Ryuk Ransomware Audit
Security VulnerabilityFind Windows Devices Infected by Ryuk Ransomware
The Ryuk ransomware is one of the many ransomware out there. Similar to all others of its kind, it usually enters the network by enticing a user to click a malicious link or download a malicious file. Once inside your network, it will try to spread, encrypt and lock devices until a ransom is paid for an encryption key. That’s why we created the Ryuk ransomware audit to keep your IT environment safe.
The Ryuk ransomware is known to place a text file in every folder once it starts encrypting files and folders. With Lansweeper’s file scanning you can scan any directory (since it will put the text file in all folders) to detect quickly if one of your machines is being encrypted. However, once the ransom note has been detected, it is usually already too late. To try and detect Ryuk earlier, we can utilize a registry scan to check if a registry key commonly created and used by Ryuk is present on a machine. This way you might be able to stop it from encrypting or spreading throughout your network.
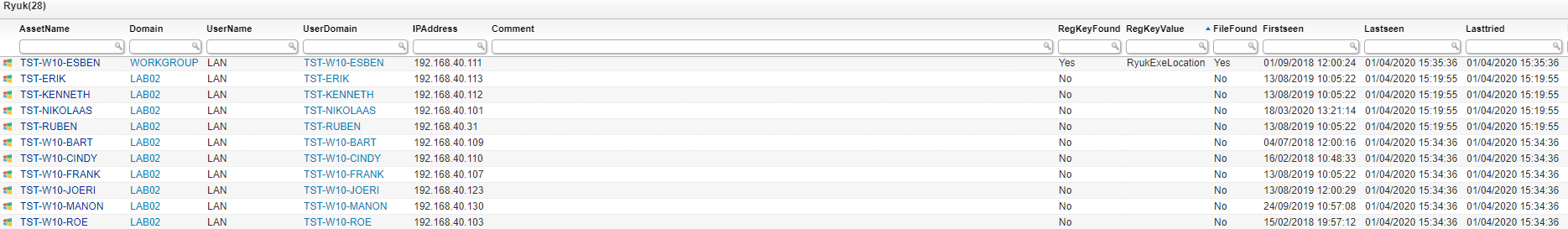
The Ryuk ransomware audit below will provide you an overview of your assets an whether the registry key or file have been found.
Ryuk Ransomware Query
Select Top 1000000 tsysOS.Image As icon,
tblAssets.AssetID,
tblAssets.AssetName,
tblAssets.Domain,
tblAssets.Username,
tblAssets.Userdomain,
tblAssets.IPAddress,
Case
When TsysLastscan.Lasttime < GetDate() -
1 Then
'Last registry scan more than 24 hours ago! Scanned registry information may not be up-to-date. Try rescanning this machine.'
End As Comment,
Case When SubQuery1.Valuename Is Not Null And SubQuery1.Valuename <> '' then 'Yes' else 'No' end as RegKeyFound,
SubQuery1.Value as RegKeyValue,
Subquery2.Found as FileFound,
tblAssets.Firstseen,
tblAssets.Lastseen,
tblAssets.Lasttried,
Subquery2.[Files last changed] as [FileLastScanned],
TsysLastscan.Lasttime As LastRegistryScan
From tblAssets
Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID
Inner Join tsysOS On tsysOS.OScode = tblAssets.OScode
Inner Join TsysLastscan On tblAssets.AssetID = TsysLastscan.AssetID
Inner Join TsysWaittime On TsysWaittime.CFGCode = TsysLastscan.CFGcode
Left Join (Select Top 1000000 tblRegistry.AssetID,
tblRegistry.Regkey,
tblRegistry.Valuename,
tblRegistry.Value,
tblRegistry.Lastchanged
From tblRegistry
Where tblRegistry.Regkey Like '%Software\Microsoft\Windows\CurrentVersion\Run' And
tblRegistry.Valuename = 'svchos') SubQuery1 On SubQuery1.AssetID =
tblAssets.AssetID
Left join ( Select Top 1000000 tblAssets.AssetID,
Case when tblFileVersions.Found = 1 then 'Yes' else 'No' end as Found,
tblFileVersions.FilePathfull,
tblFileVersions.FileVersion,
tblFileVersions.CompanyName,
tblFileVersions.Filesize,
tblFileVersions.Lastchanged As [Files last changed]
From tblAssets
Inner Join tblFileVersions On tblAssets.AssetID = tblFileVersions.AssetID
Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID
Inner Join tblState On tblState.State = tblAssetCustom.State
Where tblFileVersions.FilePathfull Like '%RyukReadMe%' And tblState.Statename =
'Active') as Subquery2 on Subquery2.AssetID = tblassets.AssetID
Where tblAssetCustom.State = 1 And TsysWaittime.CFGname = 'registry'
Order By tblAssets.Domain,
tblAssets.AssetName