Compliance with cybersecurity standards is top of mind for IT organizations across industries and geographies. For contractors and subcontractors working with the United States Department of Defense (DoD), ensuring compliance with the new Cybersecurity Maturity Model Certification (CMMC) rule passed in Q4 2020 is a high priority, as they must all meet CMMC requirements by 2026 in order to continue working with the DoD.
In this post, we’ll answer all your questions about CMMC, including what it is, what you must do to comply, and how Lansweeper can make CMMC compliance easier.
What is the CMMC?
The CMMC is a tiered system of compliance measurements for evaluating cybersecurity preparedness and the maturity of an organization’s cybersecurity systems and processes. It provides a unifying standard for implementing cybersecurity systems and processes across the Defense Industrial Base (DIB).
Specifically, the CMMC framework assembles security best practices and technical controls into 17 domains. Each domain is made up of capabilities, processes, and practices that relate to the CMMC’s five maturity levels.

What are the five levels of CMMC?
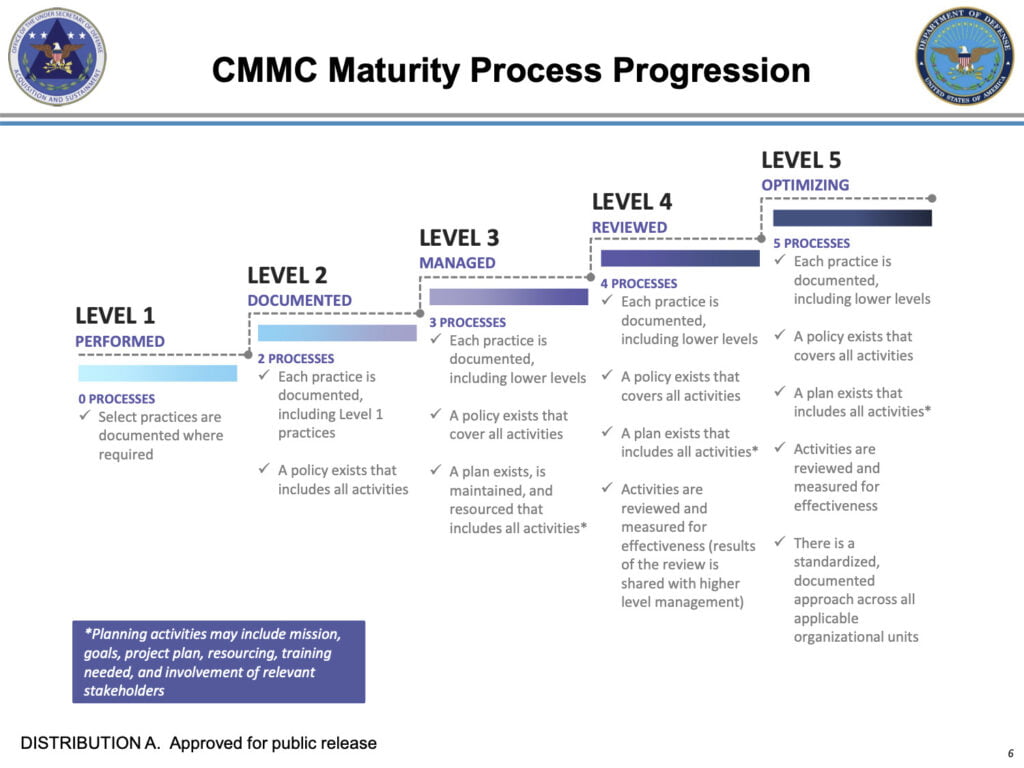
The CMMC assesses the maturity of a DIB supply chain contractor or subcontractor company’s cybersecurity program using a five-tiered maturity model. The maturity levels range from basic cyber hygiene (Level 1) to advanced and progressive cybersecurity (Level 5). The levels are cumulative, so as you move up through the tiers, you must demonstrate compliance with the requirements of all lower levels. Here’s a breakdown of what’s required at each level:
- Level 1: Basic cyber hygiene — The most basic level of CMMC compliance, Level 1 requires organizations to have basic security practices in place, such as access and identity controls and password protection. Most organizations who meet only Level 1 requirements don’t have a comprehensive cybersecurity strategy, and must improve their security solutions to achieve a higher tier of compliance.
- Level 2: Intermediate cyber hygiene — Slightly higher on the maturity scale, Level 2 requires organizations to establish and document their cyber security practices and policies. Organizations working with Controlled Unclassified Information (CUI) need this level of CMMC compliance.
- Level 3: Good cyber hygiene — Level 3 requires compliance with 130 practice and process controls, and mandates the ability to demonstrate good cyber hygiene, and the ability to show implementation of these controls. At level 3, DIB contractors and subcontractors meet the policy and procedure requirements, and have ongoing reports, tracking, systems traceability, applications and services that provide secure CUI access, storage, and transmission. Asset management, configuration management, change management and system integrity — including patch management — are all critical capabilities necessary to meet the requirements of Level 3 CMMC compliance.
