
Just hearing the words “ransomware” is enough to send a shiver down the spine of every IT professional and executive. We are all familiar with the concept by now. However, ransomware gangs like RansomHub continue to develop more sophisticated tactics, which means cybersecurity strategies must constantly evolve to keep pace.
RansomHub’s recent attack on Halliburton highlights the danger of double-extorsion techniques. These attacks combine data theft and file encryption to cause maximal disruption, in order to coerce their victim into paying the ransom. The attack prompted the U.S. government to issue an advisory about the need for robust security measures including timely updates to operating systems, software, and firmware.
The Rise of Ransomware
Crowdstrike’s 2024 Threat Report shows that the number of victims named on dedicated leak sites attacks has increased by 76% between 2022 and 2023. Ransomware attacks lead to widespread disruptions and potential catastrophic harm to an organization’s data and operations caused by loss of productivity, loss of critical files and data, and of course the loss of customer data which can in turn lead to serious reputational damage and legal and compliance issues. Recovering operations can take time leading to further financial losses. Not to mention, the ransom payments themselves can reach hundreds of thousands of dollars.
This underscores the urgent need for comprehensive security strategies across industries. Malicious actors are always on the lookout for vulnerabilities in operating systems, network configurations, and widely-used software. Securing these areas is essential for a robust cybersecurity posture, but it all begins with gaining full visibility into your technology estate.
Combatting Your Ransomware Risks With Lansweeper
Lansweeper offers a variety of tools to help you identify ransomware risks and prioritize, track, and manage your mitigation efforts.
Identify
The first step in any risk management process, especially addressing ransomware threats, is identifying where those risks lie in your network. Ransomware gangs and other cybercriminals will look for vulnerabilities in your network’s defenses in order to infiltrate. To prevent this, you must have complete visibility into your IT environment, ensuring that no vulnerable system goes unnoticed.
Lansweeper provides complete and comprehensive visibility into all IT, OT, IoT, and Cloud assets that make up your technology estate. Thanks to a combination of active and passive scanning, Lansweeper picks up on any outdated systems, unpatched software, and unauthorized devices. All data is automatically gathered in an intuitive and easy-to-use inventory so you can easily spot any potential weak points in your hardware, software, and network configurations that ransomware actors could exploit.
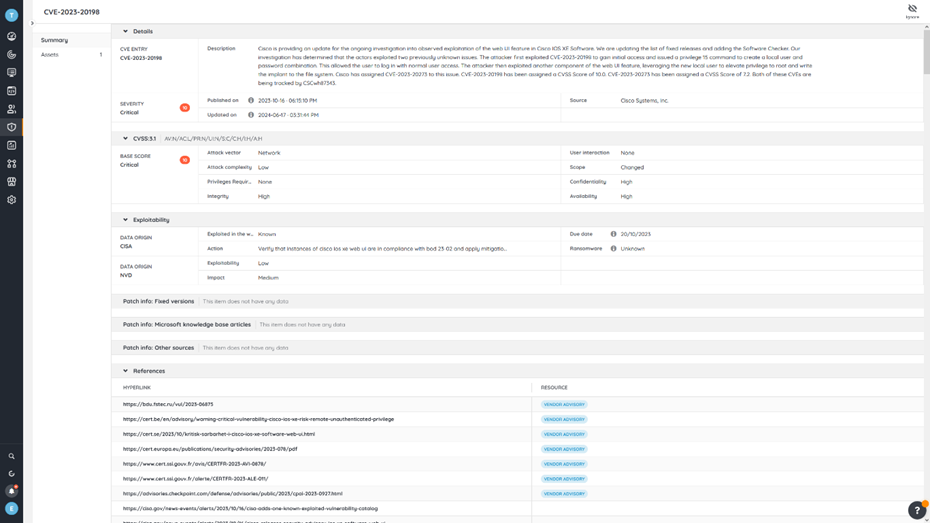
There are several ways that Lansweeper helps you identify risks. The first and most obvious one is through the Risk Insights feature. Lansweeper’s Risk Insights hold your IT asset data up against known vulnerabilities from the VulnCheck, VulDB, CISA, and MS databases. This way it automatically matches your devices with known vulnerabilities so you have real-time insights into the vulnerabilities that could be threatening your network.
Secondly, Lansweeper offers custom reporting so that you can query the detailed asset data that Lansweeper has gathered to single out the information you need to perform a comprehensive risk analysis. You can audit your network for misconfigurations, compliance breaches, and security gaps based on all available data including device model, manufacturer, domain, user details, BitLocker encryption, certificates, and much more, giving you full visibility into potential risks.
Some additional features, such as file scanning and registry key scanning, can offer valuable information to detect ransomware indicators such as suspicious files or unusual registry key changes. These features can help spot the earliest signs of ransomware activity, such as the presence of known ransomware executables or abnormal modifications to system configurations.
Prioritize
Once you have insight into all vulnerabilities and weak spots in your technology estate, the next step is to determine which areas need your immediate attention and resources, so you can prioritize your mitigation efforts.
