
Pro Tips with Esben #12
The log4j vulnerability was disclosed last week and ever since it has become more and more clear that it will be something a lot of people will struggle with for some time. Due to the number of applications impacted the scope is so large that most organizations literally have to review every application and service they use. This week, I want to take a closer look at how Lansweeper can help.
Log4j
To recap briefly what happened, on December 10, CVE-2021-44228 was disclosed impacting the log4j Java library. This logging component is used in a massive amount of applications for (drumroll) logging. The vulnerability is easily exploitable by sending a specific string to the application and therefore got a CVSS score of 10 out of 10!
On December 14, a second vulnerability was disclosed, CVE-2021-45046, while this one has a much lower CVSS score of 3.7, it again requires software publishers to update their log4j components.
To ensure you’re not vulnerable, the applications and services you use must update the log4j component to version 2.16.0. You can read more about the vulnerabilities in our dedicated log4j blog post.
How can Lansweeper help?
The biggest problem everyone has is identifying which software and service are impacted. The log4j Java component doesn’t require Java to be installed on the host machine, and it isn’t always a file you can just search for. Often, the log4j component will be nested multiple layers deep in Java Archive files (JARs).
While doing a file search with a custom script is an option, running this on all your servers can be labor and resource-intensive. However, if you’re willing to try that, I’d recommend consulting the resources listed in the log4j blog post.
Step 1 – Knowing What You Have
So what can you do? Well, the first step is to ensure you have an inventory of your entire IT environment. Without having an inventory of every server, workstation, laptop, switch, firewall, Linux appliance, NAS, IP camera, security system, etc. You won’t know what you need to check. Importantly, this inventory will also give you all the Windows, Linux and Mac software installed in your environment. Every Windows feature installed, every Windows service and even every process running.
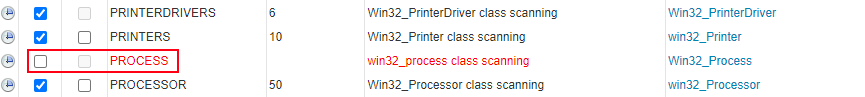
Enabling Process Scanning
By default, Windows process scanning isn’t enabled, but it can help you identify devices running specific software. A concrete example is Nginx on Windows, which is only available to run as a process. To enable this, you can navigate to ScanningScanned Item Interval and enable the checkbox in from of the PROCESS item.
Step 2 – Reporting
Creating a one-fits-all report for Log4j is extremely difficult. Due to a lack of software naming standards, the name that software has as it is stored on a device is often not identical to the one that people use. Even a small deviation will cause a report to not show it in the results. Linux software in particular often has the version of the software in the name as well.
A similar thing goes for Linux appliances, due to the wide variety of them and which SSH commands they respond to, some Linux appliances will provide more data than others.
These problems mean that the best way to report is always to have an example to base your report on. In short, this means that creating your own report will always be the most accurate and I highly recommend you to use a combination of the report templates below and other reports available, both built-in and in our report library to create your own report for finding log4j affected applications and devices.
- Specific Windows, Linux or Mac Software Installed
- All Windows Server Types
- Asset Types Chart
- Windows Processes Overview
- Installed Windows Features
- Specific Windows Service
If you have a report or an idea for a report that could help people deal with the log4j vulnerability don’t hesitate to let us know in the Pro Tips Log4j Forum topic.
Log4j Affected Publishers Report
While creating your own report and using Lansweeper’s inventory is a great way to manage your exposure, we do have a report that everyone can use. This report provides an overview of all Windows software from publishers which are known to have software that has been impacted by log4j.
This report will give you a list of software that you can verify with the impacted software list by the Dutch Cyber Security Center. Check the status of detected software using the list, and take action if needed.
Windows & Linux Webservers
One suggestion from our own internal IT team was getting an overview of all hosted sites. Since the easiest way to exploit Log4j is by submitting the specific string into a web form, any application or appliance that hosts a site should be investigated. It is also something that can be easily overlooked.
Unfortunately, Lansweeper doesn’t do port scanning. However, using a combination of software, feature, services and process scanning, we can identify machines that contain components used for site hosting. Specifically, IIS, IIS Express, Nginx, Tomcat, Apache, and Litespeed.
Step 3 – Fixing
Once you have identified all of your affected applications and services, it is about ensuring everything is updated. You’ll want to verify that log4j is updated to 2.16.0, either by yourself or by the person/company managing the service.
Finding out exactly what „fixing“ means can vary from publisher to publisher, some might have mitigations, workarounds instead of a regular update. Obviously, you’ll want to consult the security advisory of the product affected. Once again, the Dutch Cyber Security Center software list contains links to all security advisories of affected software they list.