
The Apache Software Foundation dropped a vulnerability cluster bomb on Friday, 10 December. Their Log4j java-based logging component contains a remote code execution that is extremely easy to exploit and as a result achieved a CVSS score of 10, the highest possible.
What is Log4j?
CVE-2021-44228, log4j, Log4Shell, or LogJam, whatever you would like to call this vulnerability, has exploded over the weekend. Sporting a rarely seen CVSS score of 10, this vulnerability is very widespread, easy to exploit, and allows for a complete takeover of systems or applications.
Log4j is a java-based logging package used by developers to log errors. Due to the popularity of the log4j library, many major publishers and manufacturers have been assessing their software to determine whether it has been impacted or not. Big names like Amazon, Apple iCloud, Cisco, Cloudflare, ElasticSearch, Red Hat, Steam, Tesla, Twitter, and more useful applications that make use of the log4j library.
Second Log4j Vulnerability
On December 14, 2021, a second much less critical vulnerability was found. CVE-2021-45046, with a CVSS score of 3.7, affects all log4j versions from 2.0-beta9 through 2.12.1 and 2.13.0 through 2.15.0. This means if an application you were using was vulnerable to the original log4j vulnerability, you will most likely have to update it again.
The new Apache security advisory mentions that attackers can «craft malicious input data using a JNDI Lookup pattern resulting in a denial-of-service (DoS) attack,». To fix the issue log4j 2.16.0 has been released.
Third Log4j Vulnerability
December 18, 2021, a third vulnerability was disclosed, CVE-2021-45105. While this one was less severe, only sporting a CVSS base score of 5.9, the vulnerability did result in a new updated log4j version of 2.17.0. The issue itself lies in the log4j API which can be crashed using a crafted variable.
Who Is Affected?
Any application using the log4j library with a version from 2.0-beta9 to 2.17.0 is vulnerable. This means that pretty much any application using log4j 2 is vulnerable until updated to the latest version 2.17.0. Since this library is so widely used, there isn’t a simple list of all applications that use the log4j library. There are plenty of attempts to create a centralized overview of affected products:
- Dutch Cyber Security Center Affected Software List
- BlueTeam Advisories Collection
- Tech Solvency CVE-2021-44228 cheat-sheet
Lansweeper & Log4j
Many customers have contacted us regarding log4j and the effect on Lansweeper. Our security teams have investigated the impact of the log4j vulnerability, CVE-2021-44228. We’re glad to confirm that all local, cloud, and third-party services delivered with Lansweeper are unaffected.
Finding Affected Devices and Applications
Finding out which applications in your environment have been a problem for most organizations. Since so many applications use the affected library, using a list isn’t always the best method to find which devices/applications you have in your environment are affected. Below are three great resources thanks to all the great people participating on Reddit.
These Reddit posts contain great info on how you can detect applications running the library, how you can detect possible attacks, custom scripts, and lots of articles covering every technical detail.
Using Lansweeper for Log4j
Many of you have asked how Lansweeper can help in detecting possible log4j vulnerable applications or devices. We have created 2 reports that can help you in the initial stage of finding affected devices. It is important to state that these are rudimentary reports based on current information available and should be used in combination with many of the resources listed above to minimize your exposure to log4j.
Affected Software Publishers
Utilizing the software list from the Dutch cyber security center, we’ve created a report that lists all software from the publishers mentioned. The report is designed to be used in combination with the cyber security center list to check if software detected has been investigated and found to be vulnerable. Publishers already found not affected have been omitted from the report.
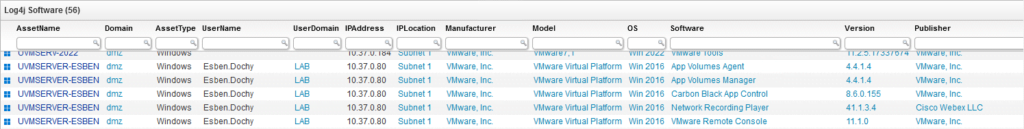
Log4j Event Log Entries
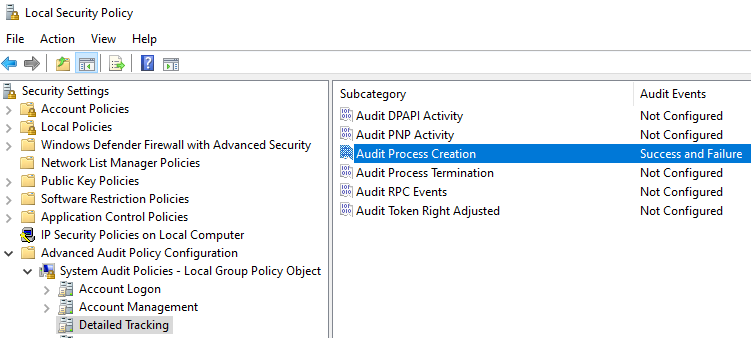
The second report is an event log audit. Once you configure Lansweeper to scan more event types, you can audit all your scanned event logs for the word «log4j». By enabling additional logging in the Windows event log, you can also improve your chances of catching the log4j usage.
An example of how you can improve coverage of your logging is by enabling Audit Process Creation logging. By enabling this, in addition to enabling the scanning of success audit events, you’ll be able to scan and audit event 4688(S): A new process has been created.
Aside from the two new reports, don’t forget that all our old reports are available in the report library and can be used as well. Specifically, the following ones might be useful during your log4j mitigation endeavors: