Across all industries and market sectors, cyber threats are increasing exponentially – and your business is looking to you to prevent an attack. Your main responsibility is to safeguard your IT infrastructure against malicious activity and respond to incidents quickly and efficiently. If an attack gets through, it’s your job to mitigate the impact before too much damage occurs.
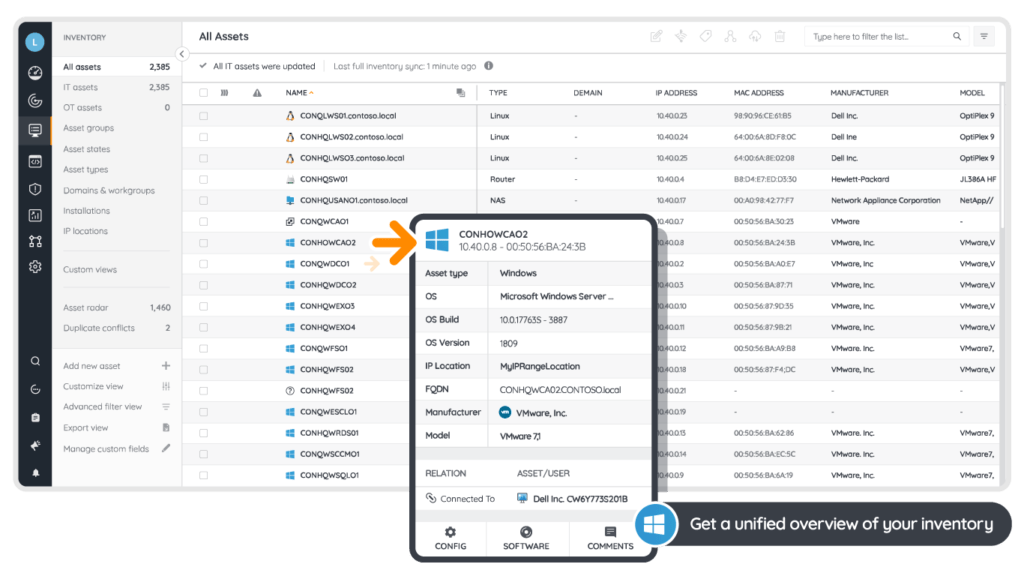
Your ability to anticipate and intercept potential cybersecurity attacks is paramount. This requires enforcing best practices and IT policies consistently and thoroughly, so you can prove compliance in case of an audit or data breach. It’s a tall order, and since you can’t protect what you don’t know you have, maintaining an always accurate IT asset inventory is a top priority.
The pressure is higher than the effort for you to enforce IT processes and best practices for ensuring stability, continuity, and productivity – but you’re short-staffed, and highly skilled security professionals are expensive and hard to come by. To make matters worse, you’re saddled with legacy infrastructure that takes a lot of time and resources to maintain and that are error-prone and incomplete.
While you can access multiple security tools, achieving a consolidated view of the IT infrastructure is a pipedream. Forgotten or missed assets may run outdated software, drivers, or even malware, creating security vulnerabilities that can compromise your data and infrastructure and lead to huge financial losses. How do you get it all under control?
With Lansweeper, we can gather data very quickly and know how to focus our efforts. From an incident response perspective, it helps us reduce the time it takes to respond to incidents so we can contain them faster. Risk is reduced because we are faster and more effective at resolving issues — and that’s invaluable.


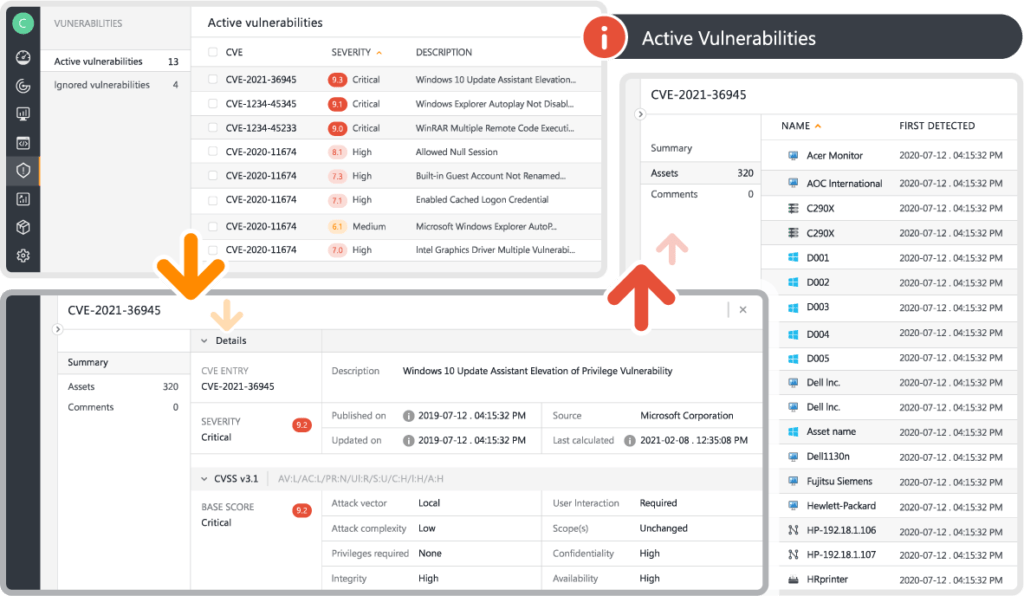
The attack surface encompasses all points of entry that can serve as attack vectors for unauthorized users to gain access to a system for malicious reasons. Cyber Asset Attack Surface Management (CAASM) helps to identify all potentially vulnerable assets before an attacker gets in. Detecting and preventing attacks won’t be possible without complete and accurate technology asset data. Learn how Lansweeper enables CAASM by providing visibility and actionable insights across your Technology Estate in this whitepaper.
Entdecken Sie alle unsere Funktionen, 14 Tage lang kostenlos.