
The frequency and severity of cyberattacks have been steadily increasing year over year. While ransomware remains the favored method for extortion, data theft is also on the rise. Between 2022 and 2023, there was a 76% surge in the number of victims named in data breaches from large, high-value organizations. In response to these growing threats, 48% of organizations report increasing their IT budgets to address mounting security concerns.
One of the most commonly exploited attack vectors in these cyberattacks is network appliances, particularly edge gateway devices. Serving as bridges between internal and external networks, these devices are prime targets for cybercriminals. They are often overlooked or neglected, leading to inadequate management and outdated firmware. In the past year, several critical vulnerabilities—including CVE-2023-20198 (Cisco), CVE-2023-3519 (Citrix), and CVE-2023-46747 (F5)—have been exploited in such edge gateway devices.
Why Network Appliances Are Prime Targets for Cyberattacks
Network appliances such as firewalls, VPNs, and routers function as gateways between internal and external networks, making them highly attractive targets for cybercriminals. Their exposure to external networks, combined with their role in handling sensitive data and enforcing security policies, significantly increases their risk of being exploited. By successfully breaching just one network device an attacker can gain access to a wide range of connected systems.
Unlike endpoint devices, network appliances require minimal user interaction to operate, which presents several risks. They are often less closely monitored and managed and an attack on them may not trigger immediate alarms. Being the first point of contact for incoming and outgoing traffic, they are more vulnerable to outside attacks. Any flaws in their firmware or configuration create an open invitation for malicious actors to exploit.
The most vulnerable of these devices are often obsolete or end-of-life products. Once manufacturers stop providing security updates or patches, the vulnerabilities in these devices remain unaddressed, and their firmware become increasingly outdated. Over time, these devices become even more susceptible to both known and zero-day vulnerabilities. Without adequate visibility and oversight, these unmanaged devices continue to operate on outdated architectures, further exposing them—and the entire network—to cyberattacks.
To effectively protect your network appliances, it’s essential to monitor them as closely as any other device within your network. Ensure they are properly managed, regularly patched, and retired before they become a security risk.
Close the Gaps: Strengthen Your Network Devices with Lansweeper
Lansweeper equips you with the necessary tools to identify, prioritize, mitigate, and track the vulnerabilities threatening your IT environment, ensuring robust cybersecurity across your entire infrastructure.
Identify
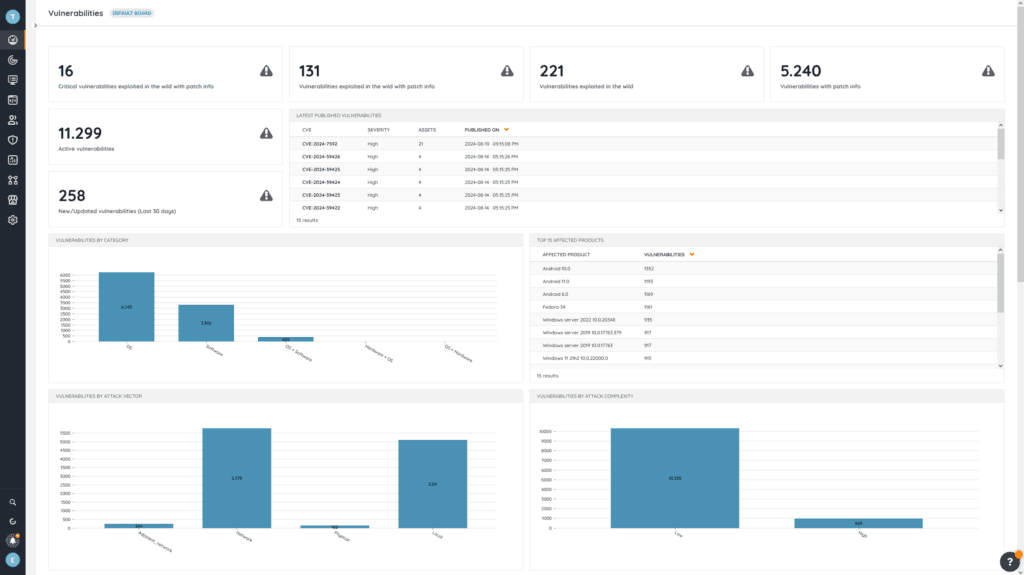
Lansweeper utilizes a combination of active and passive scanning—both agent-based and agentless—to discover and scan every IT, OT, IoT, and cloud device that connects to your network, even briefly. This way, Lansweeper provides you with an always accurate and up-to-date inventory of your entire technology estate, collecting detailed, device-specific information like model, manufacturer, serial number, hardware, and firmware lifecycle as well as a full overview of available network ports, their configuration and of course network devices. Moreover, with custom MIB and OID scanning, Lansweeper retrieves any supported data point for your managed network appliances, providing unprecedented depth in asset detail.
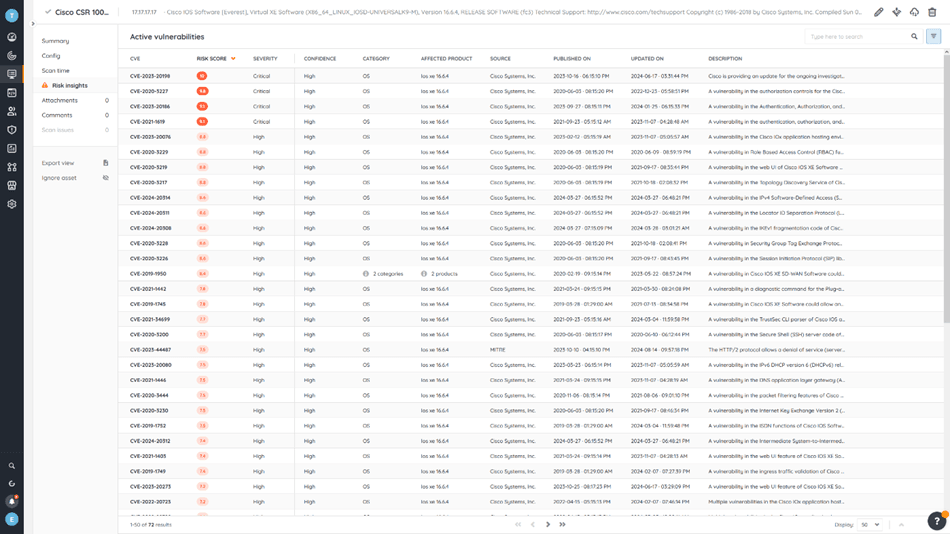
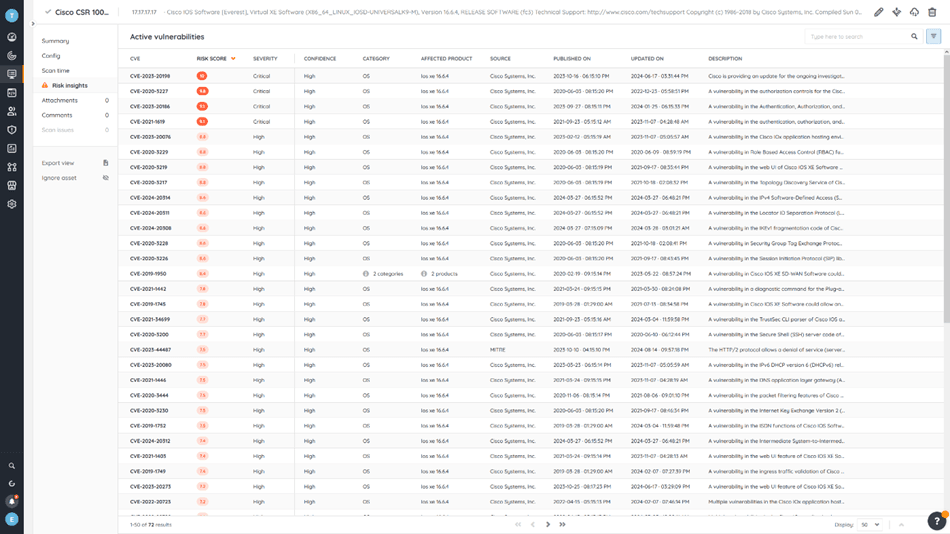
This comprehensive data fuels Lansweeper’s Risk Insights feature. Risk Insights compares your asset data against known vulnerability databases such as VulnCheck, VulDB, CISA, and MS databases to identify potential vulnerabilities in your network infrastructure that attackers could exploit. This results in an actionable list of at-risk devices and their vulnerabilities—like the Cisco vulnerability CVE-2023-20198—allowing you to proactively address threats before they lead to security breaches.
