Malicious Corona Virus Mobile App Audit
Security SoftwareFind Mobile Devices With Potential Malicious Applications
The COVID-19 crisis has also had an affect on the mobile application stores. While it is known that malicious actors try to fool users into download their malicious apps that closely resemble popular real apps, there has been a steep increase in COVID-19 or Corona related apps. While most of these apps might be innocent, it is best to stay vigilant and ensure that you double check apps that use this health crisis as a way to promote themselves. It has been reported not all of these apps have your best interest in mind.
Lansweeper scans mobile devices applications by scanning them through Microsoft Intune or VMware Airwatch.
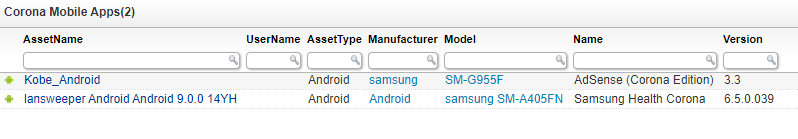
To detect whether users have a Corona related mobile application installed, the report below lists all mobile devices that have an application installed that contains the word Corona in it. This way you can double check that no malicious applications get installed on your mobile devices.
Corona Mobile Applications Query
Select Top 1000000 tblAssets.AssetID,
tblAssets.AssetName,
tsysAssetTypes.AssetTypeIcon10 As icon,
tblADusers.Username,
tsysAssetTypes.AssetTypename As AssetType,
tblIntuneDevice.Manufacturer,
tblIntuneDevice.Model,
tblIntuneApplication.DisplayName as Name,
tblIntuneApplication.Version
From tblAssets
Inner Join tsysAssetTypes On tsysAssetTypes.AssetType = tblAssets.Assettype
Inner Join tblAssetCustom On tblAssetCustom.AssetID = tblAssets.AssetID
Inner Join tblState On tblState.State = tblAssetCustom.State
Inner Join tblIntuneDevice On tblIntuneDevice.AssetId = tblAssets.AssetID
Left Join tblADusers On Lower(tblIntuneDevice.EmailAddress) In
(Lower(tblADusers.email), Lower(tblADusers.UPN))
Inner Join tblIntuneDeviceApplication On tblIntuneDevice.Id =
tblIntuneDeviceApplication.IntuneDeviceId
Inner Join tblIntuneApplication On tblIntuneApplication.Id =
tblIntuneDeviceApplication.IntuneApplicationId
Where tblIntuneApplication.DisplayName Like '%Corona%' And
tblState.Statename = 'Active'
UNION ALL
Select Top 1000000 tblAssets.AssetID,
tblAssets.AssetName,
tsysAssetTypes.AssetTypeIcon10 As icon,
tblADusers.Username,
tsysAssetTypes.AssetTypename As AssetType,
tblAirWatchDevice.Platform As Manufacturer,
tblAirWatchDevice.Model,
tblAirWatchApplication.Name,
tblAirWatchApplication.Version
From tblAssets
Inner Join tsysAssetTypes On tsysAssetTypes.AssetType = tblAssets.Assettype
Inner Join tblAssetCustom On tblAssetCustom.AssetID = tblAssets.AssetID
Inner Join tblState On tblState.State = tblAssetCustom.State
Inner Join tblAirWatchDevice On tblAirWatchDevice.AssetId = tblAssets.AssetID
Inner Join tblAirWatchApplication On tblAirWatchApplication.AirWatchDeviceId =
tblAirWatchDevice.AirWatchDeviceId
Left Join tblADusers On Lower(tblAirWatchDevice.UserEmailAddress) In
(Lower(tblADusers.email), Lower(tblADusers.UPN))
Where tblAirWatchApplication.Name Like '%Corona%' And tblState.Statename = 'Active'