
Dell’s SupportAssist package strikes again with a new vulnerability. This time the Dell SupportAssist vulnerability enables privileged remote attackers to impersonate Dell and take control of a vulnerable device’s boot process to crack OS-level security controls via the BIOSConnect feature rooted in devices’ BIOS.
⚡ TL;DR | Go Straight to the SupportAssist BIOSConnect Vulnerability Audit.
BIOSConnect Flawed
This time the vulnerability lies within BIOSConnect, part of the SupportAssist package. It provides remote firmware update and OS recovery features to Dell computers. By taking advantage of the vulnerability attackers can take control of the device’s boot process and subvert the operating system and higher-layer security controls. However, since it is part of the Dell BIOS, simply removing SupportAssist will not help.
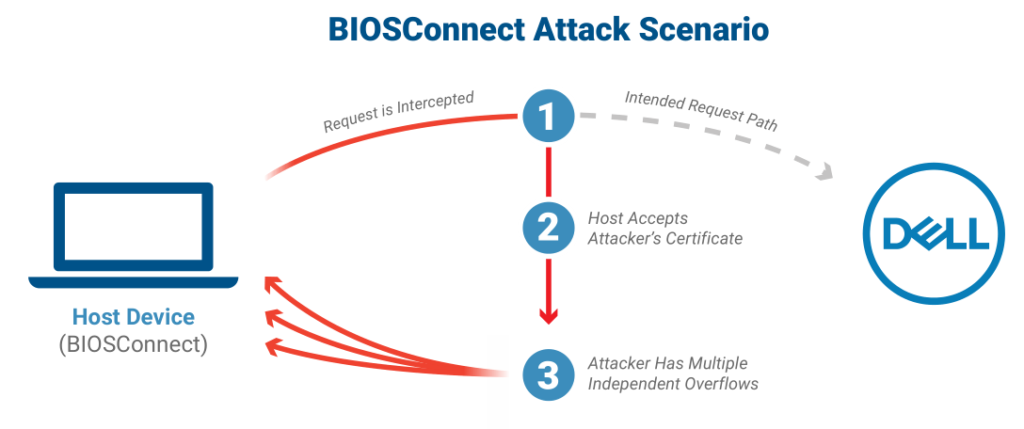
The vulnerability consists of one TLS connection issue from the BIOS to DELL (tracked as CVE-2021-21571) followed by three overflow vulnerabilities (CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574). It affects 129 Dell models of consumer and business laptops, desktops, and tablets, including devices protected by Secure Boot and Dell Secured-core PCs.
Want to run this Audit Report?
Start your Free Lansweeper Trial to run the Audit Report.
Try for FreeSupportAssist Plagued With Vulnerabilities
Dell’s SupportAssist is quickly becoming a favorite for people trying to breach corporate security systems. Not only does Dell pre-install this software on all of its Windows devices, but it is also frequently found to contain vulnerabilities like the DLL hijacking vulnerability and a previous RCE vulnerability.
Audit Your IT Environment
Find out if you have any of the 129 Dell models in your IT environment along with the current BIOS version they are running and whether you still need to update them.