your organization’s operations seriously.
Lansweeper’s powerful discovery capabilities and risk insights are the perfect tools for risk analysis and vulnerability threat management. They can also help enhance information system security by identifying misconfigurations.
Why Vulnerability Management?
Vulnerability management is a vital part of any cybersecurity strategy. It consists of systematically identifying, assessing, prioritizing, and mitigating vulnerabilities in software, systems, and networks. This can significantly reduce risk exposure and enhance overall security posture.
Proper risk and vulnerability management helps organizations avoid potential threats by proactively identifying weaknesses before attackers can take advantage. Regularly assessing your IT infrastructure for vulnerabilities enables businesses to detect vulnerabilities promptly, reducing the window of opportunity for cyber attackers. Based on the severity of each vulnerability, you can prioritize your remediation efforts and allocate resources accordingly.
Risk-Based Vulnerability Management
When taking a risk-based approach to threat and vulnerability management, you prioritize vulnerabilities based on the level of risk they pose and their potential impact on your organization’s assets, operations, and objectives.
It is important to keep in mind the difference between risk and vulnerability. A vulnerability is a weakness or a flaw in a system, network, application, or process. A malicious actor can compromise sensitive data or systems when exploited. The risk refers to the likelihood that the threat will be exploited and a breach’s potential impact on your organization.
Risk-based vulnerability assessment does not rely only on industry standards (like, for example, a CVSS score) to determine which vulnerabilities are the biggest threat. Instead, it also takes into account how the vulnerability affects your organization. In other words, the risk. For example, suppose a vulnerability with a “severe” rating only affects an isolated asset that doesn’t deal with any sensitive information. In that case, it may not be your priority under risk-based vulnerability management.
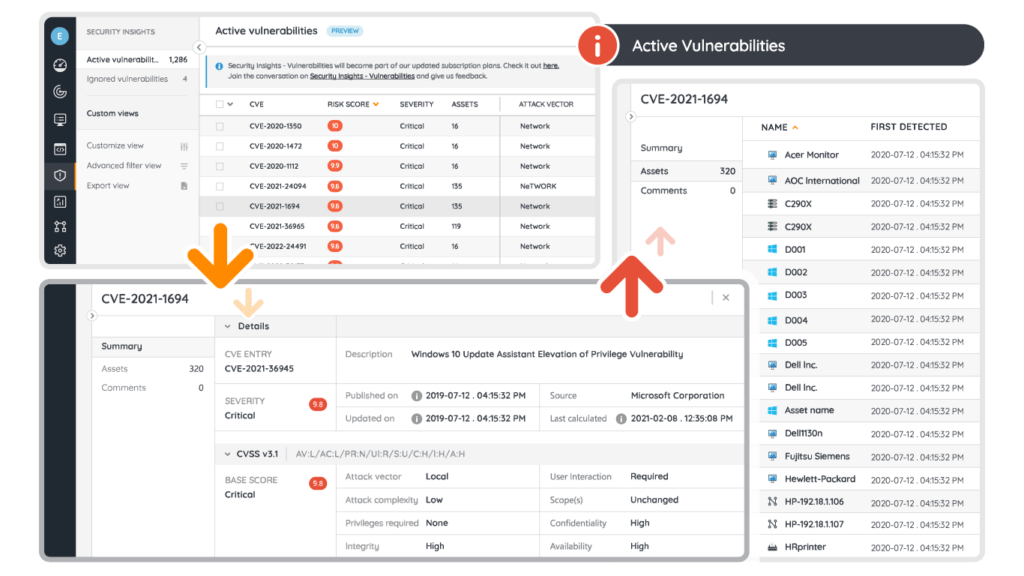
Step-by-Step Vulnerability Management with Lansweeper
Lansweeper’s unrivaled asset discovery capabilities can give you an edge in every step of the vulnerability management process.
- Asset Inventory: As we all know by now, you can’t protect what you don’t know you have. Every vulnerability management strategy should start with a comprehensive inventory of all assets within the organization’s infrastructure. This includes hardware, software, network devices, user information, and data repositories.
- Vulnerability Identification: Identify potential weaknesses in the organization’s systems and software. Lansweeper’s Risk Insights draws information from the NIST and MSRC databases to give you an overview of all vulnerabilities that are affecting your assets.
- Vulnerability Classification: Classify known vulnerabilities based on severity, exploitability, and potential impact on the organization’s assets and operations. The information in Risk Insights will tell you the CVSS score of a vulnerability and which assets it is a threat to. This way you can make an informed decision on which ones are most relevant to you.
- Risk Assessment: Assess the potential impact of identified vulnerabilities on your organization’s critical assets and operations. Consider factors such as the likelihood of exploitation, the value of the asset, and potential consequences. Use Lansweeper’s Diagrams to visualize your network and see what other assets and systems may be impacted by a breach.
- Prioritization: Prioritize vulnerabilities based on the level of risk they pose to your organization. High-risk vulnerabilities that are easy to exploit and have severe consequences should be your priority, followed by medium and low-risk vulnerabilities.
- Remediation and Mitigation: Develop and implement remediation and mitigation strategies to address identified vulnerabilities. This may involve patching systems, updating software, configuring firewalls, segmenting the network, and more.
The Importance of Proper Network Configuration
Network misconfigurations cause some of the most common and most avoidable vulnerabilities. Once a malicious actor has made it into your network, these misconfigurations allow them to move laterally within your network and escalate the exploitation to other machines. And yet, these issues are often overlooked.
It is crucial to close up these loopholes before they become a problem to minimize your attack surface. Making it easy to isolate an issue can significantly reduce the impact of a security breach.
Lansweeper can help you identify and eliminate misconfigurations thanks to the width and depth of asset data Lansweeper discovers. You can easily track down and report missing antivirus installations, lack of encryption, unauthorized local admins, outdated certificates, obsolete software/drivers, and more. It can also help you find unpatched operating systems, applications, and browsers as well as help you audit your firewalls, antivirus, and BitLocker status.
Start Managing Your Vulnerabilities Now
Risk analysis is an excellent place to start, whether you’re looking to become compliant with NIS 2 or any other security framework or simply trying to improve your cybersecurity posture. Vulnerability management is often a critical step in this undertaking. It offers a systematic approach to identifying and mitigating weaknesses in your IT environment and minimizing the risk of security breaches.
Lansweeper’s comprehensive discovery capabilities and risk insights are valuable tools when performing a thorough risk analysis, enhancing information system security, or proactively seeking out and mitigating potential threats. Lansweeper helps you throughout your cybersecurity strategy, from asset inventory to remediation and mitigation.
Addressing network misconfigurations promptly can significantly reduce your attack surface and mitigate the impact of security breaches. Lansweeper’s capabilities extend to identifying and addressing such misconfigurations, enabling you to fortify your defenses and maintain a robust security posture against evolving threats.