⚡ TL;DR | Go Straight to the Fortinet Vulnerability Report
Fortinet has released a number of emergency patches in response to a critical heap-based buffer overflow bug in FortiOS SSL-VPN. They are already aware of this vulnerability being exploited in the wild. An unauthenticated attacker could exploit the bug to execute arbitrary code. This could in turn lead to system crashes or allow a malicious actor to install programs, compromise critical data, or create new accounts with full user rights.
CVE-2022-42475
Fortinet’s security advisory describes the vulnerability tracked as CVE-2022-42475 as «A heap-based buffer overflow vulnerability [CWE-122] in FortiOS SSL-VPN» which could allow a remote unauthenticated attacker to execute arbitrary code or commands via specifically crafted requests. The vulnerability received a critical CVSS score of 9.3.
The advisory also mentions that Fortinet is aware of the vulnerability being exploited in the wild. They advise all users to validate their systems for a number of indicators of compromise:
- Multiple log entries with:
Logdesc="Application crashed" and msg="[...] application:sslvpnd,[...], Signal 11 received, Backtrace: [...]“ - Presence of the following artifacts in the filesystem:
/data/lib/libips.bak/data/lib/libgif.so/data/lib/libiptcp.so/data/lib/libipudp.so/data/lib/libjepg.so/var/.sslvpnconfigbk/data/etc/wxd.conf/flash - Connections to the following suspicious IP addresses from the FortiGate:
188.34.130.40:444103.131.189.143:30080,30081,30443,20443192.36.119.61:8443,444172.247.168.153:8033
Protect Vulnerable Fortinet Devices
CVE-2022-42475 affects several versions of FortiOS and FortiOS-6K7K. In order to protect your devices from attackers, they should be updated to the patched versions as soon as possible. You can find a list of all affected versions and the patched versions below.
| Product | Affected Versions | Update to |
| FortiOS | 7.2.0 through 7.2.2 | 7.2.3 or above |
| 7.0.0 through 7.0.8 | 7.0.9 or above | |
| 6.4.0 through 6.4.10 | 6.4.11 or above | |
| 6.2.0 through 6.2.11 | 6.2.12 or above | |
| FortiOS-6K7K | 7.0.0 through 7.0.7 | 7.0.8 or above |
| 6.4.0 through 6.4.9 | 6.4.10 or above | |
| 6.2.0 through 6.2.11 | 6.2.12 or above | |
| 6.0.0 through 6.0.14 | 6.0.15 or above |
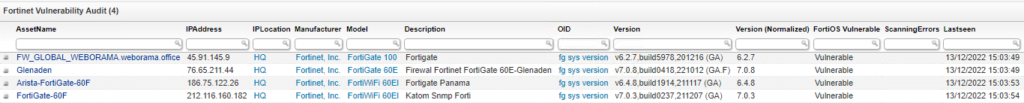
Discover Vulnerable Fortinet Devices
Our team at Lansweeper has created a special report, to help you find any Fortinet devices in your network that may be vulnerable to the vulnerability described above. The report will give you an actionable list of devices that may still need to be updated.