Lansweeper’s Risk Insights, don’t just show you what vulnerabilities are threatening your network, they also provide in-depth information such as official references, exploitability, CVSS score, and more. Based on this information you can properly assess the exposure of any given vulnerability from multiple angles so you can prioritize the most critical ones. Custom views let you filter through the noise even more by letting you add fields and filters to put the information you need front and center. These detailed insights ensure that you can single out the high-priority issues that are most likely to be exploited in ransomware attacks and could cause the most significant damage.
Comprehensive risk analysis is further supported by custom reporting. You can use existing or build new reports to audit devices for misconfigurations, compliance breaches, and security gaps, using the detailed IT asset data Lansweeper collected like device services, software, lifecycle status, domain, user details, BitLocker encryption, certificates, and more. Thanks to this detailed information you have full visibility into any potential vulnerabilities that ransomware gangs could exploit.
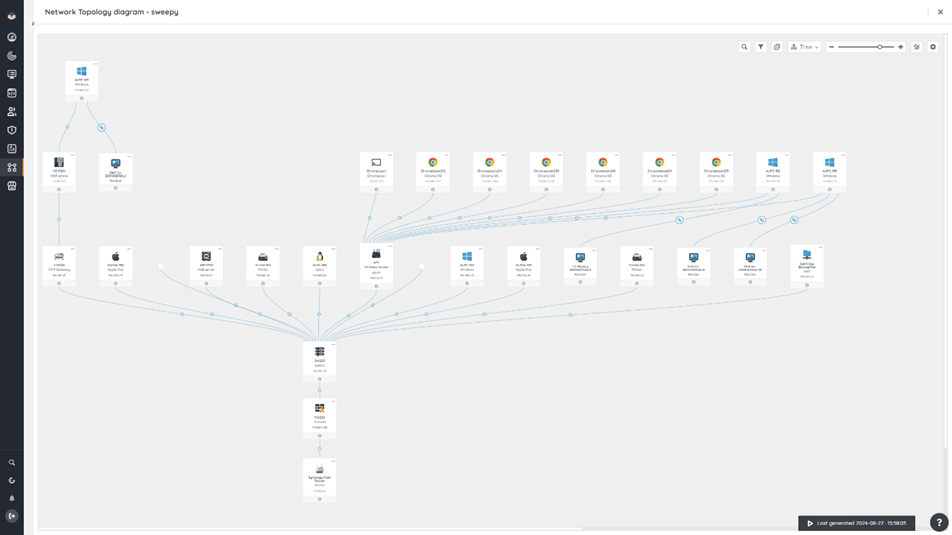
For a more visual approach, you can use network diagrams. These diagrams create a visual representation of your IT infrastructure with all its connections and dependencies. This information is invaluable when determining the potential impact of a security breach, letting you pinpoint critical assets and high-risk areas as well as potential pathways for lateral movement. This visual approach doesn’t just help you identify vulnerabilities but also helps you visualize how ransomware could propagate through your network, so you can prioritize your mitigation and remediation efforts more effectively.
Mitigate
Now that you know where to focus your efforts, it’s time to start the mitigation. Lansweeper’s Risk Insights can once again help you mitigate ransomware risks by providing both patch information and official references for each identified vulnerability. This lets your IT team know which mitigation options are readily available.
Thanks to Lansweeper’s seamless integration into your tech stack, you can also use Lansweeper’s comprehensive asset data and insights to fuel automations, workflows, and tools used in vulnerability and risk management processes, for an even better, faster, and more reliable risk response. For ransomware scenarios specifically, Lansweeper can trigger specific workflows or automations in ITSM or CMDB tools as soon as a risk is identified, streamlining your response efforts and improving the overall risk management process to prevent or limit ransomware impacts.
One thing you want to have in working order if you do find yourself the victim of a ransomware attack is your backup and recovery solutions. Lansweeper helps you ensure that these are consistently implemented across all devices. Thanks to custom reports, based on detailed data collection, you can audit devices for compliance with your company’s ransomware protection policies. Track critical details such as encryption status, system configurations, and software versions with Lansweeper to ensure that all devices meet compliance standards for ransomware prevention.
Track
A combination of continuous agentless and agent-based, active and passive scanning ensures that Lansweeper has an up-to-date inventory of your technology asset data at all times. Any mitigation or remediation efforts you take will automatically be reflected across all dashboards, views, and reports. This ensures that all changes are tracked and you have an accurate overview of your mitigation efforts.
The same goes for any tools that integrate with Lansweeper for their asset data. This information will automatically update so that you always have a comprehensive and current view of your cybersecurity status, which can then be shared with internal stakeholders to keep them informed on progress and actions taken against ransomware threats.
Take Control and Stay Ahead of Ransomware Threats
Ransomware continues to evolve, growing in both complexity and impact. As demonstrated by the recent attack on Halliburton, ransomware gangs are deploying increasingly sophisticated methods to cause maximum disruption. Organizations need to follow by adapting and strengthening their cybersecurity measures continuously.
Lansweeper’s unrivaled asset discovery and insights help you identify any vulnerabilities that could expose your network to ransomware attacks. Furthermore, its many features help you prioritize and track your mitigation efforts. Its comprehensive asset visibility, Risk Insights, and custom reporting let you uncover and prioritize high-risk vulnerabilities. By integrating seamlessly into your tech stack, Lansweeper supports proactive risk management so that your organization remains resilient in the face of evolving ransomware threats. Stay one step ahead of cybercriminals with Lansweeper.