SonicWall released a new security advisory for their Secure Mobile Access (SMA) 100-series VPN appliances. The most critical rated vulnerability has a CVSS score of 9.8, so patching is critical.
Unauthenticated Stack-Based Buffer Overflow
CVE-2021-20038 is the most severe vulnerability disclosed today. As mentioned, it boasts a CVSS score of 9.8. The issue lies in the strcat() function used in the SonicWall’s Apache httpd server explains the security advisory:
„The vulnerability is due to the SonicWall SMA SSLVPN Apache httpd server GET method of mod_cgi module environment variables use a single stack-based buffer using `strcat,“
When exploited, an unauthenticated attacker can execute code as a „nobody“ or root user. This allows attackers to gain complete control over the device and allows them to adjust anything from security policies to user accounts and applications.
Additional SonicWall Vulnerabilities
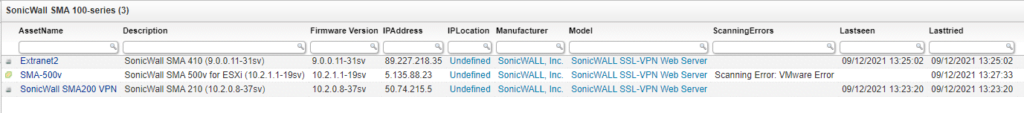
Aside from the previously mentioned vulnerability, an additional 7 vulnerabilities were disclosed and fixed. The second most critical vulnerability is CVE-2021-20045 with a CVSS score of 9.4. This vulnerability is actually a group of vulnerabilities that allow remote code execution (RCE) as a root user. According to the SonicWall security advisory:
„This vulnerability is due to the sonicfiles RAC_COPY_TO (RacNumber 36) method which allows users to upload files to an SMB share and can be called without any authentication,” according to the advisory. “RacNumber 36 of the sonicfiles API maps to the upload_file Python method and this is associated with filexplorer binary, which is a custom program written in C++ which is vulnerable to a number of memory-safety issues.“
Third in line is CVE-2021-20043 with a CVSS score of 8.8. This heap-based buffer overflow vulnerability also allows code execution in the root user context. However, this does require authentication first, hence the lower CVSS score.
The full list of vulnerabilities can be seen below and range from 7.5 to 6.3 on the CVSS scale.
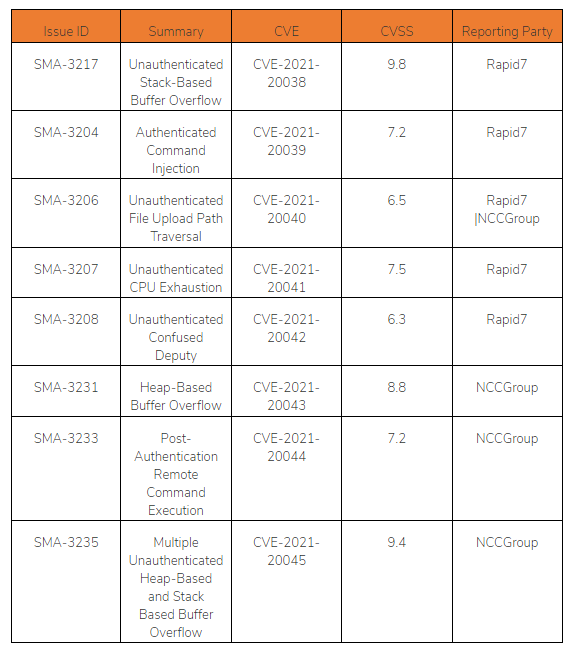
Identify Vulnerable Devices
To prevent exploitation of the vulnerabilities, it is critical that you update your SMA 100-series VPN appliances. This includes the SMA 200, 210, 400, 410 and 500v devices. The report below provides an overview of all the SMA 100-series VPN appliances in your environment along with the device description that should also contain the firmware version. Using this, you can verify that your firmware is up-to-date using the SonicWall security advisory.