Operational technology (OT) is everywhere – in manufacturing facilities, industrial complexes, stores, and construction sites. Not only does it power a range of industrial and operational systems, but it also works behind the scenes at organizations in nearly every industry, keeping the lights on and the water running – and it runs 24/7.
Some examples of OT include:
- PLC: Programmable Logic Controllers
- SCADA: Supervisory control and data acquisition
- DCS: Distributed Control Systems
- CNC: Computer Numerical Control Systems, including computerized machine tools
- BMS/BAS: Building Management and Building Automation Systems
- Lighting controls both for internal and external applications
- Energy monitoring, security, and safety systems for the built environment
In the past, much of the operational technology in an organization was isolated from the corporate network. It used proprietary control protocols, a proprietary OS, and specialized hardware to function.
All that’s changed.
Today, operational technology is often bridged into corporate networks using common internet protocols, and much of it consists of general-purpose hardware running mainstream operating systems. The IT-OT convergence has introduced increased risk that cannot be ignored.
The Growing Threat of OT Cybercrime
Incidents such as Stuxnet and the Colonial pipeline highlighted the importance of Operational Technology Cybersecurity – the Stuxnet worm infected over 20,000 devices in 14 Iranian nuclear facilities and ruined around 900 centrifuges, while the attack on the Colonial pipeline resulted in $90 million in financial losses.
Then in 2022, Russia-linked threat actor Sandworm targeted a Ukrainian critical infrastructure organization, infiltrating the operational technology (OT) environment via a hypervisor that managed a supervisory control and data acquisition(SCADA) system for the organization’s substation. Indications of lateral movement suggest that the attacker could have accessed the SCADA system for as long as three months.
Threats such as these will continue to be a concern, particularly for organizations in charge of critical infrastructure that houses sensitive and confidential data. Meanwhile, evolving cybersecurity regulations are putting pressure on cybersecurity professionals to ensure compliance across the entire technology estate – OT included.
With all that’s at stake, technologies and processes for increasing OT visibility are essential – you can’t protect, update or manage devices you don’t know you have. Unfortunately, those responsible for keeping all of the OT up and running often don’t have complete visibility into their hardware and software – and therefore cannot maintain, update, or replace it when needed. Decades-old technology can linger in the OT environment, outdated and unprotected.
Not only can outages impact business continuity and cause financial losses, but these devices are also sitting ducks for cybercriminals.
OT Asset Management Enables Proactive Protection
With Operational Technology Asset Management – a complete inventory of all operational technology assets, organizations can map possible attack vectors to secure their business better and create up-to-date, accurate, and in-depth reporting on all technology assets in the business.
The goal is to create a list of all OT assets and keep it up to date, reducing workload through preventive maintenance and protecting assets through the timely discovery of asset vulnerabilities. Devices that receive updates and maintenance also run more efficiently and reduce the risk of production outages.
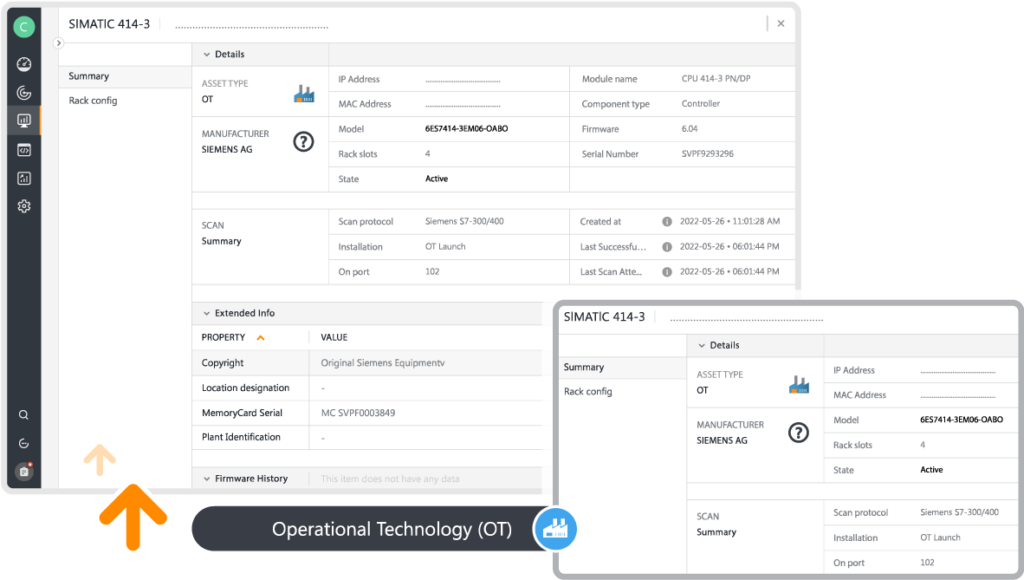
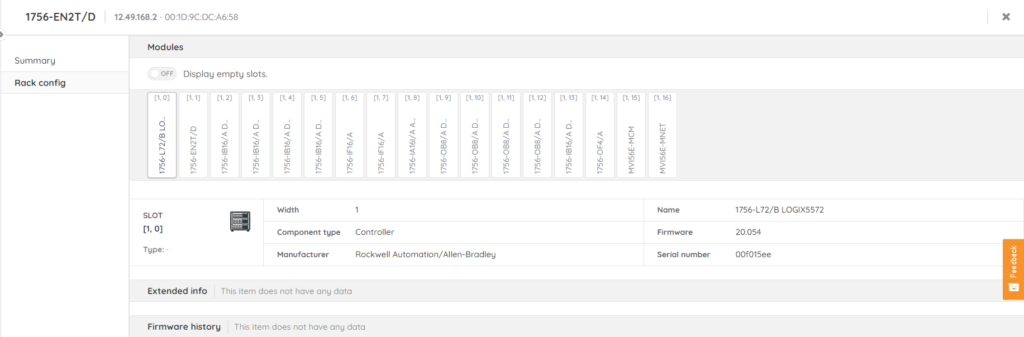
Creating an accurate OT inventory that includes comprehensive data is the first step toward enhancing the cybersecurity of OT environments. Here’s why:
- Visibility and Awareness: Maintaining a detailed inventory ensures that security teams have a complete understanding of what devices are present in the network, including their types, models, software versions, and configuration settings. This level of detail is essential for identifying which systems might be vulnerable to specific types of threats or attacks.
- Vulnerability Management: With a clear inventory, organizations can more effectively monitor for vulnerabilities specific to the devices and software within their OT networks. This information helps prioritize which systems need urgent patches or other security measures, facilitating a targeted approach to mitigating risks.
- Risk Assessment and Management: Detailed OT data allows organizations to perform more accurate risk assessments by correlating known vulnerabilities with the criticality of each asset. Understanding how each part of the OT network interacts with others and the potential impact of its compromise can help in crafting layered defense strategies tailored to specific risk profiles.
- Incident Response and Recovery: In the event of a security incident, having up-to-date and detailed information about the OT environment can speed up the response and recovery process. Teams can quickly identify affected systems, understand their role within the broader network, and apply the necessary remediations or workarounds to minimize downtime and impact.
- Regulatory Compliance and Reporting: Many industries with OT environments are subject to strict regulatory requirements regarding cybersecurity. An accurate inventory helps with compliance by providing necessary documentation of security practices and controls. It also simplifies reporting and audits by providing clear data on the security posture and actions taken to secure assets.
- Segmentation and Network Management: Knowing exactly what devices are in the OT environment supports the implementation of network segmentation strategies. Segmentation is critical in OT for isolating sensitive systems and limiting the spread of potential intrusions. Detailed inventory data helps determine the best ways to segment networks to reduce cyber risks effectively.
Lansweeper offers an effective solution to address these challenges and optimize the security of operational technology environments.
Protecting Your OT Infrastrucutre
Lansweeper’s for OT enables organizations to create up-to-date, accurate, and in-depth inventory and vulnerability reports on their OT assets using a new type of scanning called “selective scanning,” designed specifically for OT environments. Selective scanning combines the strengths of active and passive scanning to optimize security without disrupting operations.
Active scanning probes network devices to gather detailed information but can be intrusive, while passive scanning monitors network traffic non-intrusively but might miss non-communicative devices. By contrast, selective scanning tailors the approach based on the sensitivity and needs of different network segments, employing active scans during low-risk times and passive scans for critical areas. This method enhances security measures by adjusting to the specific requirements and vulnerabilities of the OT network.
Q&A Session on OT
Get all your questions answered by our experts!
Listen to this on-demand playback of an informative Q&A session on OT.
WATCH NOWLansweeper leverages unique OT protocols to perform selective scanning and identify OT devices from popular manufactures such as Siemens, Rockwell Automation, Mitsubishi Electric, Schneider Electric and more. It compiles a complete and accurate inventory of all OT devices across the business, enabling operational technology security professionals to plan and manage updates and maintenance, remediate any vulnerabilities, and have complete visibility of the expanding and increasingly diverse technology landscape.
For a complete understanding of the level of visibility Lansweeper’s new OT Discovery tool surfaces, watch the OT Demo. If you want to get started directly, it’s easy to download and set up the new Lansweeper for OT installer.