- Level 4: Proactive cyber security — At Level 4, organizations are proactive in mitigating the potential threat of a cyber attack. Instead of just being able to respond to security incidents, they must implement processes and systems that enable them to prevent incidents from happening in the first place. In other words, they must prove they can protect CUI from cyber threats.
- Level 5: Advanced and progressive cyber security — Organizations meeting Level 5 requirements must standardize and optimize proactive security processes and systems across the organization. They are continually optimizing their processes, their systems are more sophisticated, and they will have implemented many additional practices above and beyond those required for Level 4 compliance.
Did the CMMC rule change recently?
In November 2020, a rule change to Defense Federal Acquisition Regulations (DFARS) regarding the CMMC was passed, finalizing CMMC as an official Department of Defense policy, which means that the U.S. government can now add CMMC requirements into defense contracts.
Why is CMMC compliance important?
According to the White House Council of Economic Advisors, in 2016, malicious cyber activity cost the U.S. economy between $57 billion and $109 billion. Worse yet, sensitive information could fall into the hands of bad actors or U.S. adversaries as a result of gaps in cyber security. CMMC is designed to be a unifying standard for implementing cybersecurity across the DIB, with the ultimate goal of ensuring that defense contractors don’t have network vulnerabilities that could lead to the loss of sensitive DoD data or a data breach that could put the country at risk.
Who is required to be CMMC compliant?
CMMC compliance can benefit any business because it helps to improve an organization’s overall cyber security posture. However, any organization that leverages DoD information must comply with at least the minimum level of CMMC requirements — regardless of size or business focus. «Within our mission and goal of providing guidance to achieving CMMC certification readiness within the defense industrial base, we encounter a broad variety of organizations of all sizes participating within the U.S. DoD supply chain,” said U.S.-based Paul Veeneman, President & COO of @Beryllium Infosec Collaborative.
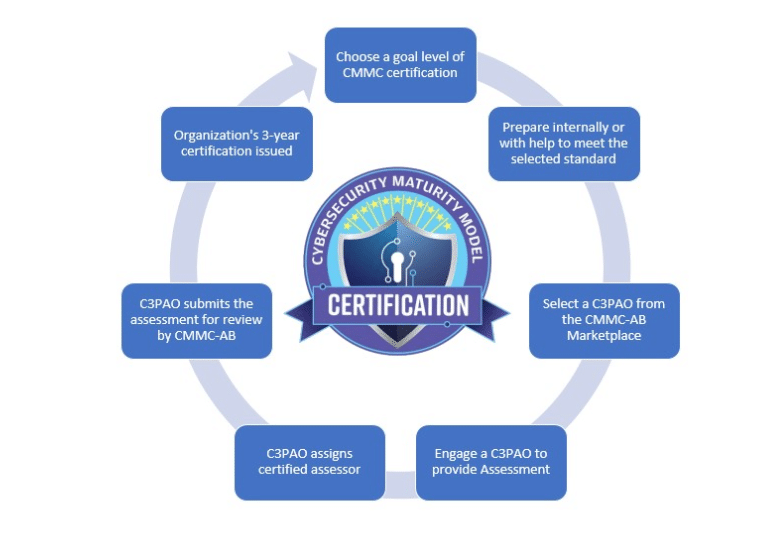
How does my organization become CMMC compliant?
First, your organization’s security program must be assessed by an independent, third-party assessor that is certified by the DoD who can evaluate your security posture and make recommendations for filling in any gaps. You will then have 90 days to fix any issues.
But fixing those issues will require having in place the capabilities for discovering, monitoring, and managing connected IT, OT, and IoT assets across the IT estate. This holds true for any contractor interested in working with the DoD. “One constant among the organizations serving the DoD is the need for discovery, cataloging, management, and monitoring of their technology asset inventory that provides access, storage, or transport of Controlled Unclassified Information (CUI),” Veeneman said.
“Knowing what assets you have, collecting detailed asset inventory data, and assessing your current security posture, vulnerabilities and threat landscape are critical first steps to defining a cyber security program.”
— Paul Veeneman, President & COO of the Beryllium Infosec Collaborative.
What level of CMMC compliance (tires 1-5) do I need to meet?
If the DoD information your organization uses to operate is non-classified, Level 3 or below may be sufficient. If the information is classified or of higher value, Level 4 or 5 compliance may be required.
Is there a CMMC certification available?
Yes. Once you’ve completed the assessment and made any changes needed, you can request certification, which is valid for three years.
How can Lansweeper help my organization achieve CMMC compliance?
