The NIS2 directive, the EU’s new cybersecurity legislation – and direct successor to the NIS1 Directive from 2016 – has a much wider scope than its predecessor. The scope of the directive is defined by the size of an organization and a (now much longer) list of (sub)sectors and types of services.
- Know if your organization fits within the scope.
- How does NIS2 affect your sector and the services you provide?
- How can you prepare for compliance?
What You’ll Learn
The Scope of NIS2
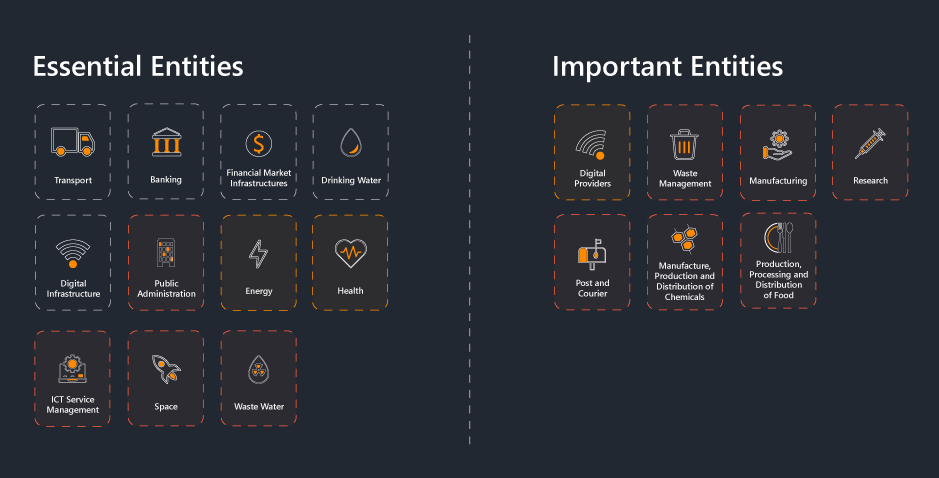
A company is in scope if it operates in one of the (sub)sectors and types of services specified by the directive (listed below) AND is considered a large or medium-sized entity. An entity is considered medium-sized or large if it has more than 50 employees OR an annual turnover of over €10 million.
Since the entities covered by NIS2 are those that are considered highly critical or critical, any security breaches will not only have a serious impact on the services they provide, but will also disrupt operations and day-to-day life for the recipients of those services. This is what makes them essential or important in the eyes of NIS2.
Note: In the image below we have marked in red the sectors that were added under the NIS2 directive and in orange the ones that have had their scope expanded. The others were already in scope under NIS1.
NIS2 Compliance – What You Need to Know
Learn more about the scope and timeline of the NIS2 Directive.
LEARN MOREStrengthening the EU’s Cybersecurity Profile
The NIS2 Directive is long and detailed, but for the essential and important entities in scope, the gist is to take appropriate and proportionate measures to manage the security risks to their IT Network and to mitigate the impact of incidents on their services. Most information you need about these requirements can be found in Article 21 of the NIS2 Directive.
If you have been involved in the cybersecurity risk management process before, most of the measures the directive touches upon will sound familiar. In summary, it concerns things like risk analysis, incident handling, business continuity, supply chain security, cyber hygiene, encryption policies, access control, asset management, multi-factor authentication, and of course policies to assess the effectiveness of all these measures.
Preparing for NIS2 through Cybersecurity Risk Management
NIS2 is going into effect on 17 October 2024. The key to compliance is timely preparation so you can get all of your processes in place, budgets approved, and stakeholders on board. Identify your critical infrastructure and processes and implement a sustainable risk and information security management policy and procedures.
Cybersecurity Asset Management
As everyone knows, good cybersecurity starts with good asset management. Asset security starts with knowing what assets you have. Full visibility and control of your IT estate, its IT, OT, and IoT devices, installed software, users, and groups are a prerequisite for the next steps, like cyber security risk management, access control, cyber hygiene, and security framework compliance. A reliable cybersecurity asset inventory helps you stay on top of your IT asset lifecycle and eliminate blind spots in your network.
Risk Management
Risk management can be broken down into three stages, identify, assess, and respond. The first step is to identify the vulnerabilities that are affecting your network and the threats that may exploit them. In the second stage, you can then analyze the severity of each risk and prioritize which issues to respond to first and how (accept, avoid, transfer, or control). It is important to note that this is a continuous process. Risks should be monitored and reviewed to respond to changes in the threat landscape.
Incident Handling
If you do face a security breach, make sure to have an incident response and risk mitigation plan at hand. Know the layout of your network and dependencies, so the breach can be isolated from the rest of your network. Make sure that everyone on the team knows their role and responsibilities in case of a security incident and keep clear communication channels.
Cyber Hygiene
Besides vulnerability management, having the right policies and procedures in place to mitigate existing risks. Many issues can be avoided with good cyber hygiene, like properly managing your firewalls, encryption, MFA, patching your software, access management, and security awareness training for your employees.
OT Asset Management
Due to the nature of the sectors in scope, especially those in manufacturing, many of the organizations included in NIS2 or dealing with crucial operational technology. In this day and age OT is often an integral part of the technology estate, but unlike IT, OT is often not patched or upgraded regularly, making it a prime target in cyber-attacks. When preparing for NIS2, make sure to consider your entire technology estate; IT, OT, and IoT in your cybersecurity asset management.
Access Control
Any organization that makes it into the NIS2 scope is potentially dealing with sensitive information. It is what makes some sectors like public admin or research facilities coveted targets for cyberattacks. Make sure you have strong access control policies in place to manage user permissions and privileges and limit access to crucial and sensitive data.
Get Ready for NIS2 with Lansweeper
Cyber security, asset management, and risk management go hand-in-hand. Lansweeper’s unrivaled asset discovery casts a wide net when it comes to gathering software, hardware, and user data from all of your IT, OT, and IoT devices. Monitor the usage of data encryption, AV installations, software that is out-of-date, unauthorized local admins, backup creation, and more. Everything you need to know to prepare your network for NIS2, Lansweeper has it.
Lansweeper’s risk insights speed up your risk analysis and easily track down misconfigurations. Had a security incident? Use Lansweeper to identify other potentially vulnerable machines.