NIS2 Readiness Checklist: Ensure Your Compliance with Lansweeper
The Network and Information Systems Directive 2 (NIS2) is a crucial update to the EU’s cybersecurity rules, designed to strengthen the defenses of critical sectors like energy, healthcare, transportation, and banking. Casting a wider net than the original NIS directive, NIS2 pulls in more industries and sets stricter cybersecurity standards. Whether running a medium-sized business or managing large-scale operations, you must take this seriously if you’re in one of the affected sectors.
The clock is ticking — October 17, 2024, is the deadline for compliance – and failing to meet NIS2 requirements could hit you where it hurts the most: your bottom line. Penalties can reach up to €10 million or 2% of your global turnover. And it’s not just about fines – noncompliance could expose your organization to cyberattacks, risking your reputation and ability to operate.
The time to act is now. This Checklist provides all the information and steps you need to achieve NIS2 Compliance.
Quick Summary
Following this checklist will enable you to enhance your organization’s cybersecurity posture and avoid penalties. What you’ll learn in this ebook:
- Understanding NIS2 Compliance
- Steps to Achieve Compliance
- Risk Management Best Practices
- Lansweeper’s Role in Compliance
Why NIS2 Compliance Matters
NIS2 is essential for protecting your organization against the growing and evolving threat of cyberattacks. By mandating more robust cybersecurity measures, the directive ensures that your systems are resilient enough to fend off potential threats and safeguard your critical operations and sensitive data. This level of protection is crucial for avoiding costly breaches and maintaining your customers’ trust.
As you know, a data breach can have devastating consequences, leading to loss of customer confidence; NIS2 helps you mitigate the risks of legal repercussions, financial losses, and a damaged reputation by enforcing best practices in data security. It helps to ensure that sensitive information remains secure and your organization maintains its reputation for reliability and trustworthiness. With NIS2 compliance, you’re not just meeting regulatory requirements – you’re taking proactive steps to secure your business and the valuable data you handle.
5 Steps to Achieve NIS2 Compliance
Step 1: Understand NIS2 Requirements
NIS2 emphasizes the need for organizations to enhance their resilience against cyber threats through better risk management, incident response, and supply chain security. Essential requirements under NIS2 include:
- Enhanced Risk Management
Organizations must develop and implement comprehensive cybersecurity risk management practices, including regular risk assessments and adopting appropriate security measures.
- Incident Response
Entities are required to establish robust incident handling and reporting procedures. This includes reporting significant incidents to relevant authorities within strict timeframes.
- Business Continuity
Organizations must ensure business continuity through effective backup management and disaster recovery plans and maintain operations during and after a cyber incident.
- Supply Chain Security
The directive mandates security measures for third-party suppliers and service providers, ensuring the security of the entire supply chain.
- Security in System Acquisition and Maintenance
NIS2 requires integrating security measures while acquiring, developing, and maintaining network and information systems, focusing on vulnerability management.
- Regular Assessments and Audits
Continuous assessment of the effectiveness of cybersecurity measures is required, alongside regular audits, to ensure compliance.
- Governance and Accountability
The directive places responsibility on senior management to ensure compliance, requiring a clear governance structure and accountability for cybersecurity practices.
Our use case about achieving NIS2 compliance with Lansweeper provides a more detailed explanation of the requirements.
Step 2: Conduct a Risk Assessment
Conducting a risk assessment is crucial in strengthening your organization’s cybersecurity posture, particularly under the requirements of NIS2. This process systematically identifies vulnerabilities within your network and information systems that cyber threats could exploit. By thoroughly analyzing your IT environment, you can pinpoint weaknesses such as outdated software, insufficient access controls, or inadequate encryption.
Once these vulnerabilities are identified, they should be evaluated regarding their potential risks to your operations, data security, and compliance obligations. This assessment highlights areas that require immediate attention and informs the development of a robust risk management strategy, enabling your organization to prioritize security measures that address the most significant threats. Effective risk assessments are key to mitigating risks, protecting sensitive data, and ensuring compliance with NIS2’s stringent cybersecurity standards.
Step 3: Implement Security Measures
Implementing security measures is where your organization begins to actively protect its IT infrastructure against the vulnerabilities and risks identified during the risk assessment. This step involves deploying a comprehensive set of security controls across your network, data, and systems, such as:
- Establishing regular backup procedures and disaster recovery plans in case of an incident.
- Installing and regularly updating antivirus and antimalware software ensures all systems are patched with the latest security updates.
- Implementing strong access control measures such as multi-factor authentication.
- Encrypting sensitive data, both at rest and in transit, to prevent unauthorized access.
- Employing network segmentation to contain potential breaches and limit their impact.
Step 4: Regular Monitoring and Updating
Cyber threats are constantly evolving, and new vulnerabilities can emerge anytime. By regularly monitoring your IT infrastructure, you can quickly detect and respond to suspicious activities, potential breaches, or system anomalies. A proactive approach allows you to address security issues before they escalate into serious incidents.
