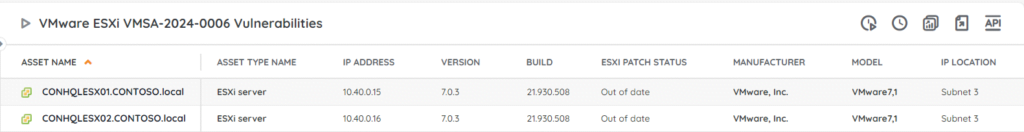
⚡ TL;DR | Go Straight to the VMware VMSA-2024-0006 ESXi Vulnerability Audit Report
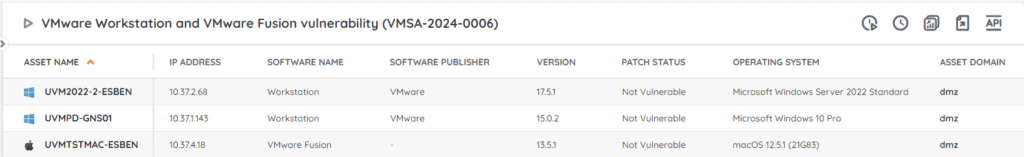
⚡OR| Go Straight to the VMware VMSA-2024-0006 Workstation and Fustion Vulnerability Audit Report
VMware has released security updates for ESXi, Workstation, and Fusion to address a series of sandbox escape vulnerabilities. The update addresses 4 vulnerabilities, all with a critical CVSS score. If successfully exploited the issues could lead to remote code execution. We have added 2 new reports to your Lansweeper installation to help you find potentially vulnerable installs of ESXi, Workstation, and Fusion.
VMware Vulnerabilities CVE-2024-22252, CVE-2024-22253, CVE-2024-22254, and CVE-2024-22255
The new security update from VMware addresses 4 vulnerabilities all having CVSSv3 scores between 7.1 and 9.3.
- CVE-2024-22252 and CVE-2024-22253 are both use-after-free vulnerabilities in the XHCI USB controller in VMware ESXi, Workstation, and Fusion. An attacker with local administrative privileges on a virtual machine could use this issue to execute code as the virtual machine’s VMX process running on the host. On ESXi, it is contained within the VMX sandbox, whereas on Workstation and Fusion, the code execution would be on the machine where Workstation or Fusion is installed.
- CVE-2024-22254 is an out-of-bounds write vulnerability in ESXi. In combination with the vulnerabilities described above, it is considered critical as it could trigger an out-of-bounds write leading to an escape of the sandbox.
- CVE-2024-22255 is an information disclosure vulnerability in the UHCI USB controller on ESXi, Workstation, and Fusion. If exploited it could lead to a memory leak from the vmx process.
Update Vulnerable ESXi, Workstation, and Fusion Installations
The flaws have now been fixed in ESXi 8.0 (update 2b and update 1d) and 7.0 (update 3p), Workstation version 17.5.1, and Fusion 13.5.1 (for MacOS). You are advised to update all installations to the new versions as soon as possible. You can find the full overview on VMware’s advisory page.
| Product | Affected Version | Fixed version |
| ESXi | 8.0 | ESXi80U2sb-23305545 |
| ESXi | 8.0 [2] | ESXi80U1d-23299997 |
| ESXi | 7.0 | ESXi70U3p-23307199 |
| Workstation | 17.x | 17.5.1 |
| Fusion | 13.x | 13.5.1 |
Due to the severity of these issues, patches have also been released for customers with extended support installs of ESXi 6.7, 6.5, and VCF 3.x.
For those who are unable to update their installations immediately, VMware also offers workarounds for CVE-2024-22252, CVE-2024-22253, and CVE-2024-22255, though not for CVE-2024-22254. You can find the details on VMware’s workaround page.
Discover Vulnerable Workstation and Fusion Installs
Our team has put together 2 reports to help you find any vulnerable ESXi, Workstation, and Fusion installations on Windows and Mac. This way you have an actionable list of installs that still need to be updated and you can take action accordingly. You can get to the report via the link below.