
PrintNightmare is a new bug that exposes Windows servers to remote code execution attacks through a Windows Print Spooler vulnerability that was accidentally disclosed by Microsoft in confusion with another Print Spooler vulnerability.
[update 13 august 2021] Go to the latest blog on the PrintNightmare vulnerability.
The severity of the issue is critical as threat actors can use it to take over a Windows domain server to easily deploy malware across an organization’s network. The exploit affects Windows Print Spooler which has a long history of vulnerabilities, which prompted the researchers to name it PrintNightmare. The service is enabled by default which makes it more troublesome, this also means that in theory, every Windows machine is affected.
⚡ TL;DR | Go Straight to the PrintNightmare Vulnerability Audit.
CVE-2021-34527 – Windows Print Spooler Vulnerability
The new 0-day exploit, is a Windows Print Spooler Remote Code Execution Vulnerability, just like CVE-2021-1675 was, which was patched by the latest Patch Tuesday update from June. But the new PrintNightmare exploit is apparently not fixed by the June Patch, which led to some confusion on the internet. The new CVE code is CVE-2021-34527 and contains a CVSS 3.0 score of 8.8.
Want to run this Audit Report?
Start your Free Lansweeper Trial to run the Audit Report.
Try for FreeWindows runs Print Spooler by default — including on Domain Controllers and Windows 7, 10, etc. It is also enabled on many Windows Server installations. Any user that can connect to your endpoint’s Spooler service, with a valid account, can cause remote code execution. Will Dormann, a Vulnerability Analyst at the CERT/CC, called on Microsoft Windows admins to treat this as a very important issue to mitigate. “If you have the “Print Spooler” service enabled (which is the default), any remote authenticated user can execute code as SYSTEM on the domain controller. Stop and Disable the service on any DC now,” Dormann said.
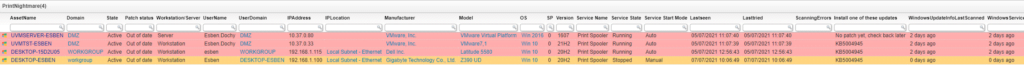
Find Domain Controllers Vulnerable to PrintNightmare
Lansweeper has prepared a special vulnerability report to find out if you have any vulnerable devices in your IT environment and whether you still need to take action to secure them. The report provides an overview of all your Domain Controllers and their Windows Print Spooler service status. Additionally, it also shows the start mode of the service. When the service is stopped and the start mode is set to Manual or Disabled, assets are considered safe.
PrintNightmare Patch Released
Microsoft released an out-of-band update for all supported Windows versions except Windows 10 version 1607, Windows Server 2016, or Windows Server 2012 on July 6. The following day, updates were released for the remaining supported Windows versions. The report has been updated so you can use it to check which machines have been updated but it continues to contain the current status of the Print Spooler service as extra information.
In addition to installing the updates, Microsoft listed the following note in regards to ensuring your systems are protected. You must confirm that the following registry settings are set to 0 (zero) or are not defined (Note: These registry keys do not exist by default, and therefore are already at the secure setting.)
- HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindows NTPrintersPointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
Additional instructions on restricting new printer driver installations to prevent future issues can be found in a newly released Microsoft KB5005010 article.
CVE-2021-34481 – PrintNightmare Continued
On July 15, Microsoft announced that not all was fixed with the Print Spooler service. Listed as CVE-2021-34481 and with a CVSS 3.0 base score of 7.8, a new vulnerability was detected in the print spooler service. This time it was an elevation of privilege vulnerability, when exploited, an attacker could run arbitrary code with SYSTEM privileges.
To prevent exploitation, Microsoft recommended disabling the Print Spooler service again until a patch was released. To help you with this process, we created a Print Spooler vulnerability report that lists all of your devices along with the status of the Print Spooler service on each device. Devices were only considered safe once the service is stopped and either in the manual or disabled start mode.
In the August patch Tuesday, Microsoft released a fix for this second Print Spooler-related vulnerability. Meaning you should be able to safely enable the print spooler service again if you wish to do so after installing the Windows updates released in August. You can find our August patch Tuesday report with the link below to check if your Windows devices have been updated to the August 2021 patch Tuesday updates.


