Windows Defender Denial of Service Vulnerability Audit
Operating System Security Software VulnerabilityFind Vulnerable Windows Defender Installations
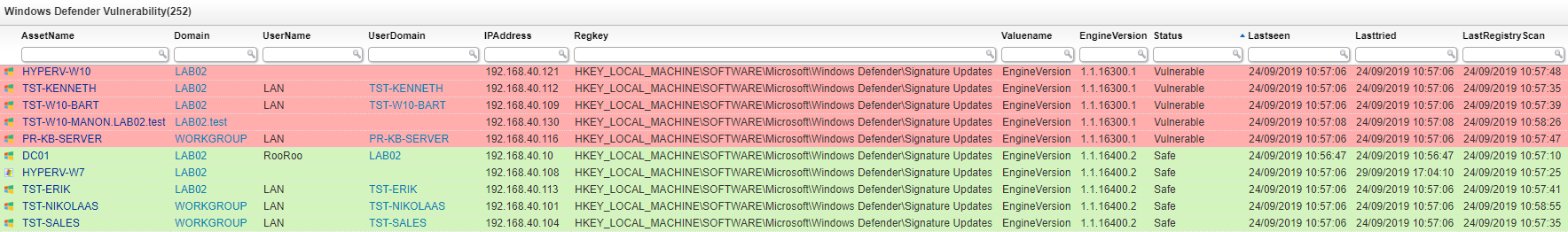
Microsoft released a new update for the Windows defender engine to fix a critical vulnerability (CVE-2019-1255). The latest engine version 1.1.16400.2 fixes the issue, however, it might not be so straight forward to view exactly which machines still need to be updated. You can learn more about it in our Windows Defender flaw blog post.
Fortunately, with the audit below, you can get an overview of your environment and whether the Windows defender engine has been updated or not. This way you can monitor the update progress and identify assets that might have issues receiving the automatic Windows defender updates.
Windows Defender Engine Version Query
Select Top 1000000 tsysOS.Image As icon,
tblAssets.AssetID,
tblAssets.AssetName,
tblAssets.Domain,
tblAssets.Username,
tblAssets.Userdomain,
tblAssets.IPAddress,
SubQuery1.Regkey,
SubQuery1.Valuename,
SubQuery1.Value As EngineVersion,
Case
When SubQuery1.EngineVersion >= 11164002 Then 'Safe'
When SubQuery1.EngineVersion < 11164002 Then 'Vulnerable'
When SubQuery2.EngineVersion >= 11164002 Then 'Safe'
When SubQuery2.EngineVersion < 11164002 Then 'Vulnerable'
Else 'RegKey not found'
End As Status,
tblAssets.Lastseen,
tblAssets.Lasttried,
TsysLastscan.Lasttime As LastRegistryScan,
Case
When TsysLastscan.Lasttime < GetDate() - 1 Then
'Last registry scan more than 24 hours ago! Scanned registry information may not be up-to-date. Try rescanning this machine.'
End As Comment,
Case
When SubQuery1.EngineVersion >= 11164002 Then '#d4f4be'
When SubQuery1.EngineVersion < 11164002 Then '#ffadad'
When SubQuery2.EngineVersion >= 11164002 Then '#d4f4be'
When SubQuery2.EngineVersion < 11164002 Then '#ffadad'
Else ''
End As backgroundcolor
From tblAssets
Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID
Inner Join tsysOS On tsysOS.OScode = tblAssets.OScode
Inner Join TsysLastscan On tblAssets.AssetID = TsysLastscan.AssetID
Inner Join TsysWaittime On TsysWaittime.CFGCode = TsysLastscan.CFGcode
Left Join (Select Top 1000000 tblRegistry.AssetID,
tblRegistry.Regkey,
tblRegistry.Valuename,
tblRegistry.Value,
Convert(bigint,Replace(tblRegistry.Value, '.', '')) As EngineVersion,
tblRegistry.Lastchanged
From tblRegistry
Where
tblRegistry.Regkey Like
'%SOFTWARE\Microsoft\Windows Defender\Signature Updates' And
tblRegistry.Valuename = 'EngineVersion') SubQuery1 On
SubQuery1.AssetID = tblAssets.AssetID
Left Join (Select Top 1000000 tblRegistry.AssetID,
tblRegistry.Regkey,
tblRegistry.Valuename,
tblRegistry.Value,
Convert(bigint,Replace(tblRegistry.Value, '.', '')) As EngineVersion,
tblRegistry.Lastchanged
From tblRegistry
Where
tblRegistry.Regkey Like
'%SOFTWARE\Microsoft\Microsoft Antimalware\Signature Updates' And
tblRegistry.Valuename = 'EngineVersion') SubQuery2 On
SubQuery2.AssetID = tblAssets.AssetID
Where tblAssetCustom.State = 1 And TsysWaittime.CFGname = 'registry' And
tsysOS.OSname <> 'Win 2000 S' And tsysOS.OSname Not Like '%XP%' And
tsysOS.OSname Not Like '%2003%' And (Not tsysOS.OSname Like 'Win 7%'
Or Not tblAssets.SP = 0)
Order By tblAssets.Domain,
tblAssets.AssetName