
The emergence of cloud environments is transforming the way organizations manage and store their data. As businesses continue to migrate their operations to cloud environments, the need for robust security measures is growing.
Cloud security dashboards offer unparalleled visibility into the dynamic landscapes of cloud infrastructures. From real-time monitoring to compliance assurance, these visualizations empower organizations to navigate the intricate challenges of securing their data in the cloud.
The Importance of Visibility in Cloud Security
You’ve probably heard this a million times before: you can’t protect what you don’t know you have. Visibility is a critical first step in any security strategy and your cloud security strategy is no exception. In fact, the rule applies even more so in the cloud.
Cloud environments are complex, dynamic, and constantly expanding. Assets are added, removed, and moved around all the time. Keeping track of your cloud assets and resources without the proper tooling is a grueling task. With the added complexity of multi-cloud infrastructures, it is nigh on impossible.
An IT security dashboard gives you immediate insights into your IT environment. Lansweeper’s scanning algorithm collects massive amounts of IT asset data. With the Lansweeper IT Dashboard, you can browse and select all relevant data about your IT environment. Gather and visualize the insights you need in a customized overview dashboard using your choice of charts and widgets.
The Role of IT Security Dashboards in Resource Access Monitoring
Real-time insights are essential to any cybersecurity strategy. Both your cloud environment and the threat landscape you are protecting it from are ever-evolving and need to be watched closely. Cyberattacks can strike at any moment and cause immediate and devastating damage.
Cloud security dashboards help you keep track of unauthorized access and suspicious activity in your cloud environment. This way you can sniff out potential threats before they become an issue. Your cloud security tools keep track of resource access by analyzing user activities, configuration changes, and data transfers within cloud environments to identify anomalies.
A well-organized dashboard presents this information in an easily digestible way. That way you have all the information you need to nip potential security threats in the bud.
How Do Cloud Security Dashboards Aid in Data Breach Detection?
There are a lot of indicators that could warn you of a data breach, but they are difficult to spot with the naked eye. Cloud security dashboards give you a comprehensive view of data transfers, user activity, and configuration changes. By analyzing logs from diverse systems, dashboards also scrutinize authentication, access changes, and network traffic for signs of security breaches.
Gathering this network data in a clear and easy-to-interpret dashboard allows you to more easily determine patterns and spot anomalies, deviations, and outliers in network traffic, data access, configuration, user behavior, and more. All of these can be signs of potential unauthorized access, malicious activity, or compromised accounts. Having all this information in a consolidated view allows security teams to investigate and mitigate potential breaches swiftly and proactively.
Ensuring Cloud Compliance Through IT Security Dashboards
By providing a centralized and visualized overview of key security metrics and activities, IT security dashboards are a convenient tool for securing compliance. Many IT security frameworks have visibility as one of their main requirements.
Most organizations have some sort of tool to keep an inventory of their IT assets and track network and user activity. Summarizing this data in a comprehensive and visual representation helps security teams to proactively address security concerns, maintain policies, and provide the necessary documentation for compliance audits.
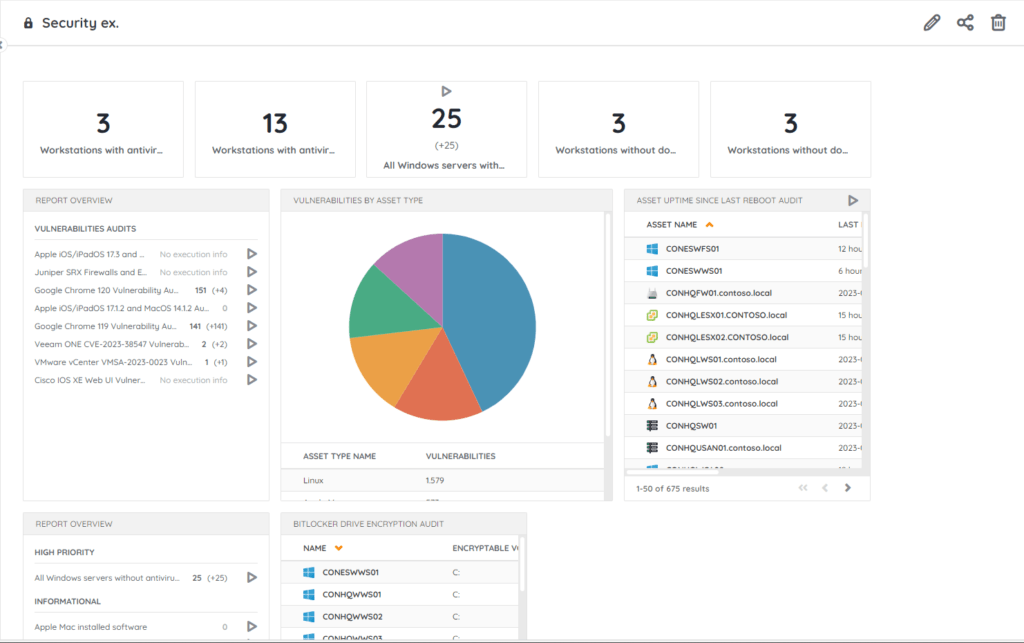
Visualizing Cloud Security
Cloud security gathers data from diverse data sources in complex, dynamic, often multi-cloud environments across distributed infrastructures. So how do you present this abundance of security metrics in a cohesive and actionable manner?
IT security dashboards organize your complex data into clear and visually intuitive representations. Thanks to the visually digestible format security teams can easily identify anomalies, deviations from network patterns, potential threats, and critical security issues. This supports informed decision-making, prioritization, and resource allocation, for faster and more effective incident response in the cloud.
IT Security dashboards offer a wide variety of visualization options for you to choose from, ranging from simple reports to charts, to detailed network diagrams displaying all interconnected systems, devices, and data flows. All of these come together to help security professionals understand your network’s layout, operations, and dependencies. When everything is in the right place it is easy to spot anomalies, deviations, and possible vulnerabilities.
Empowering Cloud Security at Lansweeper
As organizations increasingly embrace cloud technologies, cloud security dashboards emerge as indispensable tools in navigating the complexities of modern IT landscapes. These dashboards provide a holistic view of cloud security metrics. Through visualizations, they empower security teams to proactively detect anomalies, enforce access controls, and respond swiftly to potential threats.
Lansweeper gathers extensive amounts of detailed asset data. It is only natural that it also provides you with a dashboard to organize everything into a neat and digestible overview. Lansweeper’s customizable IT dashboard lets you put the information that is relevant to you front and center. Customize your dashboard with drag-and-drop widgets for graphs, tables, and charts to visualize your key metrics the way you want.