
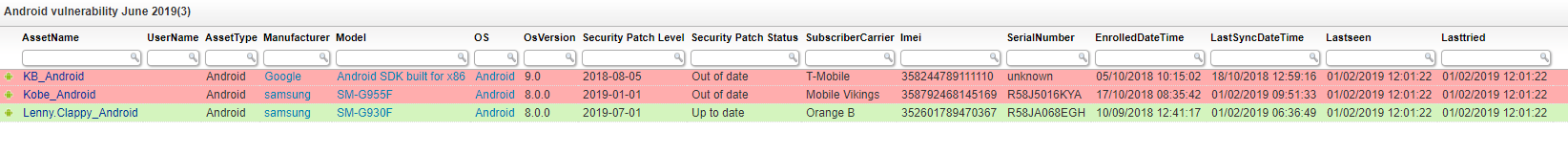
Google released a new security bulletin for 33 vulnerabilities which are being fixed with it’s latest June 2019 security update. Of the vulnerabilities, 9 have been rated as critical and should be patched as soon as possible. The custom color-coded audit below identifies mobile devices that do not have the recommend patch level as stated by the Android Security Bulletin. Ensure the cybersecurity of your IT network & update your Android’s security.
The vulnerabilities affect a wide range of Android components like the operating system itself, framework, library, media framework, Qualcomm components and Qualcomm closed-source components.
The most severe vulnerabilities reside in the media framework that could lead to arbitrary code execution using the security context of a privileged process. Currently, no active exploitation has been reported of any of the vulnerabilities. Regardless, it is highly recommended that you update to the latest security patch level. The critical severity vulnerabilities are part of the following Android components:
- Media Framework (CVE-2019-2106, CVE-2019-2107, CVE-2019-2109)
- System (CVE-2019-2111)
- Qualcomm components (CVE-2019-2308, CVE-2019-2330)
- Qualcomm closed-source components (CVE-2019-2254, CVE-2019-2322, CVE-2019-2327)
Discover Outdated Android Devices via Intune Scanning
Lansweeper scans detailed information like OS version and security path level using Microsoft Intune’s API. This gives you immediate visibility into your mobile environment in no time with the help of our built-in and custom reports.
Our custom color-coded vulnerability audit can tell you in no time which devices have an outdated security patch level and need to be patched
If you haven’t already, start your free Lansweeper trial and get a report of all vulnerable devices in no time.


