⚡ TL;DR | Go Straight to the Sophos Audit Report
Cybersecurity company Sophos has released a patch for its firewall products addressing a code injection vulnerability. The vulnerability has already been used to target a number of specific organizations, primarily in South Asia. When exploited, the vulnerability could allow remote code execution which could compromise essential data or even lead to a complete device takeover of the compromised machine.
CVE-2022-3236
The vulnerability tracked as CVE-2022-3236 is a code injection vulnerability in the User Portal and Webadmin components that could allow for remote code execution in Sophos Firewalls v19.0 MR1 (19.0.1) and older. It received a critical CVSS score of 9.8. Further details about any known exploits will be released as Sophos continues to investigate. For now, all users are advised to update their Firewalls as soon as possible. Until then, you can protect yourself from attacks by ensuring your User Portal, and Webadmin are not exposed to WAN and instead use VPN and/or Sophos Central for remote access and management. You can find instructions to disable WAN access in Sophos‘ device access best practices.
Update Vulnerable Sophos Firewalls
In order to protect yourself against attacks, you should update your Sophos Firewalls to a fixed version. You can find the list below. If you have enabled the „Allow automatic installation of hotfixes“ on a remediated version, you don’t need to take any further action. This feature is enabled by default.
- v19.5 GA
- v19.0 MR2 (19.0.2)
- v19.0 GA, MR1, and MR1-1
- v18.5 MR5 (18.5.5)
- v18.5 GA, MR1, MR1-1, MR2, MR3, and MR4
- v18.0 MR3, MR4, MR5, and MR6
- v17.5 MR12, MR13, MR14, MR15, MR16, and MR17
- v17.0 MR10
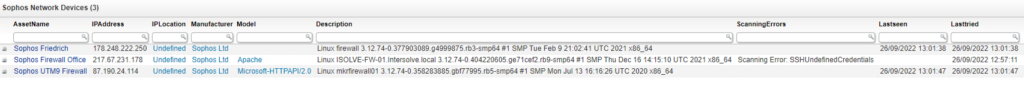
Discover Vulnerable Sophos Devices
Our team at Lansweeper has created a special report that will provide a list of all Sophos devices in your environment including Firewalls. This way you have an actionable list of devices that might require an update.