
Managing user privileges is a critical aspect of system administration. PowerShell, a powerful scripting solution for Windows, can significantly streamline this process. In this tutorial, we’ll cover how to retrieve a list of local administrators from computers within an Active Directory (AD) domain using PowerShell.
PowerShell Script Prerequisites
Before executing the script, ensure the following prerequisites are met:
- Domain Administrative Credentials: You need domain administrative privileges to execute the script successfully.
- PowerShell Version: The script is compatible with PowerShell 5.1, which is standard in Windows 10. You can check your PowerShell version by running
$PSVersionTable.PSVersionin PowerShell. - Active Directory Module: This script requires the
ActiveDirectorymodule, typically available on Windows Server with Active Directory role or on Windows client machines through RSAT (Remote Server Administration Tools). - PowerShell Remoting Enabled: The script uses PowerShell remoting to execute commands on remote computers. Ensure PowerShell remoting is enabled on all target computers. This can usually be done with the
Enable-PSRemotingcmdlet. - Network Accessibility: Ensure that the computer where the script is run has network access to all target computers in the AD domain.
- Appropriate Permissions: The user running the script must have permissions to access and execute commands on remote systems. This usually means being part of the Administrators group on the target computers.
- Firewall Configuration: Ensure that any firewalls on both the local and remote systems allow for PowerShell remoting. The required ports (typically 5985 for HTTP and 5986 for HTTPS) should be open.
- TrustedHosts Configuration: If your environment requires it, you may need to configure the
TrustedHostssetting on the computers. This is often necessary in workgroup environments or non-trusted domains. - Execution Policy: The execution policy on the computer running the script should be set to allow the execution of scripts. You can view the current policy with
Get-ExecutionPolicyand change it withSet-ExecutionPolicy, though this should be done with an understanding of the security implications. - Testing Environment: Always first test scripts in a controlled, non-production environment to ensure they function as expected and do not disrupt your network or systems.
To install RSAT, run PowerShell as Administrator and execute the following command:
Add-WindowsFeature RSAT-AD-PowerShell
In some cases, you may need to download RSAT from the Microsoft website or use the „Add a feature“ option in the Settings app in Windows. After installation, ensure that the module is available by running:
Get-Module -ListAvailable -Name ActiveDirectory
If the module is listed, you’re ready to proceed. Open your PowerShell ISE or editor of choice and prepare your script. Here’s a breakdown of the key script sections:
- Variables: The
$folderPath,$outputFileName,$dateStamp,$logFileName,$outputFile, and$logFilevariables are defined at the top of the script. - Retrieve AD Computers: The script gathers all computer objects from AD.
- Local Administrator Retrieval: For each computer, the script collects the names of the local administrators and writes them to the CSV file.
- Final Log: After completing the script, a final log entry is written.
Local Administrators PowerShell Script
Run the script in PowerShell. Ensure you execute it with administrative privileges to avoid permission issues.
Local Administrators PowerShell Script
# Output file and log file paths
$folderPath = "C:\test"
$outputFileName = "groupmembership.csv"
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$logFileName = "log_$dateStamp.txt"
$outputFile = Join-Path -Path $folderPath -ChildPath $outputFileName
$logFile = Join-Path -Path $folderPath -ChildPath $logFileName
# Function to write a log entry
function Write-Log
# Check and create output folder
if (-not (Test-Path -Path $folderPath))
# Initialize the output file without an additional line break
"ComputerName,FQDN,IPAddress,MACAddress,OperatingSystem,LocalAdministrators" | Set-Content $outputFile -Encoding ASCII
# Import the Active Directory module
try catch
# Get all active computers (servers and workstations) from Active Directory
try catch
# Loop through each computer and get details including operating system
foreach ($computer in $computers)
$adminList = $admins -join ", "
$adminList = $adminList.Trim()
$adminList = $adminList -replace '"', '""'
$props = @
return $props
} catch
}
$result = Invoke-Command -ComputerName $computer.DNSHostName -ScriptBlock $scriptBlock -ErrorAction Stop
# Construct the output line with all details
$line = "$($computer.Name.Trim()),$($computer.DNSHostName),$($result.IPAddress),$($result.MACAddress),$($result.OperatingSystem),$($result.Admins)"
Add-Content $outputFile -Value $line -Encoding ASCII
} else
} catch
}
# Final log entry
Write-Log "Script execution completed. Check the output at $outputFile"
Get Local Admins Without Any Scripting
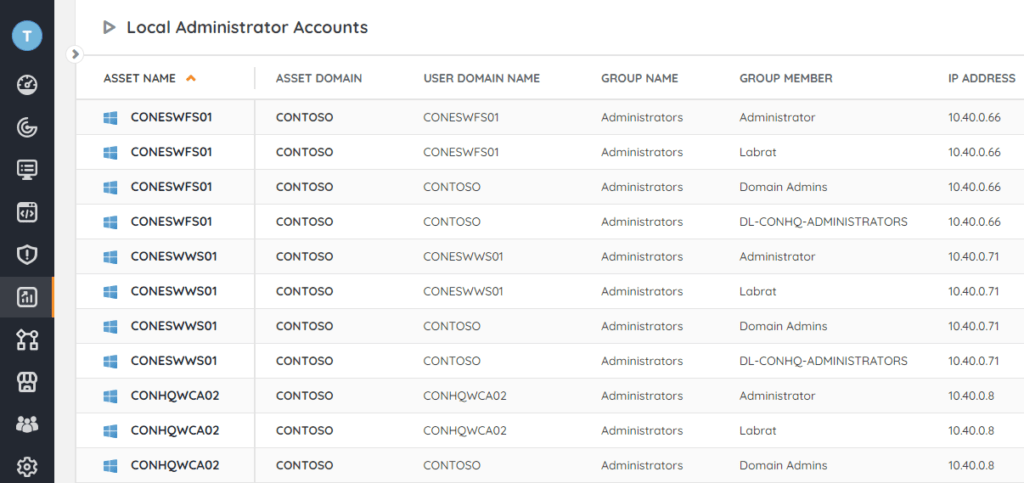
Want to get the above information without all of the pre-requisites and configurations? Lansweeper scans all users from Microsoft Active Directory, Azure Active Directory or Microsoft 365, as well as automatic agent-based or agentless scanning of all devices in your IT envrinoment. This means you can get a quick and complete overview of all AD, AAD, or M365 users, groups, attributes, and device information in seconds. Simply use the default „Local Administrator Accounts“ report to get your complete overview that you can consult at any time.
Unleash Your Asset Management Potential with Lansweeper
Discover every single device in your IT evironment from Servers to OT devices using flexible agent, agentless or passive scanning, utilize extensive third-party integrations to provide your tech stack with an accurate and comprehensive inventory and utilize Lansweeper’s granular reporting, NIST-based risk insights, organized and dynamic network diagrams, and more – all in a powerful solution to efficiently manage your entire network infrastructure.
Discover Your Local Administrators
Try Lansweeper for free! Easily identify all local admins without scripting. Plus, explore detailed device data in your IT environment.
Try Now