A vulnerability has been discovered in Sudo, one of the most important, powerful, and commonly used utilities that comes as a core command installed on almost every UNIX and Linux-based operating system.
The vulnerability in question is a Sudo security policy bypass flaw that could allow a malicious user or a program to execute arbitrary commands as root on a targeted Linux system. The bug requires a system to have a non-standard configuration. In other words, Linux computers are not vulnerable by default.
When executing commands on a Linux operating system, unprivileged users can use the „Superuser do“ command to execute commands as root just by specifying the user ID „-1“ or „4294967295.“
The vulnerability tracked as CVE-2019-14287 does require a nonstandard configuration but nonetheless does open the door to unauthorized users. The Sudo bug allows users to bypass the nonroot restriction by simply using -u#-1 in the command line.
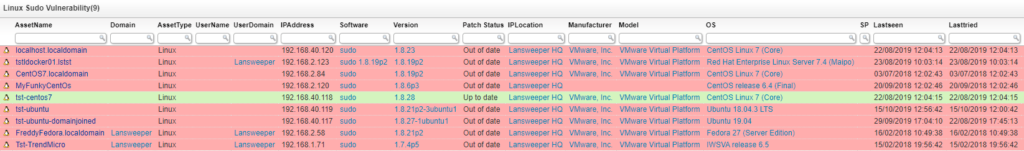
Find Vulnerable Linux Sudo Versions – Run the Audit
All versions prior to the latest released version 1.8.28 are affected by the Linux Sudo vulnerability. If you currently have Sudo installed on your workstations, it’s pretty critical that you update it at the earliest opportunity to ensure that you don’t fall prey to this vulnerability.
Our custom Sudo Vulnerability Audit Report can tell you in no time which devices have an outdated terminal version in place and need to be patched.