Additionally, keeping all systems, applications, and security measures up to date via regular updates and patches can help close security gaps that attackers could exploit. Automated discovery tools like Lansweeper can streamline this process, providing detailed insights into your network’s health and alerting you to areas requiring immediate attention.
Step 5: Documentation and Reporting
Keeping detailed records of your compliance efforts helps demonstrate your organization’s adherence to regulatory standards like NIS2 while providing a clear audit trail in case of an audit. Documenting every cybersecurity measure your organization takes, including risk assessments, security implementations, incident response procedures, and ongoing monitoring activities, is essential. Be sure to generate regular reports to track the effectiveness of those measures and also keep track of any changes, updates, or improvements you’ve made over time.
Effective documentation ensures transparency and accountability, making it easier to identify areas for improvement and maintain continuous compliance with NIS2. It also serves as a valuable resource for training, future planning, and demonstrating your organization’s commitment to cybersecurity best practices.
Lansweeper’s Role in NIS2 Compliance
Automated Asset Discovery and Inventory
Lansweeper is critical in helping organizations comply with NIS2’s market-leading, automated asset discovery and inventory capabilities. The solution continuously scans your network to identify and catalog every IT, OT, and IoT technology asset so you can build a comprehensive, up-to-date inventory. This is the first critical step in maintaining security and demonstrating NIS2 compliance. By automating this process, Lansweeper reduces the likelihood of overlooked assets, helping you keep an accurate and up-to-date view of your entire infrastructure.
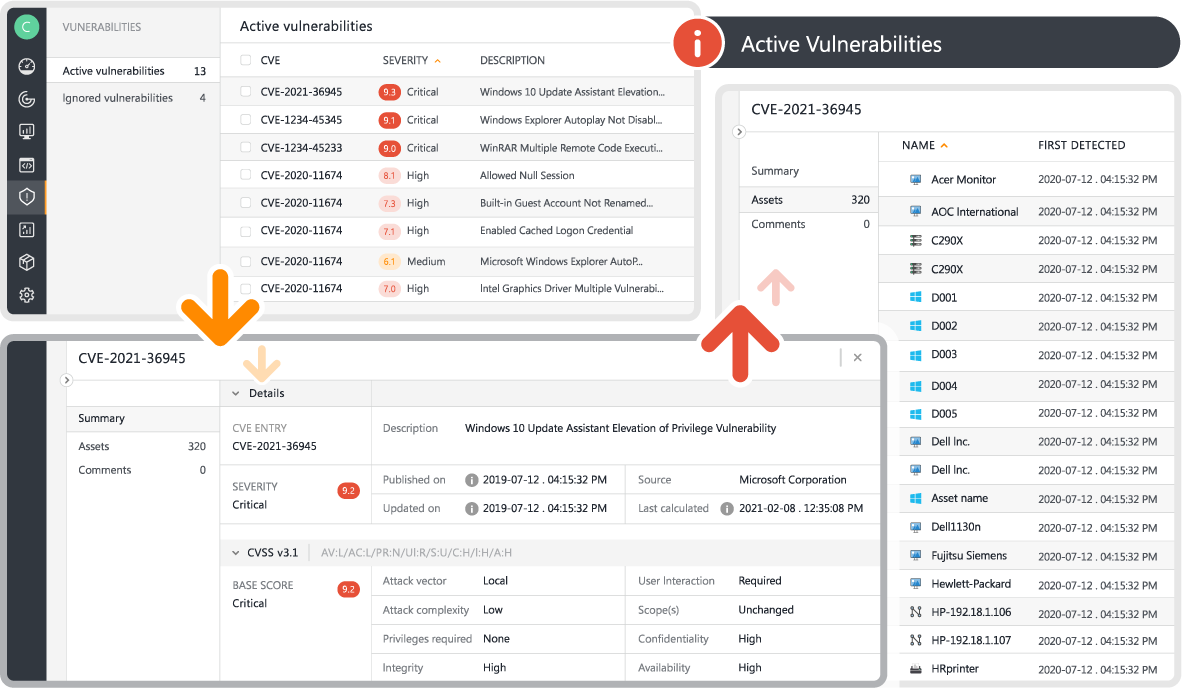
Vulnerability Management
Regarding vulnerability management, Lansweeper provides the tools to identify and address potential security weaknesses within your network. It scans your systems to detect outdated software, missing security patches, and misconfigurations that could expose your organization to cyber threats, providing detailed and actionable Risk Insights. By prioritizing and remediating these vulnerabilities, Lansweeper helps you fortify your IT infrastructure against attacks and meet the stringent security requirements in NIS2.
Integration with Existing Systems
Lansweeper seamlessly integrates with a wide range of compliance and security tools – ITSM, SIEM/SOAR systems, and more – enhancing your overall security posture. These integrations streamline workflows while enabling more comprehensive monitoring and reporting, ensuring all your compliance efforts are coordinated and effective across the board. Lansweeper’s holistic approach simplifies IT governance and makes it easier to comply with the stringent requirements of NIS2.