Simply put, you can’t protect what you can’t see. Lansweeper’s IT asset discovery platform discovers and identifies all network-connected devices, including IT, OT and IoT. The platform’s advanced Asset Radar and Credential-free Device Recognition (CDR) technologies detect assets the moment they come online, eliminating blind spots and providing access to granular information such as hardware and software specifications, user details, and more.
Within 35 minutes of downloading the Lansweeper application, DoD supply chain, and DIB contractors and subcontractors are on their way to achieving conformity and compliance in the following CMMC practices, and potentially others:
- CMMC Asset Management: Lansweeper provides real-time, up-to-date, comprehensive view of hardware assets connected to an organization’s network.
- CMMC Configuration and Change Management: Lansweeper captures information system characteristics critical to meeting CMMC maturity Level 3 requirements, including OS, installed software, vulnerable software, installed security patches and more.
- CMMC Audit & Accountability and System Integrity: Lansweeper delivers dashboards and reports that can be customized and updated continuously to provide DIB contractors and subcontractors metrics such as missing security patches and current vulnerabilities.
“Lansweeper delivers the technology asset management features and functionality that allows organizations to meet applicable CMMC controls and objectives, establish baseline configurations, track and trace change within the environment, and continuously maintain and monitor critical assets containing CUI.”
— Paul Veeneman, President & COO of the Beryllium Infosec Collaborative.
CMMC Compliance, Simplified
Lansweeper helps organizations achieve any level of CMMC compliance while reducing the operational overhead associated with third-party assessments and audits. With Lansweeper, contractors and subcontractors all along the DIB supply chain can have a complete and always accurate IT asset inventory — the fundamental starting point for implementing security measures across your organization and taking a proactive and progressive stance against cyber threats.
“Knowing what assets you have, collecting detailed asset inventory data, and assessing your current security posture, vulnerabilities and threat landscape are critical first steps to defining a cyber security program,” Veeneman said. “Lansweeper delivers the technology asset management features and functionality that allows organizations to meet applicable CMMC controls and objectives, establish baseline configurations, track and trace change within the environment, and continuously maintain and monitor critical assets containing CUI.»
Don’t let CMMC derail your ability to win and maintain DoD contracts — get started with Lansweeper today. Learn more about how Lansweeper helps organizations strengthen their cybersecurity posture, or try Lansweeper for free.
CMMC FAQs
Before we begin to consider the challenges to implementing CMMC into your risk management and compliance programs, let’s address some of the most commonly asked questions about CMMC.
Not necessarily. If you only bid on defense contracts with low-security risks (say, supplying foodstuffs), you might need only the “basic” (level 1) maturity level. If you want to bid on projects with high-security risks (say, mission-critical technology for satellite imagery), you would likely need the “advanced” maturity in level 5.
The Defense Department is starting CMMC compliance only with a select number of large “prime” contractors this year. More and more contractors will be subject to CMMC over the next five years until all defense contracts require CMMC compliance in the fiscal year that starts on Oct. 1, 2025.
The U.S. government has no plans right now to expand CMMC beyond the Defense Department — but “right now” is the crucial phrase here.
How to Begin CMMC Compliance
The first step in CMMC compliance is to understand what level of maturity your business wants to achieve. One part of that task is to review the CMMC standard itself and the controls associated with each level. Another part is to ask senior executives how much of their business strategy depends on defense contracting or working within the defense industrial base.
Is the business likely to merge with a prime contractor sometime soon, where preparing for a higher maturity level might make you a more attractive acquisition target? The compliance maturity you want will depend on the strategic objectives that senior executives set. Understand those objectives and explain to senior leaders that their objectives will have implications for CMMC compliance.
Then will come the true challenge of assessing your current cybersecurity regime and implementing remediation steps necessary to bring your program to the CMMC level you want to achieve.
Effective technology will be indispensable because of the sheer volume of work likely to be involved. You will likely need to juggle pieces of several cybersecurity frameworks to identify policies, procedures, and other controls that need attention; and you’ll need a way to monitor that all mitigation work is done in a timely manner; and you’ll need to document your progress to pass the independent assessment that awaits at the end of your program update.
Perhaps the most critical step you can take for CMMC compliance is to establish the understanding that CMMC is inevitable and will be a complex undertaking throughout senior executives, the board, and other executives in the First and Second lines of defense of your business.
Expect some back-and-forth among risk managers, the CISO, your data privacy team, your procurement function if you have one, and leaders of other business operating units. Expect thorough work to develop effective controls, test them, and document them.
It’s going to be a long journey, with the occasional bump along the way. On the far side of CMMC compliance, however, your business will have a better cybersecurity posture and be able to bid on contracts from one of the biggest customers around – the U.S. Defense Department. Not too many boards and CEOs would be unhappy with that.
 — Paul Veeneman, President & COO of the Beryllium Infosec Collaborative.
— Paul Veeneman, President & COO of the Beryllium Infosec Collaborative.