⚡ TL;DR | Go Straight to the Linux ‘Dirty Pipe’ Vulnerability Report
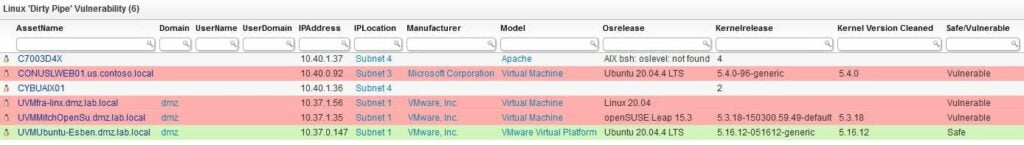
Linux Kernel 5.8 and later are vulnerable to a vulnerability dubbed ‘Dirty Pipe’ which allows local users to get root access. The vulnerability has been fixed in Linux kernels 5.16.11, 5.15.25, 5.10.102, and higher.
CVE-2022-0847 also known as Dirty Pipe allows local users to inject and overwrite data in read-only files, this can lead to privilege escalation because unprivileged processes can inject code into root processes. Max Kellermann, who disclosed the vulnerability, also mentions that the vulnerability is similar to CVE-2016-5195 “Dirty Cow” but is easier to exploit.
Several proofs of concept were disclosed today, including in the original disclosure, showing that the vulnerability is relatively easy to take advantage of.
To fix the vulnerability, new Linux kernel versions were released. To ensure that your Linux devices are safe, kernel versions 5.16.11, 5.15.25, 5.10.102 or higher need to be installed. Together with our Dirty Pipe vulnerability report, you can easily identify which Linux devices have which kernel version and whether they require an update.