Imagine coming home after your vacation to discover your house has been ransacked. Someone broke in, stole your valuables, and left your place in shambles. You call the police, and a team rushes over to dust your front door, furniture, and other belongings for fingerprints. Suppose they find anything that doesn’t belong to you or anyone else who lives in your home. In that case, they have substantial evidence to begin their investigation, find and convict the criminals, and hopefully recover your missing goods.
Fingerprints help catch criminals in the physical realm and strengthen security in the digital realm.
In this post, we’ll explain device fingerprinting and how it works. We’ll also explain how device fingerprinting can reduce the risk of a cyber attack against your corporate network by ensuring you have all the data you need to optimize and protect every device across your technology asset estate.
What Is Device Fingerprinting?
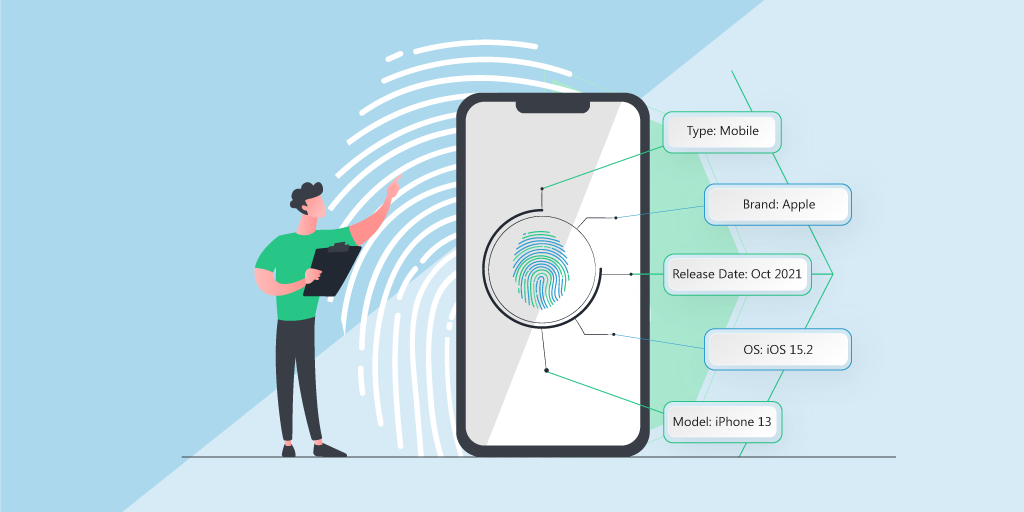
A device fingerprint is a collection of information about the hardware and software of a computing device. A fingerprinting algorithm assimilates the information and creates an identifier for the device. Some of the information these algorithms leverage include:
- IP address
- HTTP request headers
- User-agent string
- Plugins or fonts that the user has installed on their device
- Screen resolution
- Operating system
- Location information and time zone
- VPN and browser information
- Flash data
- Battery information
- And more
Although none of the data collected may be unique to a single device, it’s unlikely that two devices will have the same combination of attributes. Just like an actual fingerprint, a device fingerprint is one-of-a-kind. It can identify a device without cookies or when the client’s IP address is hidden.
Passive vs. Active Device Fingerprinting
There are two types of fingerprinting: active and passive. Malicious software leverages active fingerprinting to send packets to a victim’s host, wait for a reply and analyze the results to launch an attack.
On the other hand, passive fingerprinting is used defensively in cybersecurity software and services to identify and recognize devices. Rather than actively sending packets to a target system, it monitors network traffic data at the gateway or router using HTTP. The HTTP protocol requires clients to send a user agent that contains a description of the client system and is a popular technique for ensuring devices are protected and updated with the latest available OS versions.
How Device Fingerprinting Works
Lansweeper leverages device fingerprinting in its Credential-free Device Recognition (CDR) technology. CDR applies big data, AI, and advanced machine-learning techniques to identify and recognize devices passively and has uniquely identified over 1.2 billion devices (and counting) across various environments. Devices are detected and recognized instantly – even those that only touch the network briefly – and fingerprints are generated, encrypted, and stored in Lansweeper’s database.
Device fingerprinting enables Lansweeper to more accurately determine the asset type of specific devices and add additional information that could previously not be retrieved without credentials. Fingerprints consist of a MAC address and are further enriched with granular data about the manufacturer, model, and OS. During a scan, the fingerprints are sent to the Lansweeper-owned recognition API, which returns more information about the device to be added to the database. Upon the following network scan, all this information is applied to the device, creating a more complete picture of all its unique attributes.
What Are Device Fingerprints Used For?
By embedding device fingerprinting technology in their products, telecom, and cybersecurity providers can enhance the customer experience by enabling users to quickly identify all connected devices – IT, OT, and IoT with a high degree of accuracy. Fingerprints can be used with Zero Trust Network Access (ZTNA) solutions to authenticate users and determine whether a device attempting to access the network is trusted. They can also detect unauthorized access – a mismatch between a user and a device or an unknown device accessing the network could signify a security risk or malicious activity. Other use cases include:
- Identify and isolate rogue devices.
- Troubleshooting performance issues and identifying opportunities to optimize the network.
- Detecting and addressing vulnerabilities such as outdated OSes.
- Push security updates to connected devices.
- Leverage self-service capability for streamlined local network management.
Learn more about Lansweeper device fingerprinting technology here.
Innovate, Scale, and Get to Market Faster
Accelerate your go-to-market by leveraging our embedded technologies.
OEM Products