⚡ TL;DR | Go Straight to the Zyxel Vulnerability Audit Report
Zyxel has released patches for some of their access points and security router versions in response to an operating system command injection vulnerability. When exploited this vulnerability would allow an unauthenticated attacker to execute OS commands which could compromise the hosting server. Users are advised to install the patches as soon as possible.
Zyxel Vulnerability CVE-2024-7261
The vulnerability tracked as CVE-2024-7261 is an operating system (OS) command injection vulnerability with a critical CVSS score of 9.8. The vulnerability affects several access point and security router versions, listed below. Zyxel’s security advisory describes the vulnerability as «The improper neutralization of special elements in the parameter “host” in the CGI program of some AP and security router versions could allow an unauthenticated attacker to execute OS commands by sending a crafted cookie to a vulnerable device.»
Update Vulnerable Zyxel Access Points and Security Routers
OS command injection vulnerabilities can lead to the hosting server being compromised, allowing an unauthorized attacker to execute OS system commands. Users are advised to update devices as soon as possible. The table below lists all affected models and versions, as well as the available patches.
| Product | Affected Model | Affected Version | Patch Availability |
| Access point | NWA50AX | 7.00(ABYW.1) and earlier | 7.00(ABYW.2) |
| NWA50AX PRO | 7.00(ACGE.1) and earlier | 7.00(ACGE.2) | |
| NWA55AXE | 7.00(ABZL.1) and earlier | 7.00(ABZL.2) | |
| NWA90AX | 7.00(ACCV.1) and earlier | 7.00(ACCV.2) | |
| NWA90AX PRO | 7.00(ACGF.1) and earlier | 7.00(ACGF.2) | |
| NWA110AX | 7.00(ABTG.1) and earlier | 7.00(ABTG.2) | |
| NWA130BE | 7.00(ACIL.1) and earlier | 7.00(ACIL.2) | |
| NWA210AX | 7.00(ABTD.1) and earlier | 7.00(ABTD.2) | |
| NWA220AX-6E | 7.00(ACCO.1) and earlier | 7.00(ACCO.2) | |
| NWA1123-AC PRO | 6.28(ABHD.0) and earlier | 6.28(ABHD.3) | |
| NWA1123ACv3 | 6.70(ABVT.4) and earlier | 6.70(ABVT.5) | |
| WAC500 | 6.70(ABVS.4) and earlier | 6.70(ABVS.5) | |
| WAC500H | 6.70(ABWA.4) and earlier | 6.70(ABWA.5) | |
| WAC6103D-I | 6.28(AAXH.0) and earlier | 6.28(AAXH.3) | |
| WAC6502D-S | 6.28(AASE.0) and earlier | 6.28(AASE.3) | |
| WAC6503D-S | 6.28(AASF.0) and earlier | 6.28(AASF.3) | |
| WAC6552D-S | 6.28(ABIO.0) and earlier | 6.28(ABIO.3) | |
| WAC6553D-E | 6.28(AASG.2) and earlie | 6.28(AASG.3) | |
| WAX300H | 7.00(ACHF.1) and earlier | 7.00(ACHF.2) | |
| WAX510D | 7.00(ABTF.1) and earlier | 7.00(ABTF.2) | |
| WAX610D | 7.00(ABTE.1) and earlier | 7.00(ABTE.2) | |
| WAX620D-6E | 7.00(ACCN.1) and earlier | 7.00(ACCN.2) | |
| WAX630S | 7.00(ABZD.1) and earlier | 7.00(ABZD.2) | |
| WAX640S-6E | 7.00(ACCM.1) and earlier | 7.00(ACCM.2) | |
| WAX650S | 7.00(ABRM.1) and earlier | 7.00(ABRM.2) | |
| WAX655E | 7.00(ACDO.1) and earlier | 7.00(ACDO.2) | |
| WBE530 | 7.00(ACLE.1) and earlier | 7.00(ACLE.2) | |
| WBE660S | 7.00(ACGG.1) and earlier | 7.00(ACGG.2) | |
| Security Router | USG LITE 60AX | V2.00(ACIP.2) | V2.00(ACIP.3) (updated by cloud) |
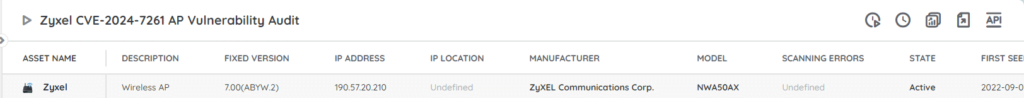
Find Vulnerable Zyxel Devices
To help you mitigate the risk of this vulnerability as soon as possible, we’ve added a new report to Lansweeper that lists all vulnerable Zyxel products along with details like the model, description, location, and more. This way you have an actionable list of devices that might require a patch.