Chrome 87 Vulnerability Audit
Security VulnerabilityDiscover Chrome 87 Vulnerabilities
Google released an update for Chrome on Tuesday, November 17, 2020, to the Stable desktop channel for the Windows, macOS, Linux platforms with bug fixes, new features, and 56 security fixes.
The Google Chrome browser got an update for several security vulnerabilities together with a technical update to make webpages load faster and use less RAM memory.
It’s the Chrome director Matt Waddell that starts with the good news regarding the technical updates but he also notes that there were 33 security vulnerabilities. Google fixes these vulnerabilities in version 87. The most important flaw is CVE-2020-16022 which allows a remote attacker to bypass security restrictions. After this, the hacker can access all the Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) on the affected system. Samy Kamkar discovered this flaw and called it NAT slipstreaming.
The name comes from its behavior: it’s all about the Network Address Translation (NAT). This can allow hackers to evade firewalls before making a connection to your internal IT networks in order to let users load malicious websites. The targeted device must have the Application Level Gateway (ALG) connection tracking which is built within the NAT. Our Chrome 87 report will detect and update the infected assets within your IT network.
Other Chrome 87 features include:
- Faster start-up
- Load pages faster
- Decreased RAM memory use
- More energy efficient
- search functions to look for an open tab or tab throttling
- ‚Cards‘: a summary of webpages related to the user’s history
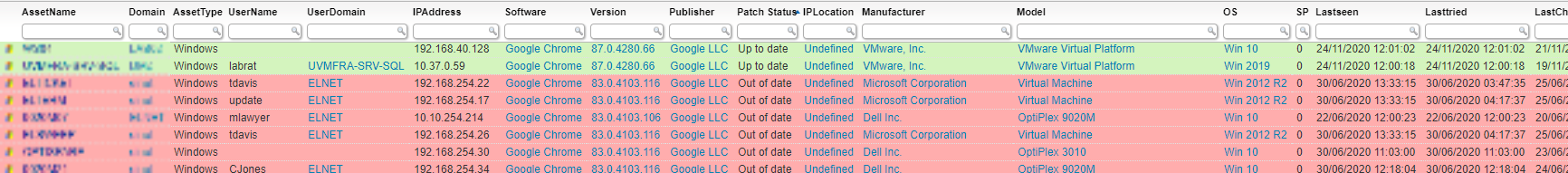
Run The Report Query
Select Top 1000000 tblAssets.AssetID, tblAssets.AssetName, tblAssets.Domain, tsysAssetTypes.AssetTypename As AssetType, tblAssets.Username, tblAssets.Userdomain, tsysAssetTypes.AssetTypeIcon10 As icon, tblAssets.IPAddress, tblSoftwareUni.softwareName As Software, tblSoftware.softwareVersion As Version, tblSoftwareUni.SoftwarePublisher As Publisher, Case When Cast(SubString(tblSoftware.softwareVersion, 0, 3) As INT) > 87 Then 'Up to date' When Cast(SubString(tblSoftware.softwareVersion, 0, 3) As INT) = 87 And Cast(SubString(tblSoftware.softwareVersion, 6, 4) As INT) > 4280 Then 'Up to date' When Cast(SubString(tblSoftware.softwareVersion, 0, 3) As INT) = 87 And Cast(SubString(tblSoftware.softwareVersion, 6, 4) As INT) = 4280 And Cast(SubString(tblSoftware.softwareVersion, 11, 4) As INT) >= 66 Then 'Up to date' Else 'Out of date' End As [Patch Status], tsysIPLocations.IPLocation, tblAssetCustom.Manufacturer, tblAssetCustom.Model, tsysOS.OSname As OS, tblAssets.SP, tblAssets.Lastseen, tblAssets.Lasttried, tblSoftware.Lastchanged, Case When Cast(SubString(tblSoftware.softwareVersion, 0, 3) As INT) > 87 Then '#d4f4be' When Cast(SubString(tblSoftware.softwareVersion, 0, 3) As INT) = 87 And Cast(SubString(tblSoftware.softwareVersion, 6, 4) As INT) > 4280 Then '#d4f4be' When Cast(SubString(tblSoftware.softwareVersion, 0, 3) As INT) = 87 And Cast(SubString(tblSoftware.softwareVersion, 6, 4) As INT) = 4280 And Cast(SubString(tblSoftware.softwareVersion, 11, 4) As INT) >= 66 Then '#d4f4be' Else '#ffadad' End As backgroundcolor From tblAssets Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID Inner Join tsysAssetTypes On tsysAssetTypes.AssetType = tblAssets.Assettype Inner Join tsysIPLocations On tsysIPLocations.LocationID = tblAssets.LocationID Inner Join tblState On tblState.State = tblAssetCustom.State Inner Join tblSoftware On tblAssets.AssetID = tblSoftware.AssetID Inner Join tblSoftwareUni On tblSoftwareUni.SoftID = tblSoftware.softID Left Join tsysOS On tsysOS.OScode = tblAssets.OScode Where tblSoftwareUni.softwareName Like '%Google Chrome%' And tblSoftwareUni.SoftwarePublisher Like '%Google%' And tblState.Statename = 'Active'