Prioritize
When you explore Lansweeper Risk Insights, you’ll uncover a wealth of information about the vulnerabilities it has detected. This includes essential details such as official references, exploitability, CVSS scores, patch availability, and more. With these detailed insights, you can more precisely evaluate the threat each vulnerability poses to your organization from multiple angles. This allows you to filter out the noise from thousands of vulnerabilities and focus on the most critical ones. You can even leverage Lansweeper’s custom views to further filter the information that matters to you, save it, and share with your team, ensuring alignment in addressing the most urgent security issues.
Another valuable tool for conducting risk assessments is the Diagrams feature. These network diagrams provide a clear visual representation of your IT infrastructure, mapping the connections between your devices. This allows you to quickly grasp the potential impact of vulnerabilities within the broader context of your network. With these diagrams, you can not only identify where vulnerabilities exist but also visualize how an exploit could spread across your network, particularly through lateral movement by attackers.
This holistic approach enables IT teams to prioritize mitigation efforts more effectively, focusing not only on the severity of each vulnerability but also on its potential impact on the entire IT estate.
Mitigate
After identifying which vulnerabilities to prioritize, it’s time to begin mitigation. The Risk Insights that Lansweeper provides include patch information and official references. That way you have your mitigation options at hand and you know what your options are for each identified vulnerability.
In addition, Lansweeper seamlessly integrates with your existing tech stack, allowing you to leverage its comprehensive asset data to supercharge automation, workflows, and tools used in your vulnerability and risk management processes. For instance, once a vulnerability is detected, Lansweeper can automatically trigger specific workflows or automations in your ITSM or CMDB tools, streamlining and accelerating your overall risk management process.
Track
The final, yet equally important step in vulnerability management is tracking your mitigation efforts. This data is crucial to only to keep your stakeholders informed about possible threats and the steps taken to mitigate them, but also to evaluate the outcome and impact of mitigation efforts. Conducting a retrospective analysis of past mitigation strategies can help strengthen and streamline future responses.
With Lansweeper’s continuously updated inventory, any mitigation actions you take are automatically reflected across all dashboards, views, and reports. Additionally, any tools integrated with Lansweeper will receive the updated information seamlessly, ensuring your entire system stays in sync.
Close the Door on Cyber Threats Today
All indicators show that cyberattacks continue to rise in both frequency and severity, with network devices—especially edge gateway devices that serve as bridges between internal and external networks—becoming prime targets for cybercriminals. These devices are often overlooked and under-managed, operating on outdated firmware and architecture, which introduces vulnerabilities that can compromise not just the device itself but your entire network.
Lansweeper empowers you to regain control by discovering all your network devices and utilizing this information to identify vulnerabilities. This allows you to effectively prioritize, execute, and track your mitigation efforts based on reliable, actionable data. With its unmatched depth and breadth in asset visibility, Lansweeper transforms this visibility into actionable risk insights, enabling proactive vulnerability management. This ensures that potential threats are addressed before they can escalate into full-scale breaches.