Readiness Checklist for NIS2 Compliance
1. Understand the Scope and Applicability
☑️ Identify if your organization falls under the essential entities defined by NIS2. Use this guide as a reference.
☑️ Assess which parts of your operations are within the scope of NIS2 based on your sector and size.
2. Understand the Scope and Applicability
☑️ Identify and document all vulnerabilities within your IT infrastructure.
☑️ Assess the potential risks and impacts associated with each vulnerability.
☑️ Develop and implement a risk management strategy prioritizing the most critical risks.
3. Implement Security Measures
☑️ Ensure all IT systems and networks have up-to-date antivirus, anti-malware, and encryption software.
☑️ Implement multi-factor authentication (MFA) for accessing critical systems and data.
☑️ Establish a process to regularly update and patch all software and systems to close security gaps.
4. Establish Incident Response Procedures
☑️ Develop and document a comprehensive incident response plan.
☑️ Define what constitutes a security incident and the appropriate escalation paths.
☑️ Assign roles and responsibilities for incident management to specific personnel or teams.
☑️ Ensure regular training and drills are conducted to test the effectiveness of the incident response plan.
5. Ensure Business Continuity and Crisis Management
☑️ Develop and regularly update backup management and disaster recovery plans.
☑️ Ensure that all critical data is regularly backed up and that backup systems are tested for reliability.
☑️ Implement crisis management procedures to maintain operations during and after a cyber incident.
6. Secure the Supply Chain
☑️ Assess the cybersecurity posture of all third-party suppliers and service providers.
☑️ Require suppliers to comply with your organization’s security policies and NIS2 requirements.
☑️ Establish contracts that clearly define the security responsibilities of each supplier.
7. Regular Monitoring and Updating
☑️ Continuously monitor your IT environment for new vulnerabilities, threats, or anomalies.
☑️ Use automated tools to scan and update your security measures regularly.
☑️ Keep all systems, software, and security tools up-to-date to protect against emerging threats.
8. Implement Cyber Hygiene Practices and Training
☑️ Ensure that all employees receive regular cybersecurity training and are aware of best practices.
☑️ Monitor compliance with basic cyber hygiene practices, such as using strong passwords, regular software updates, and secure handling of sensitive information.
9. Document and Report Compliance Efforts
☑️ Keep detailed records of all cybersecurity policies, risk assessments, and incident response activities.
☑️ Generate regular compliance reports to demonstrate adherence to NIS2 requirements.
☑️ Prepare for audits by ensuring all documentation is complete, accurate, and up-to-date.
10. Review and Improve
☑️ Regularly review and update your cybersecurity policies and procedures to reflect changes in the threat landscape or regulatory requirements.
☑️ Conduct periodic audits and assessments to identify areas for improvement and implement corrective actions.
☑️ Engage in continuous learning to stay informed about new cybersecurity trends, threats, and best practices.
Additional Resources
Your path to NIS2 compliance may vary depending on your industry. Below are three guides specific to Public Sector, Manufacturing, and Finance.
You may also find the following resources valuable:
Success Stories
Several organizations have successfully used Lansweeper to enhance compliance and IT management capabilities. Here are a few notable examples:
Radisson Hotel Group Gains Global Visibility with Lansweeper
Radisson implemented Lansweeper to consolidate IT asset data across all its properties, which led to significant time and cost savings and provided unprecedented insights that optimized IT spending and performance across the enterprise. The comprehensive visibility into their IT assets ensured compliance with various regulatory requirements, enhancing overall cybersecurity and operational efficiency.
“The time and cost savings we realize from using Lansweeper to collect and consolidate all of the IT asset data across all our properties is substantial. At the same time, we gain unprecedented insights that will help us optimize IT spend and performance across the enterprise.”
👉 Read how Radisson eliminated manual data gathering and reporting.
University of York Reduces IT Spending with £300,000 Annually
The University of York used Lansweeper to save approximately £300,000 annually in IT spending. By improving IT procurement, management, and security, the university ensured compliance with regulatory frameworks and significantly enhanced its IT operations.
👉 Discover how Lansweeper helped the University of York save £300,000 annually.
Bekaert Improves Cybersecurity and Slashes Costs with Accurate Asset Data
Bekaert, a leading global company, leveraged Lansweeper to improve cybersecurity and reduce costs by maintaining accurate asset data. This helped them ensure compliance with industry standards and regulations while also streamlining their IT management processes.
👉 Discover how Bekaert slashed costs with accurate asset data.
Your Roadmap to NIS2 Compliance Starts with Lansweeper
Ensuring compliance with NIS2 is not just a regulatory requirement but a crucial step in protecting your organization from growing cyber threats. By following this checklist, you can systematically address the key areas of risk and security, protect your operations, and maintain customer trust.
Lansweeper can help streamline this process and ensure comprehensive coverage. With its powerful tools for asset discovery, vulnerability management, and seamless integration with other security systems, Lansweeper provides the support you need to meet NIS2 standards and enhance your cybersecurity posture.
Get started with Lansweeper today, for free!
Start your 14-day free trial, no credit card required.
TRY NOW