⚡ TL;DR | Go Straight to the Veeam ONE Vulnerability Audit Report
Veeam has released hotfixes for their Veeam ONE IT monitoring and analytics platform addressing 4 new vulnerabilities, 2 of which are critical. If successfully exploited these flaws could allow an unauthenticated attacker to execute remote code or an unprivileged user to obtain the NTLM hash of the account used by the Veeam ONE Reporting Service. We have added a new report to Lansweeper to help you identify any at-risk Veeam ONE installations
Veeam ONE Vulnerabilities
Veeam’s new advisory addresses a total of 4 vulnerabilities in Veeam ONE, 2 of which are critical and 2 of medium severity. Regardless of severity, all of these vulnerabilities have the potential to compromise sensitive data or disrupt operations. In order of severity:
- CVE-2023-38547 received a critical CVSS score of 9.9. It allows an unauthenticated user to gain information about the SQL server connection Veeam ONE uses to access its configuration database. This could allow them to execute remote code on the SQL server hosting the Veeam ONE configuration database. This flaw affects Veeam ONE 11, 11a, and 12.
- CVE-2023-38548 is another critical flaw with a CVSS score of 9.8. It only affects Veeam ONE 12. It could allow an unprivileged user who has access to the Veeam ONE Web Client to acquire the NTLM hash of the account used by the Veeam ONE Reporting Service.
- CVE-2023-38549 has a medium severity rating with a CVSS Score of 4.5. This vulnerability affects Veeam ONE 11, 11a, and 12. It’s a cross-site scripting (XSS) vulnerability that allows a user with the Veeam ONE Power User role to obtain the access token of a user with the Veeam ONE Administrator role.
The severity of this flaw was reduced, however, because it requires interaction by a user with the Veeam ONE Administrator role. - CVE-2023-41723 is another medium severity vulnerability (CVSS score: 4.3) that again affects Veeam ONE 11, 11a, and 12. It allows a user with the Veeam ONE Read-Only User role to view the Dashboard Schedule. Again the criticality of this vulnerability was reduced because the user would only be able to view the schedule, not make any changes.
Update Vulnerable Veeam ONE Installations
Hotfixes are available for these flaws for the versions listed below. If you are running an older version of Veeam ONE make sure to update your installations first.
- Veeam ONE 12 P20230314 (12.0.1.2591)
- Veeam ONE 11a (11.0.1.1880)
- Veeam ONE 11 (11.0.0.1379)
All download information as well as the deployment information for the hotfixes is available in Veeam’s advisory.
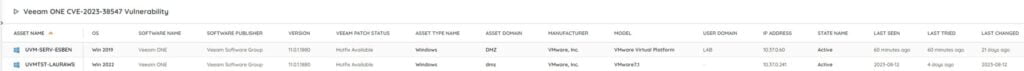
Discover At-Risk Veeam ONE Installations
We have added a new vulnerability report to Lansweeper to help you locate any vulnerable installations of Veeam ONE in your network. Please note that the report only lists the versions listed above, as those have hotfixes available. If you have older installations, make sure to update them first. This will give you an actionable list of devices that still require you to take action. You can get the report via the link below.