⚡ TL;DR | Go Straight to the Palo Alto Networks Vulnerability Audit Report
Palo Alto Networks has released security updates for their Next-Generation Firewalls addressing 2 zero-day vulnerabilities that are already under active exploitation. The vulnerabilities are a critical authentication bypass and a privilege escalation flaw both in the PAN-OS software. Successful exploitation could compromise critical data and systems so users are advised to update vulnerable devices as soon as possible. We have added a new report to Lansweeper to help you find them.
Palo Alto Networks Vulnerabilities CVE-2024-0012 and CVE-2024-9474
This security update addresses connected 2 vulnerabilities. The most critical is CVE-2024-0012, an authentication bypass in the PAN-OS management web interface with a severity score of 9.3. It could allow an unauthenticated attacker to gain PAN-OS administrator privileges to perform administrative actions, tamper with the configuration, or exploit other authenticated privilege escalation vulnerabilities like CVE-2024-9474.
CVE-2024-9474 is itself a privilege escalation vulnerability, also in the PAN-OS web management interface. When successfully exploited it could allow an attacker with PAN-OS administrative privileges to perform actions on the firewall with root privileges.
You can read more in Palo Alto Networks’ security bulletins linked above.
Update Vulnerable PAN-OS Instances Now
The vulnerabilities described above affect several versions of the PAN-OS software. The vulnerabilities do not affect Cloud NGFW and Prisma Access. The issue has been fixed in PAN-OS 10.2.12-h2, PAN-OS 11.0.6-h1, PAN-OS 11.1.5-h1, PAN-OS 11.2.4-h1, and all later PAN-OS versions. You can find all the details on Palo Alto’s advisory page.
| Versions | Affected | Unaffected |
| Cloud NGFW | None | All |
| PAN-OS 11.2 | < 11.2.4-h1 | >= 11.2.4-h1 |
| PAN-OS 11.1 | < 11.1.5-h1 | >= 11.1.5-h1 |
| PAN-OS 11.0 | < 11.0.6-h1 | >= 11.0.6-h1 |
| PAN-OS 10.2 | < 10.2.12-h2 | >= 10.2.12-h2 |
| PAN-OS 10.1 | None | All |
| Prisma Access | None | All |
As a general rule, Palo Alto Networks urges its users to secure access to their management interface. In case it is not possible for you to update right away this can also help as a workaround. You can find full instructions in their advisory.
Discover Vulnerable Palo Alto Devices
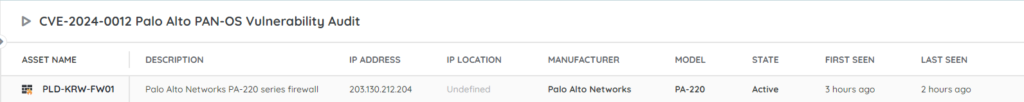
We have added a new report to Lansweeper to help you find any devices in your network that may be running a vulnerable version of PAN-OS. This will give you an actionable list of devices that are at risk. You can get the report via the link below.